- Email: info@clearinfosec.com
- 1800 760 5656

In the vast and intricate world of cybersecurity, the discovery of novel threats often sends ripples of concern throughout the industry. One such discovery, the emergence of Loop Denial-of-Service (DoS) attacks, represents a significant milestone in the ongoing battle against cyber adversaries. These attacks, as elucidated by researchers from the esteemed CISPA Helmholtz-Center for Information Security, target application-layer protocols reliant on the User Datagram Protocol (UDP). Their findings shed light on a potentially devastating vulnerability that threatens the integrity and availability of countless hosts across the digital landscape.
At the core of this newfound threat lies a complex and sophisticated attack vector, aptly named the Loop DoS attack. Unlike conventional DoS attacks that rely on flooding targets with excessive traffic, Loop DoS attacks employ a cunning strategy that involves the perpetual exchange of messages between servers of UDP-based protocols. This insidious pairing of servers initiates an endless loop of communication, culminating in a deluge of network traffic that overwhelms the targeted systems, rendering them unresponsive and inaccessible to legitimate users.
To comprehend the vulnerability exploited by Loop DoS attacks, one must delve into the fundamental workings of the User Datagram Protocol (UDP). Unlike its counterpart, the Transmission Control Protocol (TCP), UDP lacks the mechanism for verifying the authenticity of source IP addresses. This inherent flaw makes UDP susceptible to a technique known as IP spoofing, wherein attackers manipulate packet headers to falsify the source IP address. By leveraging this vulnerability, adversaries can craft UDP packets containing forged victim IP addresses, thereby initiating a reflected denial-of-service onslaught with devastating consequences.
Building upon the foundation of UDP’s vulnerability, cybercriminals have devised a cunning ploy to exploit specific implementations of UDP-based protocols. These protocols, ranging from Domain Name System (DNS) to Network Time Protocol (NTP) and Trivial File Transfer Protocol (TFTP), unwittingly serve as conduits for orchestrating Loop DoS attacks. Through meticulous manipulation of these protocols, attackers can orchestrate a self-perpetuating loop of communication between vulnerable servers, amplifying the impact of the assault and exacerbating the challenge faced by defenders.
By dissecting the sequence of events that unfold during the execution of this attack, organizations can gain invaluable insights into its intricacies and implement targeted mitigation measures to mitigate the risk effectively. Let’s delve into the meticulous breakdown of the attack process to shed light on its modus operandi and the vulnerabilities it exploits.
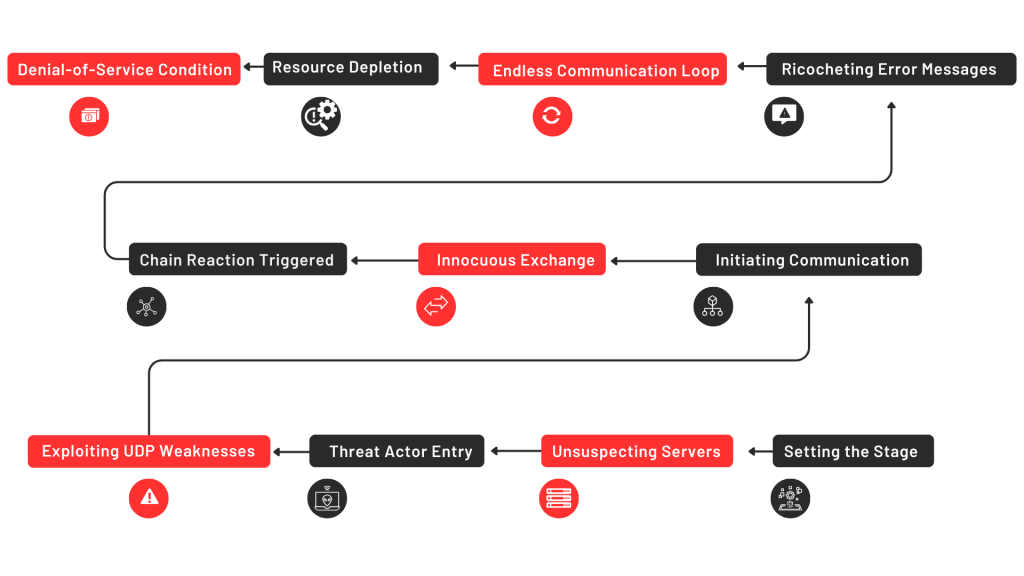
As the error messages propagate back and forth incessantly between the two servers, a cascade of consequences ensues. With each exchange, the servers unwittingly deplete their finite resources, including bandwidth, processing power, and memory. This symbiotic exchange of errors culminates in a catastrophic denial-of-service scenario, leaving the targeted services paralyzed and inaccessible to legitimate users, thus achieving the malicious objectives of the attackers.
Amidst the complexity and sophistication of Loop DoS attacks, it is essential to quantify the magnitude of the threat they pose to the digital ecosystem. According to estimates provided by CISPA, approximately 300,000 hosts and their associated networks are susceptible to exploitation through Loop DoS attacks. While empirical evidence of active exploitation may be lacking, the potential impact of this threat cannot be understated, underscoring the urgent need for proactive mitigation measures.
In the face of this looming threat, the importance of proactive mitigation measures cannot be overstated. Initiatives such as Best Current Practice 38 (BCP38), aimed at filtering spoofed traffic, assume critical significance in fortifying the resilience of network infrastructures against Loop DoS attacks and similar threats. By implementing robust defensive strategies and staying abreast of emerging vulnerabilities, organizations can bolster their defenses and mitigate the risk posed by this insidious exploit.
As the ripple effects of Loop DoS attacks reverberate across the cybersecurity landscape, it is imperative to identify and address the vulnerabilities present in affected products and manufacturers. The researchers at CISPA have identified numerous products from industry giants such as Broadcom, Cisco, Honeywell, Microsoft, MikroTik, and Zyxel that are susceptible to exploitation. This revelation underscores the urgency for stakeholders to collaborate closely with manufacturers and security experts to remediate vulnerabilities promptly and safeguard against potential exploitation.
In conclusion, the emergence of Loop DoS attacks serves as a sobering reminder of the ever-evolving nature of cyber threats and the imperative for constant vigilance. By understanding the intricacies of this threat and adopting proactive mitigation strategies, organizations can fortify their defenses and mitigate the risk posed by this insidious exploit. Let this revelation serve as a clarion call for collaboration, resilience, and unwavering commitment to cybersecurity in the face of adversity.
New “loop dos” attack impacts hundreds of thousands of systems. The Hacker News. (2024, March 20). https://thehackernews.com/2024/03/new-loop-dos-attack-impacts-hundreds-of.html
Copyright © 2026 Clear Infosec. All Rights Reserved.