- Email: info@clearinfosec.com
- 1800 760 5656

In the dynamic landscape of cybersecurity, a recent revelation by threat actor “Prisma” has brought to light a significant exploit that allows the generation of persistent Google cookies through token manipulation. This discovery, highlighted by CloudSEK’s threat intelligence researcher, Pavan Karthick M, has far-reaching implications, shaping the narrative of cyber threats in recent times.
In the intricate web of online security, the emergence of novel exploits demands a closer look at their origins, mechanisms, and subsequent impact. Recently, a threat actor named “Prisma” unveiled a noteworthy exploit capable of generating persistent Google cookies through the manipulation of tokens. This revelation, as explored by CloudSEK’s Pavan Karthick M, not only underscores the evolving sophistication of cyber threats but also sheds light on the collaborative efforts within the cybersecurity community to unravel and understand these intricacies.
The journey of this exploit begins with infostealers, including Lumma and Rhadamanthys, strategically incorporating token manipulation techniques into their malware. Their goal: to create enduring Google cookies. In October, CloudSEK researchers uncover a zero-day exploit after Prisma shares information on its Telegram channel. This discovery triggers a ripple effect, as Lumma’s threat actor enhances the methodology through reverse engineering, leading to the swift integration of the exploit into the arsenals of prominent infostealers.
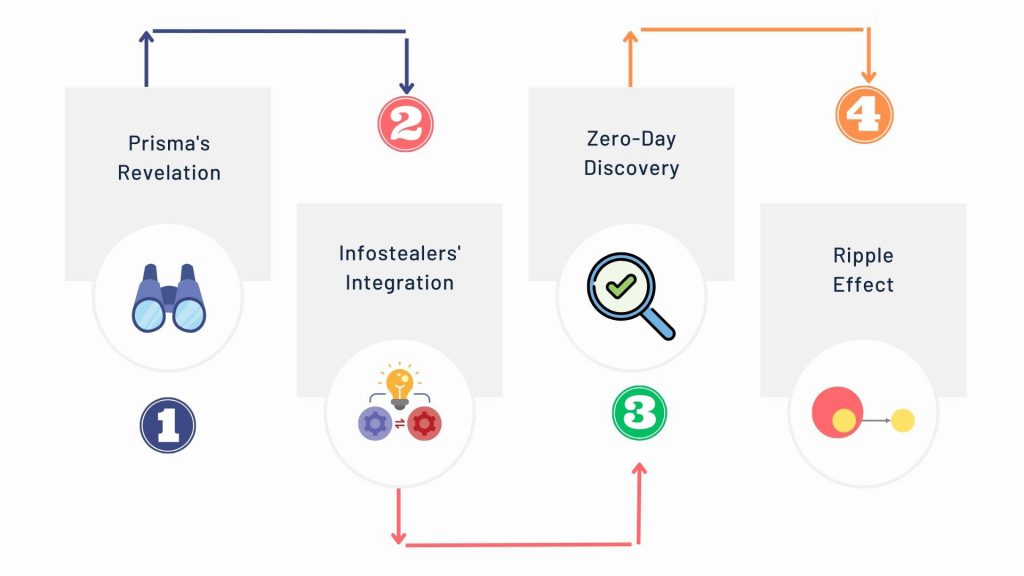
1.Prisma’s Revelation: Prisma discloses the exploit, enabling the generation of persistent Google cookies through token manipulation.
2. Infostealers’ Integration: Lumma and Rhadamanthys incorporate token manipulation into their malware, aiming to create enduring Google cookies.
3. Zero-Day Discovery: CloudSEK researchers uncover a zero-day exploit in October, triggered by Prisma’s disclosure on its Telegram channel.
4. Ripple Effect: Lumma’s threat actor enhances the methodology through reverse engineering, swiftly integrating the exploit into the arsenals of prominent infostealers.
The improved methodology marks a shift in the landscape of malware development, emphasizing the concealment and protection of exploit methodologies. Lumma’s adoption of advanced blackboxing techniques serves a dual purpose — it keeps the core mechanics of the exploit hidden, making replication challenging for other threat actors, and reduces the likelihood of triggering security alarms. This strategic move ushers in a new era where the emphasis lies not only on the effectiveness of exploits but also on their ability to remain covert.
