- Email: info@clearinfosec.com
- 1800 760 5656

In today’s interconnected world, the threat of cyber attacks looms larger than ever before. Cybersecurity breaches have become increasingly common, with attackers continuously devising new and sophisticated methods to infiltrate systems, steal sensitive data, and disrupt operations. As organizations embrace digital transformation and rely more heavily on technology, the importance of robust cybersecurity measures cannot be overstated.
In recent months, cybersecurity researchers have raised the alarm over a surge in phishing attacks orchestrated with the aim of deploying a particularly insidious threat: StrelaStealer. These attacks have targeted over 100 organizations across the European Union and the United States, leaving a trail of compromised systems and data breaches in their wake.
At the heart of these phishing campaigns lies StrelaStealer, a sophisticated malware strain designed to infiltrate email clients, exfiltrate sensitive data, and evade detection by security software. Understanding the inner workings of StrelaStealer is essential for organizations seeking to defend against this pervasive threat.
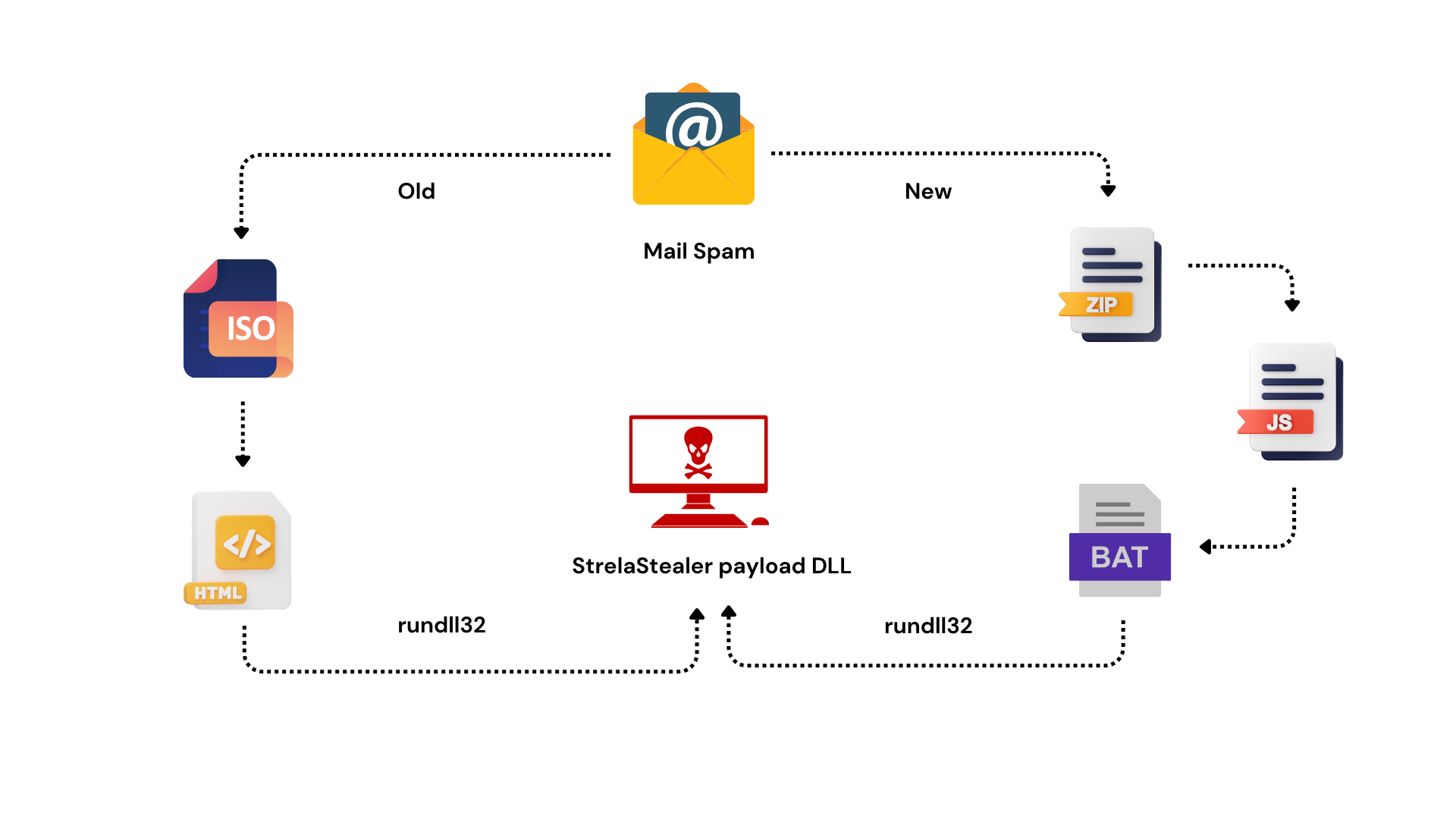
While StrelaStealer commands attention with its sophisticated capabilities, it is but one piece of a larger puzzle. The cybersecurity landscape is replete with a diverse array of threats, each presenting its own unique challenges to organizations seeking to protect their digital assets.
In the face of these ever-evolving cyber threats, organizations must adopt a proactive approach to cybersecurity to protect their digital assets and mitigate the risks posed by malicious actors.
As the digital landscape continues to evolve, organizations must remain vigilant in the face of emerging cyber threats. By understanding the tactics employed by malicious actors, implementing robust security measures, and fostering a culture of cybersecurity awareness, organizations can navigate the perilous seas of cyberspace with confidence. Together, we can build a more resilient digital ecosystem, safeguarding our data and preserving the integrity of our interconnected world.
New Strelastealer phishing attacks hit over 100 organizations in E.U. and U.S. The Hacker News. (2024b, March 23). https://thehackernews.com/2024/03/new-strelastealer-phishing-attacks-hit.html
Copyright © 2025 Clear Infosec. All Rights Reserved.