- Email: info@clearinfosec.com
- 1800 760 5656

ISO 27001 stands as a globally recognized standard for Information Security Management Systems (ISMS), systematically safeguarding vital company data. It furnishes a thorough blueprint for establishing, executing, sustaining, and refining an ISMS, centering on the assessment and control of information security risks customized to the organization’s unique requirements. Over time, the ISO 27001 standard undergoes periodic updates to adapt to evolving information security risks, technological progressions, and shifts in regulatory landscapes.
The transition from ISO 27001:2013 to ISO 27001:2022 signifies a significant advancement in the standard’s approach to addressing the intricacies of information security in today’s digital milieu. While the 2013 iteration laid the groundwork for best practices in information security management, the latest 2022 revision builds upon these foundations with updated directives that confront current and emerging threats in the field.
Let’s compare ISO 27001:2013 with ISO 27001:2022 to see what’s changed in the standard, based on the clauses.
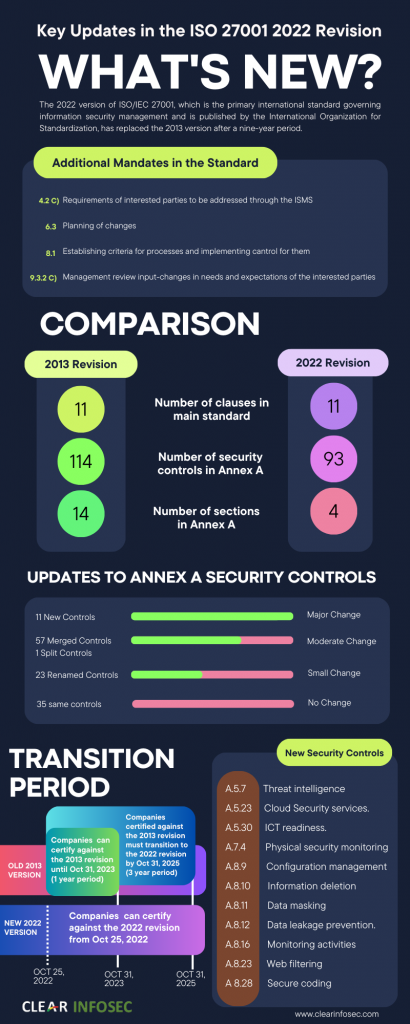
Clause (4-10) | ISO 27001:2013 | ISO 27001:2022 |
4.2 Understanding the Needs and Expectations of Interested Parties | Not explicitly requiring an analysis of interested parties’ requirements to be addressed through the ISMS. | Introduced a new item (c) mandating an analysis to determine which requirements from interested parties needs and expectations to be managed through the ISMS. |
4.4 Information Security Management System | Less specific language around the identification of necessary processes within the ISMS. | A new phrase was added that requires organizations to identify relevant processes and their interactions within the ISMS, emphasizing a more comprehensive approach. |
5.3 Organizational Roles, Responsibilities, and Authorities | Contained general instructions on communicating roles related to information security. | A minor phrase was updated to clarify the communication of roles relevant to information security within the organization. |
6.2 Information Security Objectives and Planning to Achieve Them | Provided general guidance on setting information security objectives. | Additional guidance (d and e) on the information security objectives was introduced, including the need for regular monitoring and formal documentation. |
6.3 Planning of Changes | N/A | A new sub-clause was added, which sets a standard for planning changes to the ISMS, ensuring changes are controlled. |
7.4 Communication | Included detailed instructions for communication (items a-c), with separate points (d and e) for who should communicate and how. | Items a-c remain the same; simplified and combined items related to communication (previously d and e) into a new item (d), streamlined focusing on how to communicate. |
8.1 Operational Planning and Control | Offers basic guidance on operational planning and control. | New guidance was added to establish criteria for operational actions identified in Clause 6 and control those actions according to the criteria. |
9.2 Internal Audit | Separate sections for Clause 9.2.1 and 9.2.2. | A clause was revised to consolidate previous subclauses (9.2.1 and 9.2.2) into a single section without materially changing its content. |
9.3 Management Review | No explicit mention of considering changes to the needs and expectations of interested parties. | A new item (9.3.2 c) was added, which included a requirement for the management review to consider changes to interested parties’ needs and expectations. |
10 Improvement | Structure did not prioritize Continual Improvement. | Reorganized subclauses to prioritize Continual Improvement (10.1) before Nonconformity and Corrective Action (10.2), emphasizing the importance of ongoing improvement in the ISMS. |
The transition from ISO 27001:2013 to ISO 27001:2022 brings about a modernization and simplification of the framework, adapting it to present information security risks and technologies by reorganizing the controls. The annex’s title has been changed to “Information security controls reference” from its previous name, “Reference control objectives and controls.
Aspect | ISO 27001:2013 | ISO 27001:2022 |
Control Domains/Themes | 14 domains | 4 categories |
Total Number of Controls | 114 controls (across 14 domains) | Decreased overall 114 controls into 93 controls (across 4 categories) |
New Controls Introduced | N/A | Introduction of 11 new controls |
Controls Merged | N/A | Consolidation of 57 controls into fewer overarching controls |
Controls Renamed | N/A | Renaming of 23 controls for clarity or relevance |
Controls Removed | N/A | Elimination of 3 controls deemed no longer necessary |
Reorganization of Controls | 1. Information security policies | 1. A.5 Organizational controls (37 controls) |
The ISO 27001:2022 version introduces 11 new controls within Annex A.
Whether you’re currently certified to ISO/IEC 27001 or new to the standard, Ana-Data offers a comprehensive range of services to guide you towards successful certification.
Our services encompass:
Conducting ISO 27001 gap assessments and providing remediation support to prepare you for the certification audit. We cover all facets of remediation activities needed, from designing processes and architecture to implementing solutions, developing documentation, and offering project and program management. Additionally, we provide subject matter expert support in specific areas.
Performing ISO 27001 internal audits as mandated by clause 9.2 of the standard.
Equipping your team with the necessary knowledge and providing support throughout the certification process.
Let Ana-Data be your partner in achieving ISO 27001 certification excellence.
Copyright © 2024 Clear Infosec. All Rights Reserved.