- Email: info@clearinfosec.com
- 1800 760 5656

In a groundbreaking development, the National Institute of Standards and Technology (NIST) recently unveiled version 2.0 of its renowned Cybersecurity Framework (CSF). This release, the first major update in a decade, reflects the dynamism of the digital landscape and the evolving threat landscape. Initially tailored for critical infrastructure organizations, the CSF 2.0 is now poised to become a versatile and indispensable tool for organizations of all sizes and security maturity levels.
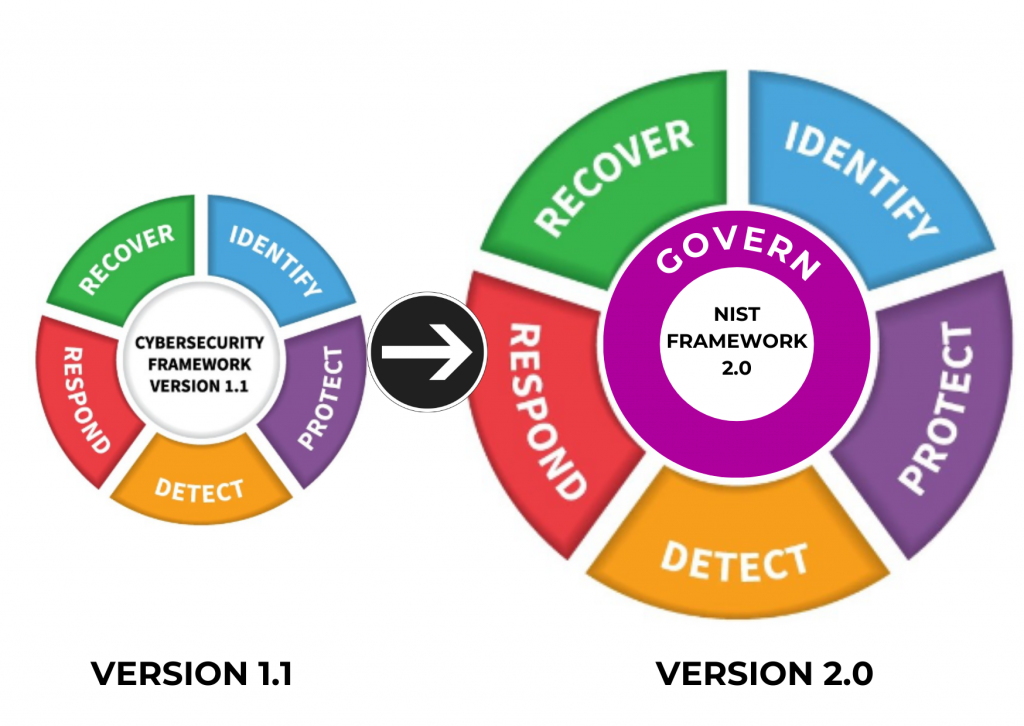
The original cybersecurity framework gained prominence by addressing the unique challenges faced by critical infrastructure entities. However, NIST recognized the broader applicability of its framework and responded by incorporating valuable feedback received during the draft phase. The result is the CSF 2.0, equipped with expanded core guidance and additional resources to empower organizations in their quest for robust cybersecurity practices.
CSF 2.0 is built on six crucial pillars, each vital for strengthening how an organization protects itself online. This update introduces the ‘Govern’ function, a critical addition that specifically addresses risk management. Experts, such as Robert Booker, Chief Strategy Officer at HITRUST, highlight the importance of adding the “Govern” function, emphasizing its key role in enhancing the overall effectiveness of the framework.
Let’s take a closer look at the new elements introduced in NIST CSF version 2.0.
