- Email: info@clearinfosec.com
- 1800 760 5656
Identify | Analyse | Mitigate
Penetration testing involves a planned cyber attack performed on an organization with skilled ethical hackers. It will be a well-planned attack performed under controlled conditions simulating a real-world attack. The test helps in finding the vulnerabilities that can be exploited and figuring out the security posture of the company. Depending upon the type of test an organization and the type of assets to which the attacks are planned, the tests performed vary.
Red Team Attack Simulation
Tests your defensive and response capabilities to a real-world attack.
By leveraging our expertise in the security domain and threat landscape, we can tailor an attack simulation that can be effective as a real-world attack. Get insights about your ability to withstand social, physical, network, and application attacks. Try every way possible to get into your systems, see whether your systems, network, apps, and workforce are impenetrable or can be manipulated.
Application Pen Test is an unavoidable part of every organization’s SDLC. Test your native applications, web applications, and their environment to build them with confidence. With Clear Infosec, Identify high-risk business vulnerabilities, such as authentication, authorization, and business logic flaws, that could lead to a data breach.
Wireless networks are an inevitable part of organizations today as it is handy to use and doesn’t consume much space. We cannot avoid the thought that it can be an entry point to bad actors as well. Test all your wireless networks, technologies, protocols, and more to find ways flaws that can lead to a data leak.
Every day, more and more companies are adopting new cloud environments to host applications and more. The entire environment is virtual and you don’t get to test everything involved. But you can test what is in your control - the services that are hosted in all types of environments (IaaS/PaaS/SaaS).
Networks connect you with others. That’s making it one of the crucial assets that can be used by a bad actor for data leaking. Test all your networks – internal and internet-facing. Find and patch the critical vulnerabilities in your network right away. Keep the bad ones' away.
People are always the weakest link in cyber security. There is an unlimited number of ways through which an employee can be manipulated by a bad actor. With Clear Infosec, check how impenetrable your people are and provide the security awareness they need.
