- Email: info@clearinfosec.com
- 1800 760 5656

1. Introduction
2. Vulnerability Statistics – 2021
3. Risk – Threat – Vulnerability
4. Model for Vulnerability Management
a. Capability Maturity Model certification (CMMC) framework
b. SANS Vulnerability Management Maturity Model
5. Vulnerability Management best practices
6. Final Thoughts
The year 2020 has been a tough year for the most. With a greater level of optimism, we have stepped into 2021 which is not much different from 2020. But we have learned to adapt to the changes around us.
The remote working shift was the biggest challenge for every business across the globe, changing entirely the way businesses work and how the workforce connects to their workplace. It increased the attack surface of IT infrastructure.
An attack surface is the entire network and software environment that is exposed to remote or local attacks. It can also be explained as the different ways through which an application or network can possibly be exploited by a bad actor. No doubt that no business wants to expose itself to such risks and the workforce moved out of the secure zone left them with a wider attack surface.
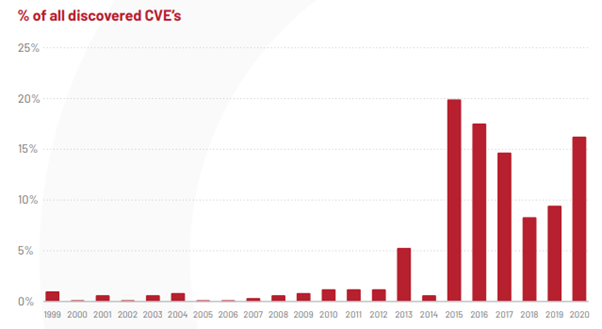
Leaving behind a vulnerability unnoticed can cause harm that is beyond our expectation as it is through exploiting the vulnerabilities, the bad actors gain access to your systems. Cybersecurity statistics say that in 2020, the number of vulnerabilities published is more than 18000, which is higher than the preceding years.
The below graph shows the number of Common Vulnerabilities and Exposure (CVE) found over the years. 88% of the CVE’s existing now are at least 0-5 years old.
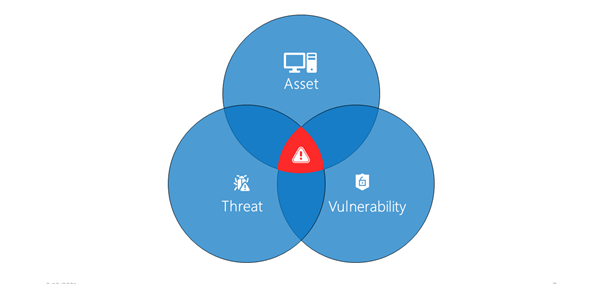
Risk, Threat, and Vulnerability are almost related terms that signify different things.
In cybersecurity, Vulnerability is a weak spot which a bad actor can exploit and gain unauthorized access to one’s system. With the gained access, they can install malware and can get their hands on the sensitive data and that is not something an organization will expect to happen.
A threat can be any event, action, or circumstance that exploits a vulnerability, causing damages. The objective is to gain unauthorized access to sensitive systems or data. The person causing the threat can be the threat actor who takes advantage of the vulnerabilities. When a threat actor exploits a vulnerability, which can give him unauthorized access posing potential damage or loss is a Risk.
Organizations must adopt strategies that increase the visibility of vulnerabilities and risk mitigation to reduce the attack surface and risk exposure.
SANS has developed a Vulnerability Management Maturity Model from the Capability Maturity Model Integration (CMMI) with a goal to provide insight and guidance in the areas important to Vulnerability Management. This maturity model is not intended to resolve all your problems but to categorize them into more manageable pieces for you to handle them easily. Let us look into the levels of CMMI first and then move to SANS Vulnerability Management Model.
Capability Maturity Model certification (CMMC) framework
This is a proven industry framework to improve product quality and development efficiency for both software and hardware. It is sponsored by the Department of Defence (DoD) in co-operation with Carnegie Mellon University and Software Engineering Institute (SEI).
This model uses 5 levels to describe the maturity of organizations. It provides the organizations with a way to focus and manage hardware and software development from product inception through deployment and maintenance. At present, your organization can be at any level of this model. It is always better to start from where you are and move up.
Level 1:
This level involves organizations performing a set of specified practices. Thus, it deals with processes that are maintained in an ad-hoc manner. Processes can be unpredictable, poorly controlled, and reactive. It may not even meet the specific objectives as it may not be stable.
Level 2:
This level involves organizations that establish and document practices & policies to implement their CMMI efforts. Thus, it deals with managed processes that are planned and executed in accordance with policies by skilled people.
Level 3:
This level involves organizations to establish, maintain and resource a plan demonstrating management of activities for process implementation. Thus, it deals with defined processes that are well understood, deployed, and executed proactively.
Level 4:
This level involves organizations to review and measure practices of effectiveness. Thus, it deals with processes that are measured and controlled well. This enhances the detection and response capabilities to address and adapt to varying tactics, techniques, and procedures.
Level 5:
This level involves organizations to standardize and optimize process implementation. Thus, it focuses on continuous quantitative improvements. It increases the depth and sophistication of cyber security capabilities.
