- Email: info@clearinfosec.com
- 1800 760 5656

In our earlier blog, we talked about how some people could misuse Google OAuth to take over someone’s session without permission. Surprisingly, this seemingly harmless part turned out to be a favorite for malware that steals information. CloudSEK found a serious problem where malware uses MultiLogin to keep control of a user’s session, even after they change their password.
This exploit, initially revealed by PRISMA on October 20, 2023, has swiftly become a tool of choice for various malware families like Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and WhiteSnake. The technical implications of this exploit are significant, challenging the security of Google’s OAuth infrastructure and highlighting the need for enhanced vigilance.
The main purpose of the MultiLogin authentication endpoint is to synchronize Google accounts across various services, particularly when users log into their accounts using the Chrome web browser. However, a detailed analysis of the Lumma Stealer code through reverse engineering has brought to light a targeted approach.
The technique focuses on the “Chrome token_service” table in WebData, extracting both tokens and account IDs associated with Chrome profiles that are currently logged in. Within this table, two critical columns stand out: service (GAIA ID) and encrypted_token. This revelation unveils a specific exploitation method used by the Lumma Stealer to gain unauthorized access to user data.
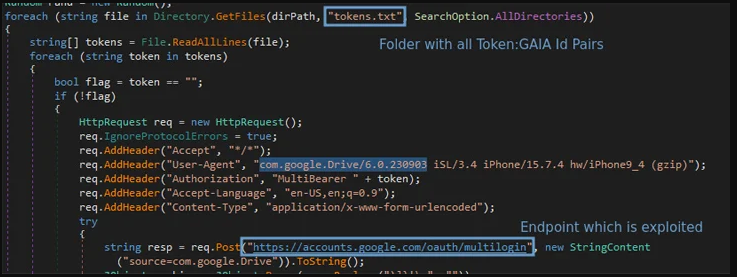
The combination of a token and GAIA ID plays a pivotal role in this exploitation. This pairing is ingeniously employed with the MultiLogin endpoint, allowing the regeneration of Google authentication cookies. Testing revealed three distinct scenarios for token-cookie generation:
In cases where the user remains logged in with the browser, the token can be utilized indefinitely, posing a serious threat to the user’s ongoing session security.
When a user opts to change their password but maintains their Google sign-in status, the token becomes a one-time use entity. This precaution prevents repeated use and ensures the security of the user’s session.
If the user chooses to sign out of the browser, the associated token is promptly revoked and deleted from the browser’s local storage. However, this token is regenerated upon subsequent login. This emphasizes the importance of vigilant log-out practices to mitigate the risk of unauthorized access.
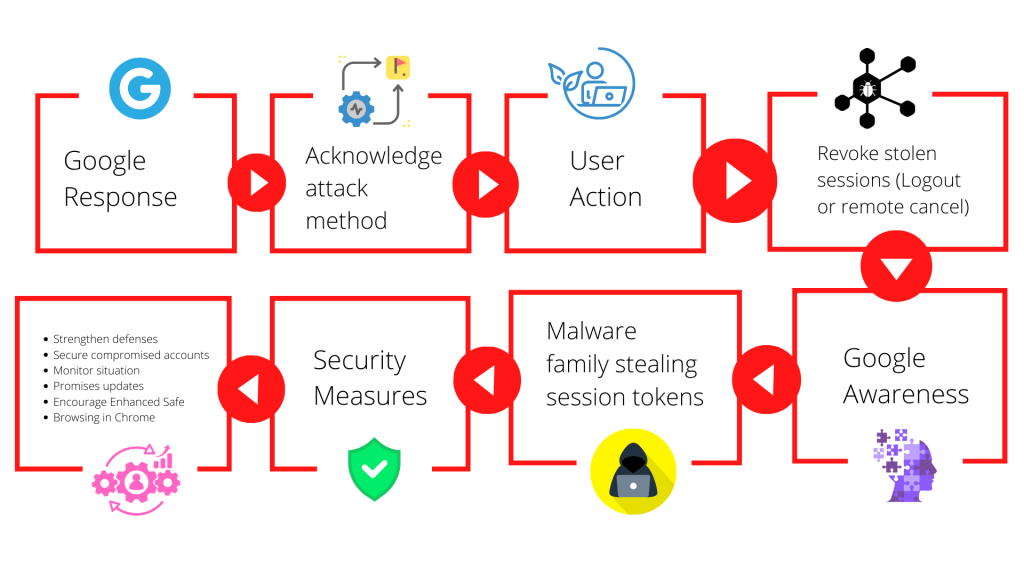
In response to queries, Google acknowledged the existence of this attack method. However, users can take control of the situation by revoking stolen sessions through a simple yet effective measure—logging out of the affected browser.
Google is aware of recent reports about a malware family swiping session tokens, as shared with The Hacker News. The company pointed out that attacks where cookies and tokens are stolen are not new, and they regularly strengthen their defenses to protect users from such malicious tactics. In response, Google has promptly taken steps to secure any compromised accounts identified.
It’s crucial to clarify a misunderstanding circulating in some reports, suggesting that users cannot cancel stolen tokens and cookies. Google corrects this, highlighting that users can make stolen sessions invalid by simply logging out of the affected browser or remotely canceling them through the user’s devices page. Google is staying vigilant, monitoring the situation closely and promising updates when necessary.
Furthermore, the company encourages users to turn on Enhanced Safe Browsing in Chrome for added protection against phishing attempts and malware downloads. This extra layer of security helps users browse the internet with increased confidence, preventing potential threats.
In response to the MultiLogin exploits, security experts emphasize the importance of changing passwords as a preventive measure. They suggests this step as a deterrent to thwart threat actors from exploiting password reset authentication flows to regain unauthorized access.
Additionally, users are advised to actively monitor their account activity, particularly scrutinizing sessions originating from unfamiliar IPs and locations, which could signal suspicious behavior.
The significance of Google’s clarification on the situation is underscored by Alon Gal, the co-founder and chief technology officer of Hudson Rock. Notably, Gal had previously disclosed details of the exploit last year. While acknowledging the value of Google’s security measures, he sheds light on the sophistication of the exploit, signaling a potential challenge to traditional methods of securing accounts.
Gal advocates for the adoption of more advanced security solutions, especially in the face of evolving cyber threats, exemplified by the rising popularity of infostealers among cybercriminals. This incident serves as a reminder of the dynamic landscape of cyber threats, urging the need for continuous advancements in security protocols.
Malware using Google Multilogin exploit to maintain access despite password reset. The Hacker News. (2024, January 3). https://thehackernews.com/2024/01/malware-using-google-multilogin-exploit.html
Copyright © 2026 Clear Infosec. All Rights Reserved.