IoT enables everything to go smart and wireless. But you must not forget that they are not smart enough to defend against any attacks. Find and patch every vulnerability in your IoT devices to make them fortified. Test all the smart devices connected to your network.
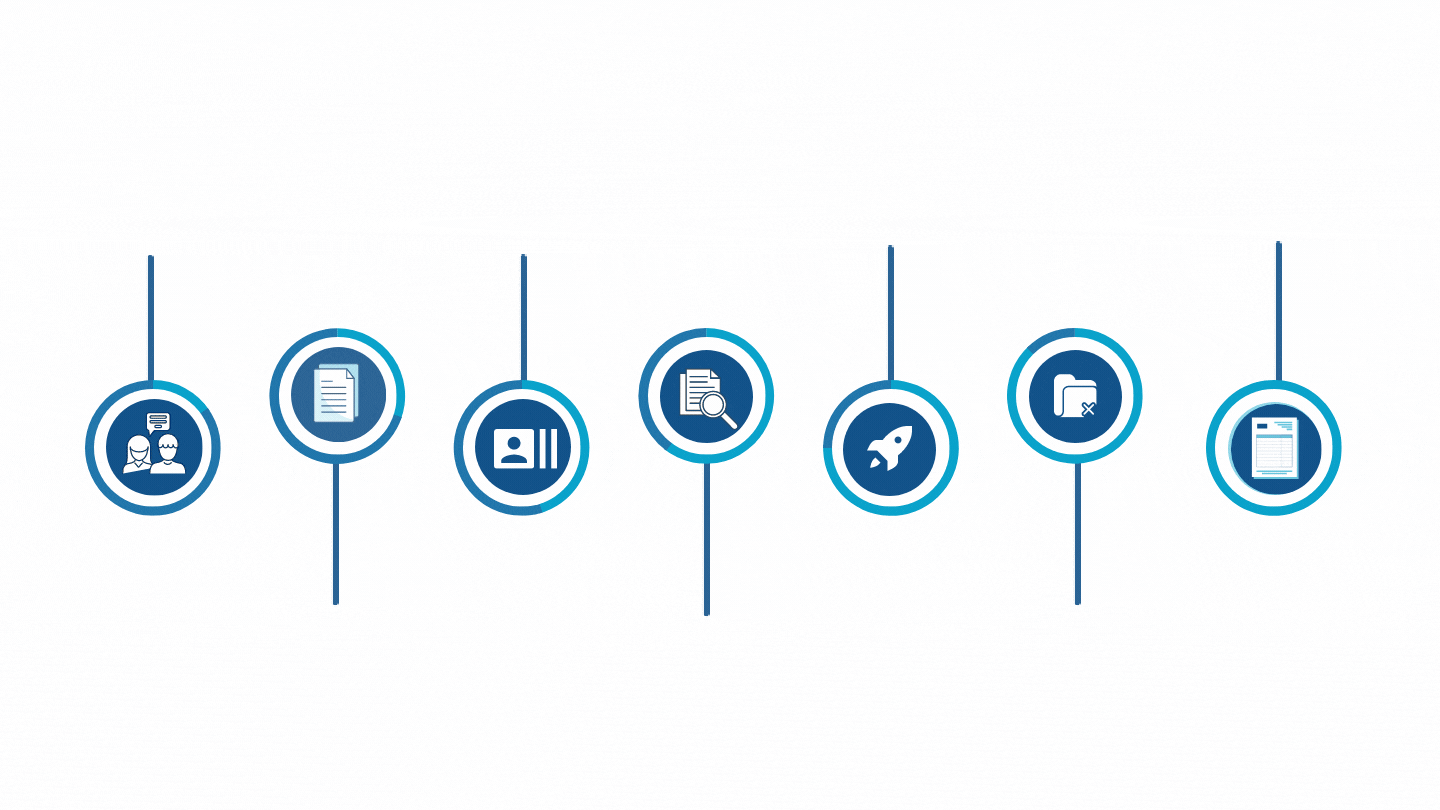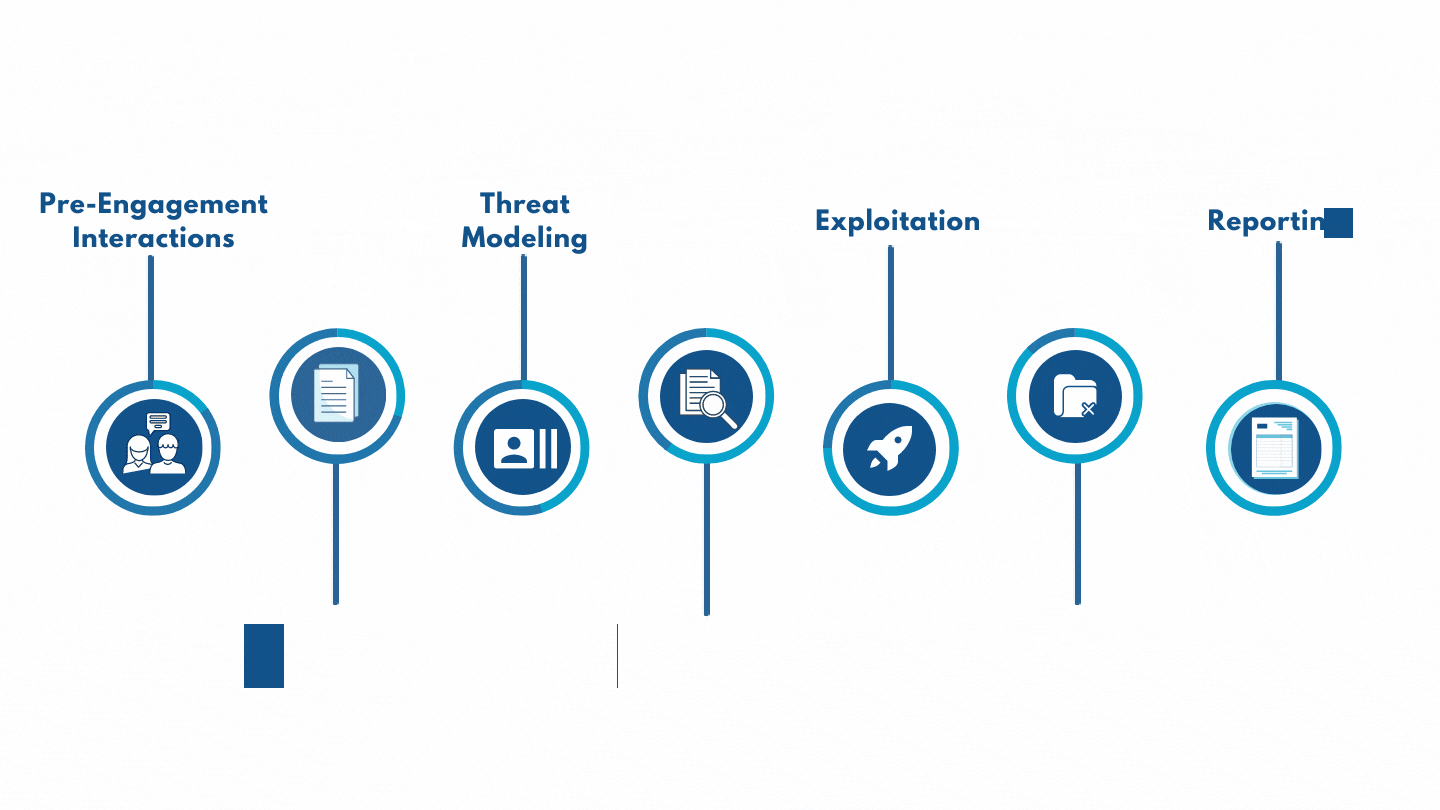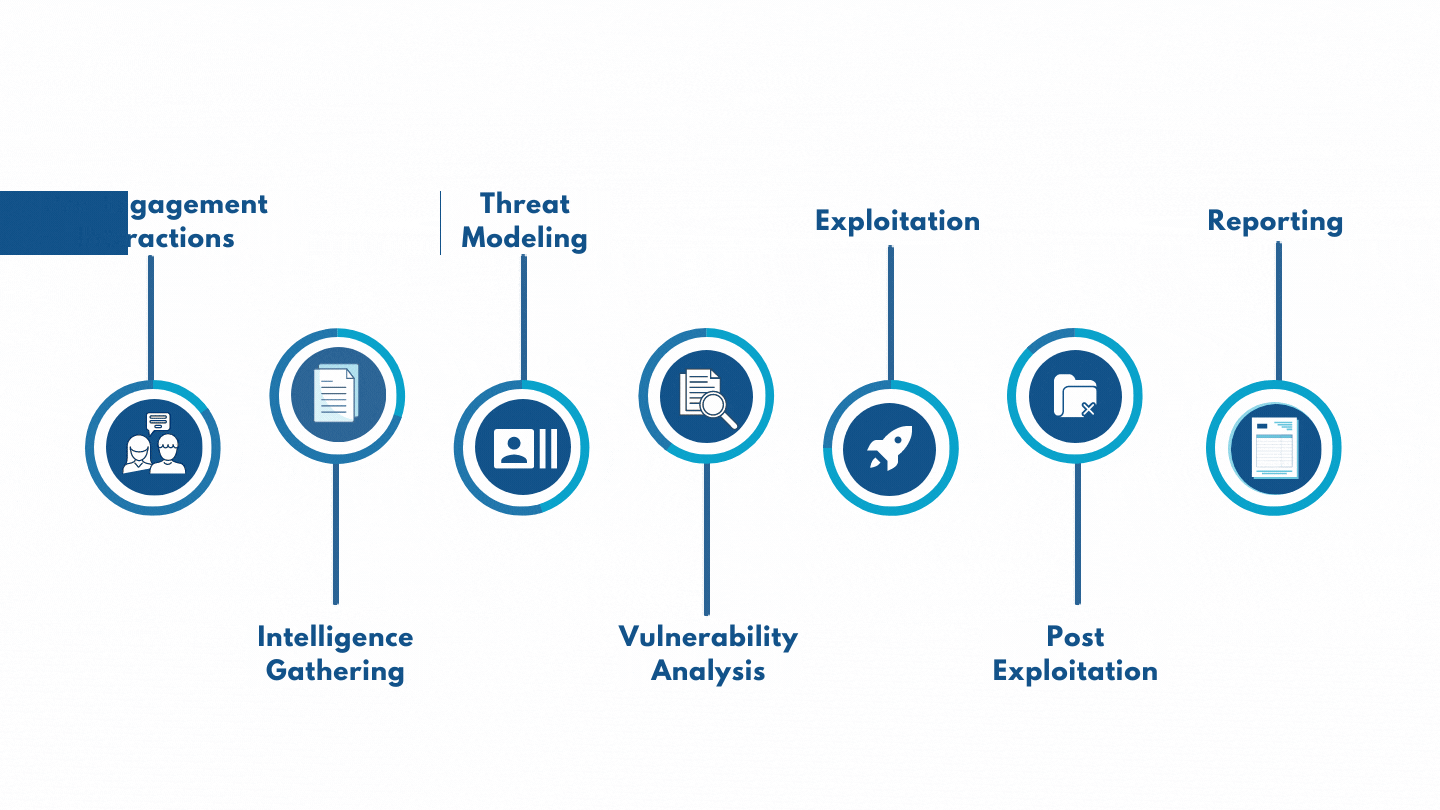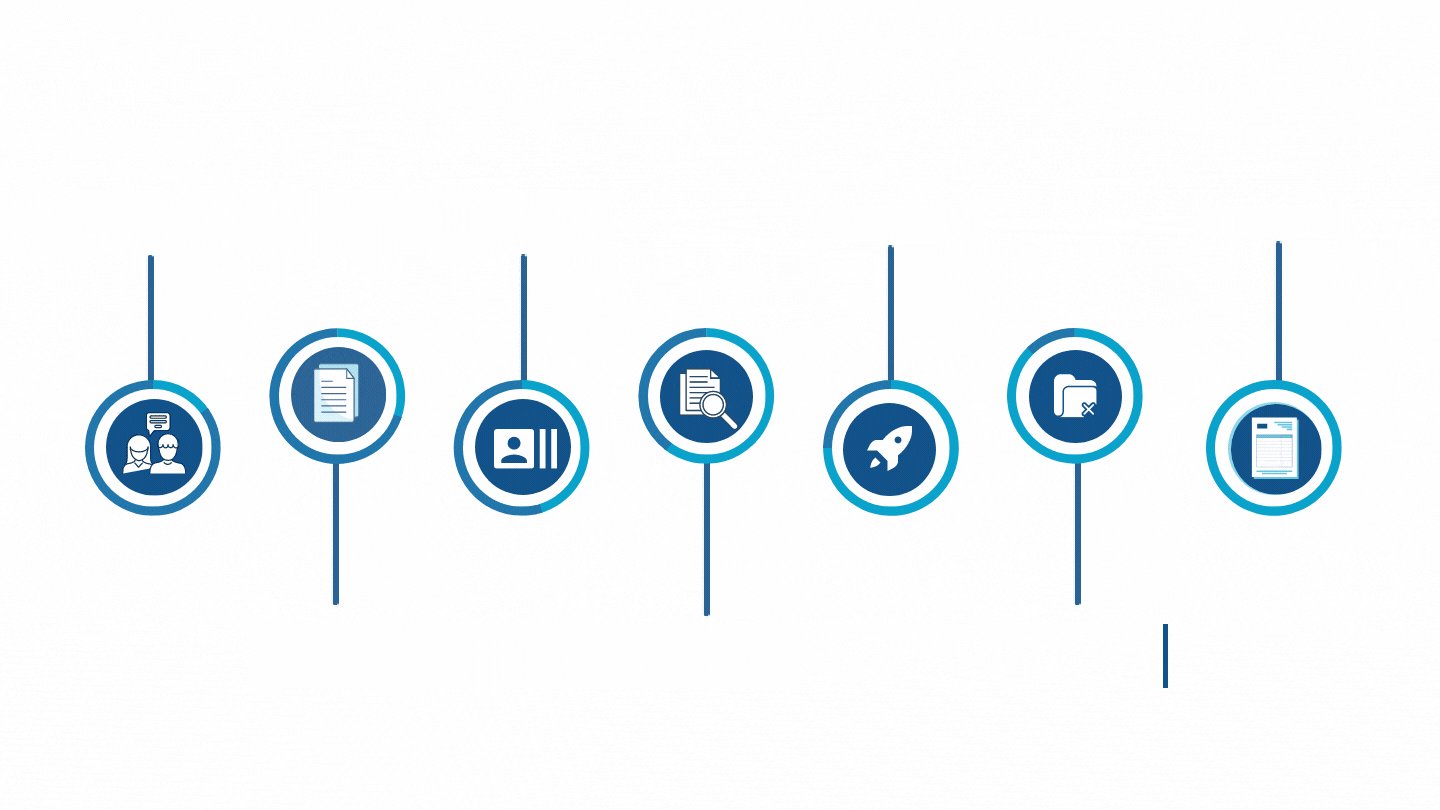
Believing and having confidence that you are secure from an attack are entirely two different things. We, Clear Infosec, intend to elevate our customers' belief into confidence and that is absolutely priceless. That confidence gives you the freedom and time to invest in improvising your business.
Our certified team of pen testers is capable of learning your infrastructure inside out in no time, finding your strengths as well as your vulnerabilities in order to help you improvise your security posture to face what tomorrow brings.
To defend against an attack, you must think like an attacker. That is why we have the best in the market pen testers with proven track records in our team. An effective pen tester is a good hacker who works for a good cause. Our testers are qualified, certified, and out-of-the-box thinkers who can unquestionably find their way in. They are the front-runners in the respective domains who have the confidence and curiosity that drive them to find even the slightest gap in security posture.