Collaboratively, CloudSEK’s threat research team, working alongside Prisma, independently reverse engineers the malware housing the exploit. This collaboration unveils the root of the method, tracing it to an undocumented Google OAuth endpoint named “MultiLogin.” This internal mechanism, designed for synchronizing Google accounts across services, is found to have two crucial features — the persistence of a user’s Google session post-password change and the ability to generate valid cookies during a session disruption
OAuth is like a teamwork system for apps, seen in features like “Log in with Google” on websites. Its job is to get permission from users so apps can share and use their information. However, if it’s not set up correctly, it can lead to issues. Security researchers discovered problems with it on Booking.com, where it exposed the site to potential attacks. Moreover, some folks create fake apps using OAuth to target Microsoft Exchange servers. So, while OAuth is handy for making things work together, we must be cautious to ensure our online safety.
CloudSEK discovered that Prisma’s OAuth exploit, targeting Google Chrome, centers on the token_service table, holding vital details like “service (GAIA ID)” and “encrypted_token” for logged-in Chrome profiles. To obtain this information, encrypted tokens are deciphered using a unique code stored in Chrome’s Local State within the UserData directory, similar to how passwords are kept secure. By scrutinizing Chromium’s source code,
CloudSEK identified the MultiLogin endpoint as an internal tool designed to synchronize Google accounts across services, ensuring a smooth user experience by aligning browser account states with Google’s authentication cookies. Importantly, this endpoint plays a crucial role in Google’s OAuth system, managing simultaneous sessions or seamless switches between user profiles by accepting vectors of account IDs and auth-login tokens.
Lumma’s Manipulation Technique
MultiLogin, crucial for user authentication, can be misused if its cross-account communication is mishandled. CloudSEK delves into Lumma’s strategy, the first infostealer to exploit MultiLogin, to illustrate how this abuse unfolds.
Nuanced Token Manipulation
Lumma’s approach centers on manipulating the token: GAIA ID pair, a critical element in Google’s authentication. This pair, in tandem with the MultiLogin endpoint, allows the regeneration of Google service cookies. Lumma takes an extra step by encrypting this pair with private keys, effectively “blackboxing” the exploitation process, keeping its core mechanics concealed.
Purposeful Blackboxing
The blackboxing serves dual purposes: it conceals the exploit’s core mechanism, making it challenging for other threat actors to replicate. Additionally, it lowers the likelihood of triggering alarms in network security systems, as encrypted traffic tends to be overlooked by standard security protocols, often considered legitimate.
Persistent Access through Exploitation
By manipulating the token: GAIA ID pair, Lumma achieves continuous regeneration of cookies for Google services. This exploitation remains effective even after users reset their passwords, allowing for prolonged and potentially unnoticed access to user accounts and data, as observed by CloudSEK.
Lumma’s Exploit Evolution and Exposure
Lumma’s adaptation of the exploit, incorporating SOCKS proxies to bypass Google’s IP-based restrictions on cookie regeneration, inadvertently disclosed details of its techniques. This revelation opened the door for other infostealers like Rhadamanthys, Risepro, Meduza, Stealc Stealer, and, most recently on Dec. 26, White Snake, to adopt the exploit, as highlighted by CloudSEK.
CloudSEK highlights a significant shift in cyber threat tactics, exemplified by Lumma threat actors encrypting a key part of their exploit. This strategic move reflects an increased emphasis on stealth and sophistication in the realm of cyber threats.
CloudSEK underscores the need for defenders to enhance their cybersecurity strategies in response to this evolving landscape. The altered focus in malware development now prioritizes concealing and protecting exploit methodologies alongside their effectiveness. The call for organizations to adopt continuous monitoring of both technical vulnerabilities and human intelligence sources becomes crucial in staying ahead of emerging cyber threats. Karthick M emphasizes the collaborative effort between these two aspects as vital for uncovering and comprehending these increasingly sophisticated exploits.
Copyright © 2025 Clear Infosec. All Rights Reserved.