- Email: info@clearinfosec.com
- 1800 760 5656

More than 10 million Android users are being impacted by the new GriftHorse mobile virus. According to security experts, these typical premium service scams are using phishing techniques to make $41 every month per user by
GriftHorse apps in all categories were discovered by Zimperium on Google Play and third-party app stores. GriftHorse, a Trojan code discovered in more than 200 malicious apps in at least 70 countries, has been afflicting Android phones since November 2020, according to Zimperium researchers Aazim Yaswant and Nipun Gupta. Google has taken down the flagged apps, but there could be more play store and a variety of unofficial store apps on people’s phones could still be active.
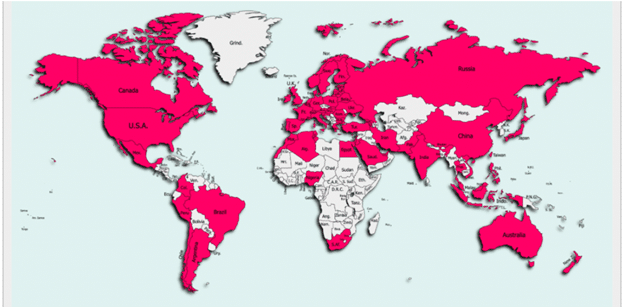
Distribution of GriftHorse Android malware victims. Source: Zimperium.
The new Trojan malware deceives Android users into sign up for a variety of paid services. Following their successful attack, affected Android users are required to pay around $41 in monthly premium subscription fees.
The Trojans are built using the Apache Cordova mobile application development framework, according to Zimperium’s latest blog post. For cross-platform mobile development, Cordova allows developers to use standard web technologies such as HTML5, CSS3, and JavaScript. Developers can use this technology to push out app updates without requiring users to do so manually.
While this framework improves the user’s experience and security, it can also be used to host malicious code on the server and develop an application that executes the code in real-time. The application appears as a web page with HTML, CSS, JavaScript, and image references.
When an app is launched, for example, AES is used to decrypt the encrypted files in the “assets/www” folder. After a little more digging, the source code for the core functionality uses the GetData() function to encrypt an HTTP POST request and establish communication between the application and a first-stage command-and-control (C2) server.
The app then receives an encrypted response, which is decrypted with AES to obtain a C2 URL for the second stage. According to the analysis, it also performs a GET request using Cordova’s “InAppBrowser” function to uncover a third-stage URL, and it begins sending user notifications about the alleged “prize” once every hour, five times in a row.
Regardless of the application or the victim’s geolocation, the second-stage C2 domain is always the same.
The third-stage URL redirects to a final page that requests the victim’s phone number and enrolls them in a variety of paid services and premium subscriptions.
According to researchers, the JavaScript Interface facilitates interaction between the WebPage and in-app functions by allowing JavaScript code inside a WebView to trigger actions in native (application-level) code. This can include gathering information about the device, such as the IMEI and IMSI numbers, among other things.
GriftHorse’s success, according to the researchers, is due in part to the fact that it avoids pattern-based detection and blocking by not reusing common strings in the application code.
Victims are tricked into downloading Android apps that appear to be safe and legitimate. The most popular malicious app — a translator — has received at least 500,000 downloads and ranges from puzzle games and utilities to dating software, food, and drink.
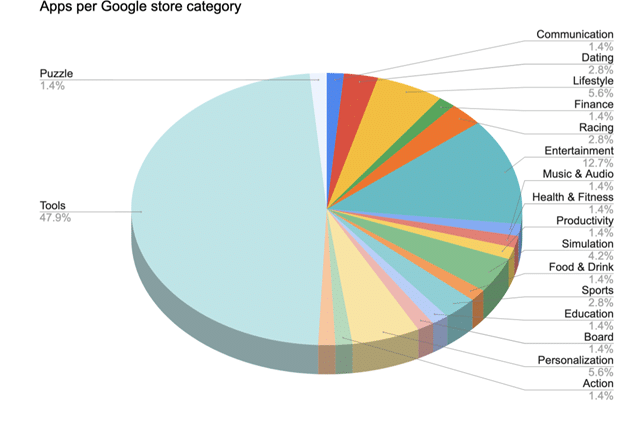
Source: zLabs
Mobile application sources and permissions:
The researchers discovered that 10.5 percent of the 68,051 apps they looked at shared personal information with third-party services without disclosing it in their privacy policies. In addition, only 22.2 percent of the 68,051 apps named third-party partners or affiliates in their privacy policies, with most apps concealing where user data is collected.
Sensor data, call logs, camera and microphone access, location, storage, and contact lists are among the permissions that apps can request. While many legitimate apps require access to certain features, you should always be aware of which apps have access to which data in order to avoid unnecessary security risks or data leaks.
No matter which mobile operating system we use, download apps from verified, trusted sources is the best option to maintain your security and privacy. To be on the safe side, you should uninstall any application that you no longer require.
Mobile malware:
Mobile malware has become as popular as malicious software but with these variants infecting Android, iOS, and sometimes make their way into official app stores. Malware developers frequently use the technique of submitting a legitimate-looking mobile application and then uploading malicious functions once a user base has been established.
It’s recommended that you download and install an antivirus software solution for mobile devices, however, you will probably be safe enough as long as you do not jailbreak your phone and Instead of third-party repositories, you only download the app. APKs from trusted sources.
GriftHorse Android TROJAN steals millions from over 10 million VICTIMS Globally. Zimperium Mobile Security Blog. (2021, September 29). Retrieved September 30, 2021, from https://blog.zimperium.com/grifthorse-android-trojan-steals-millions-from-over-10-million-victims-globally/.
Seals, A. T., & Seals, T. (n.d.). GriftHorse money-stealing TROJAN Takes 10M Android users for a ride. Threatpost English Global threatpostcom. Retrieved September 30, 2021, from https://threatpost.com/grifthorse-money-stealing-trojan-android/175130/.
Copyright © 2025 Clear Infosec. All Rights Reserved.