We conduct research, publish articles, machine-hack walkthroughs, contribute to infosec communities and much more to spread the awareness and knowledge that we gained over the years.
Find and Fix it
What? When? and How?
Penetration testing is never over with the submission of a list of vulnerabilities found. Knowing what to do with the list is important. That is why our penetration testing never stops with report submission and involves discussions and so even after that.
We understand that the motive behind conducting a Pen Test varies from Organization to Organization. That is why we have our team trained and skilled at various types of penetration testing. We can address any of the needs with our different penetration testing methods and stand consistent with the Industry Standards.
This is a testing type in which you provide us with no prior information about the asset and we find our ways to barging in.
Black box testing with Clear Infosec empower you with the confidence you need to release the applications and keeping away the users from deserting your apps. We help organizations to improve the security of applications, from beginning through production, combining the best-in-class personnel and technology in an effective and cost-efficient way.
To carry out this testing type, you will be requested to provide us with all the information about the assets you want us to test.
White box testing with Clear Infosec ensure you that your application is tested inside out. Our information security professionals make certain that the source code is tested as comprehensively as possible. Keeping your applications protected and providing you with feedbacks – stays as the primary goal. ALWAYS…!
For this testing type, you will be requested to provide us with some information about the asset which you want to test.
With Clear Infosec, find the flaws of your applications regardless of where they are in the Development Life Cycle. Find and fix them right away. We offer on-demand and automated security testing methods that can be effortlessly integrated into each life cycle. With less effort and cost, uncover every significant flaw.
With every passing experience, we make our Strengths stronger and Weaknesses weaker. We make this happen by adding more and more into our resources database.
We make records of every challenge we face and make it empower us to proceed in the pursuit further. You can find the best resources here in our resources section. We highly recommend that you use them for learning purposes and not for marketing or sales purposes.
Copyright © 2025 Clear Infosec. All Rights Reserved.