SANS Vulnerability Management Maturity Model
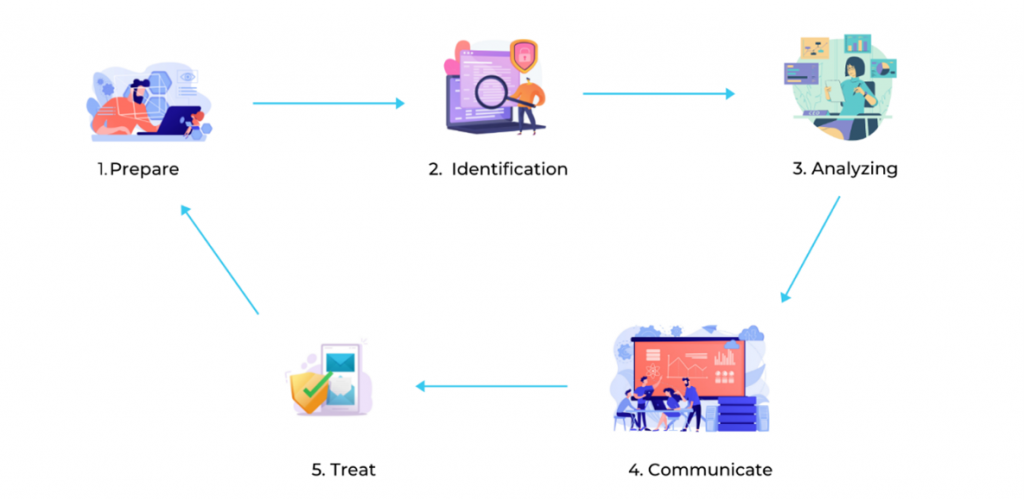
Prepare
Preparation is the first and vital part of a vulnerability management program. The team must figure out all the assets, the key assets that need to be protected, their importance, plan for evaluating the vulnerabilities, and knowing how to treat them. The accepted vulnerabilities should also be included to ensure the acceptance of its risk.
Identify
The team should finalize all the assets that need to be evaluated in the preparation step itself and identifying the key assets is the second one. Those have critical data stored in them, those have critical uptime required, etc. Not just the assets, but the access paths to them should also be included in the evaluation process. With the assessments and scans, the vulnerabilities in all assets are identified.
Analyze
Right after identifying the vulnerabilities, what needs to be done is evaluating them and prioritize them according to the risk each of them possesses. This gives an idea of the security posture of the assets and environment. The level of impact is evaluated, and the priority of which needs to be treated first is decided based on it. This process can be simple as running a scan to a complex set of processes to evaluate all the controls that are already in place.
Communicate
Most organizations prefer to jump into treating the vulnerabilities right when they are discovered, avoiding this step. The vulnerability management team must sit and discuss with the Ops team, Sys Admins and executives, etc to plan on how and when to treat the vulnerabilities. Validate all the vulnerabilities found with the team. This will keep everyone in the team know about what is going on and prevents human errors to a great extent.
Treat
This is the ultimate goal of a vulnerability management program where the vulnerabilities are treated to reduce the risk. This is not actually a final step as this entire thing is a cyclic process. After validating vulnerabilities that hold a potential risk to the organization, the next step involved is to find ways to patch the vulnerabilities.
Finding and Evaluating vulnerabilities needs an efficient team and skilled professionals to perform assessments, choose the best tools, deploy an attack simulation, etc.
Many are still mistaken that Vulnerability assessments and Penetration testing is all that vulnerability management is consisting of. But the reality is very far from that as they both are just processes involved. But Red teaming is entirely different which involves security professionals manipulating your workforce and using all possible ways and technologies to compromise your system security.
Vulnerability Assessment
It is done with the use of tools either automated or manual against a system, network, application, etc. A detailed raw scan report will be available after the scan with all the vulnerabilities found and with descriptions and all. All the vulnerabilities need to be verified manually to confirm a true positive.
Penetration Testing
Performing Vulnerability assessments alone will not be much effective as it gives you only a list of vulnerabilities that your system has. In pen tests, the vulnerabilities are exploited and tried to leverage the access obtained to dig deep into your systems. Only a Penetration test will show you which of those listed vulnerabilities need immediate actions and thus helping you to categorize them all.
Red Team
The above-mentioned methods are all technical evaluations. But Red Teaming is entirely different, and it aims to get into your systems by any method using any possible means (within legal limits). It is a kind of real-world attack simulation where the team will try to exploit your vulnerabilities of systems by technical means as well as workforce by their social engineering skills.
Vulnerability Management best practices
Organizations with a proactive and pre-emptive strategy to secure their systems, networks, and applications will be able to stay safer from cyber threats. But with today’s evolving technologies, the attackers, as well as attacks, are so advanced that they can even bypass some of the advanced security methods.
We have seen in our previous blog, Infosec insights to the new normal, that cybersecurity is not just an IT team’s job now and it is not some random rules to follow blindly. Let’s look at some best practices for improving your vulnerability management program.
Final Thoughts
An efficient vulnerability management program enables you to address the growing cyber risks and will give confidence in your Infrastructure integrity, availability of system, and confidentiality of your sensitive information. No need for a complicated set of security tools and all to improve your cybersecurity posture. The right vendors and a team of skilled security professionals can shoulder the responsibilities and make your pursuit of information security less toil.
Reference:
Copyright © 2025 Clear Infosec. All Rights Reserved.