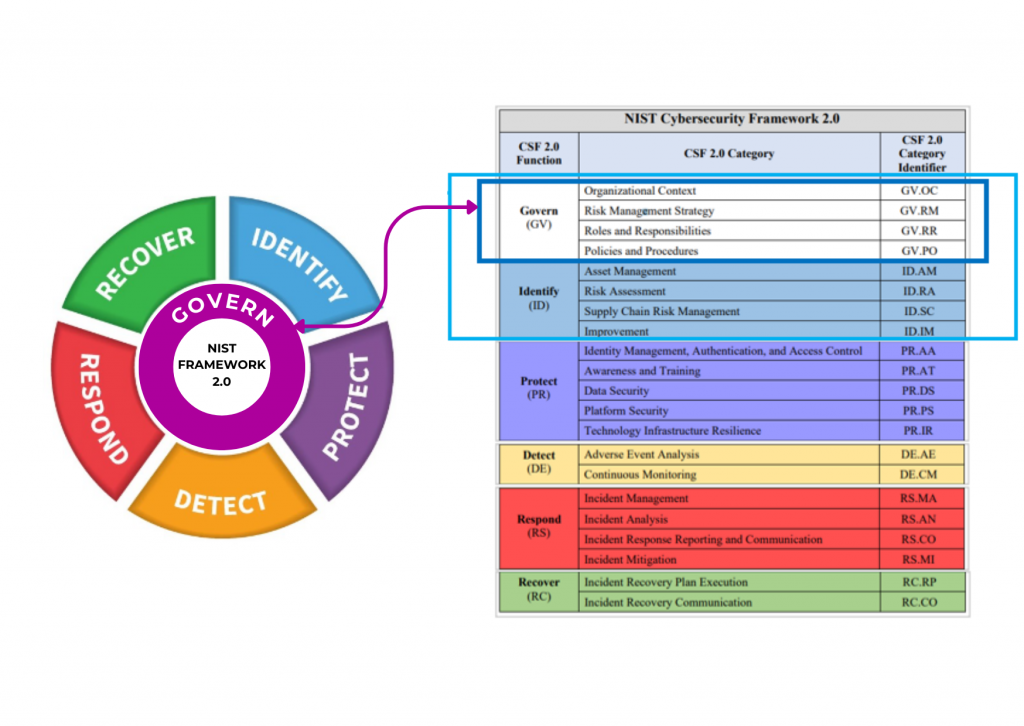
GOVERNANCE (GV): In charge of setting up and overseeing the organization’s approach to managing risks, expectations, and policies.
IDENTIFY (ID): Determining the current cybersecurity risk to the organization.
PROTECT (PR): Using protective measures to mitigate and reduce cybersecurity risks.
DETECT (DE): Finding and analyzing potential cybersecurity attacks and compromises.
RESPOND (RS): Taking action on a detected cybersecurity incident.
One distinguishing feature of CSF 2.0 is its commitment to providing practical assistance to organizations. Users are not left to navigate the framework alone; instead, they are equipped with implementation examples and quick-start guides tailored to their specific needs. The framework also offers a searchable catalog of references, allowing organizations to align their guidance with over 50 relevant cybersecurity documents. With availability in over a dozen languages, CSF 2.0 is set to become a global standard, thanks to volunteers translating it worldwide.
NIST Director Laurie E. Locascio emphasizes that CSF 2.0 is not a one-size-fits-all solution. Rather, it is a suite of resources that organizations can customize and use individually or in combination. This flexibility ensures that the framework can adapt to evolving cybersecurity needs and capabilities over time, providing enduring value to organizations.
To gauge the real-world implications of CSF 2.0, we turn to Katherine Ledesma, Head of Public Policy & Government Affairs at industrial cybersecurity firm Dragos. Her insights shed light on the specific benefits and challenges that organizations with industrial control systems (ICS) and operational technology (OT) systems may encounter. CSF 2.0 aligns with the industry-wide shift in perception. It moves the conversation from viewing cybersecurity as a mere cost center to recognizing it as an investment that not only protects but also supports business operations. This paradigm shift holds particular significance for entities relying on ICS and OT cybersecurity, such as manufacturing facilities and utility providers.
While CSF 2.0 acknowledges the broad applicability of its functions, categories, and subcategories to both IT and OT environments, Ledesma anticipates a focused effort on developing distinct approaches for ICS/OT protection. This involves continuous updates to documents like the Guide to OT Security and incorporation of specific concepts into broader planning and guidance documents.
In concluding our exploration of NIST Cybersecurity Framework 2.0, we recognize it as a pivotal milestone in the ongoing efforts to fortify digital defenses. Its versatility, practical resources, and adaptability to diverse organizational needs position it as a crucial tool in the dynamic landscape of cybersecurity. As organizations embrace this framework, the dialogue around its implementation and its impact on various sectors will undoubtedly shape the future of cybersecurity practices. NIST’s commitment to continuous improvement ensures that CSF 2.0 remains at the forefront of cybersecurity, empowering organizations to navigate the evolving digital threatscape with resilience and confidence.
Kovacs, B. (2024, February 27). NIST Cybersecurity Framework 2.0 officially released. SecurityWeek. https://www.securityweek.com/nist-cybersecurity-framework-2-0-officially-released/
NIST releases version 2.0 of Landmark Cybersecurity Framework. NIST. (2024, February 26). https://www.nist.gov/news-events/news/2024/02/nist-releases-version-20-landmark-cybersecurity-framework
Copyright © 2025 Clear Infosec. All Rights Reserved.