- Email: info@clearinfosec.com
- 1800 760 5656

On December 1, 2025, public disclosure was made for a critical remote-code execution (RCE) vulnerability in Outlook, tracked as CVE-2024-21413.
According to the disclosure, a Proof-of-Concept (PoC) exploit is now available — meaning that researchers (and potentially attackers) can reproduce the exploit under lab conditions, raising the likelihood of real-world exploitation.
This vulnerability is especially dangerous because it abuses a mechanism in Outlook named “MonikerLink”. Attackers can embed a malicious link that bypasses standard protections (such as “Protected View”) and triggers the exploit when the email is processed.
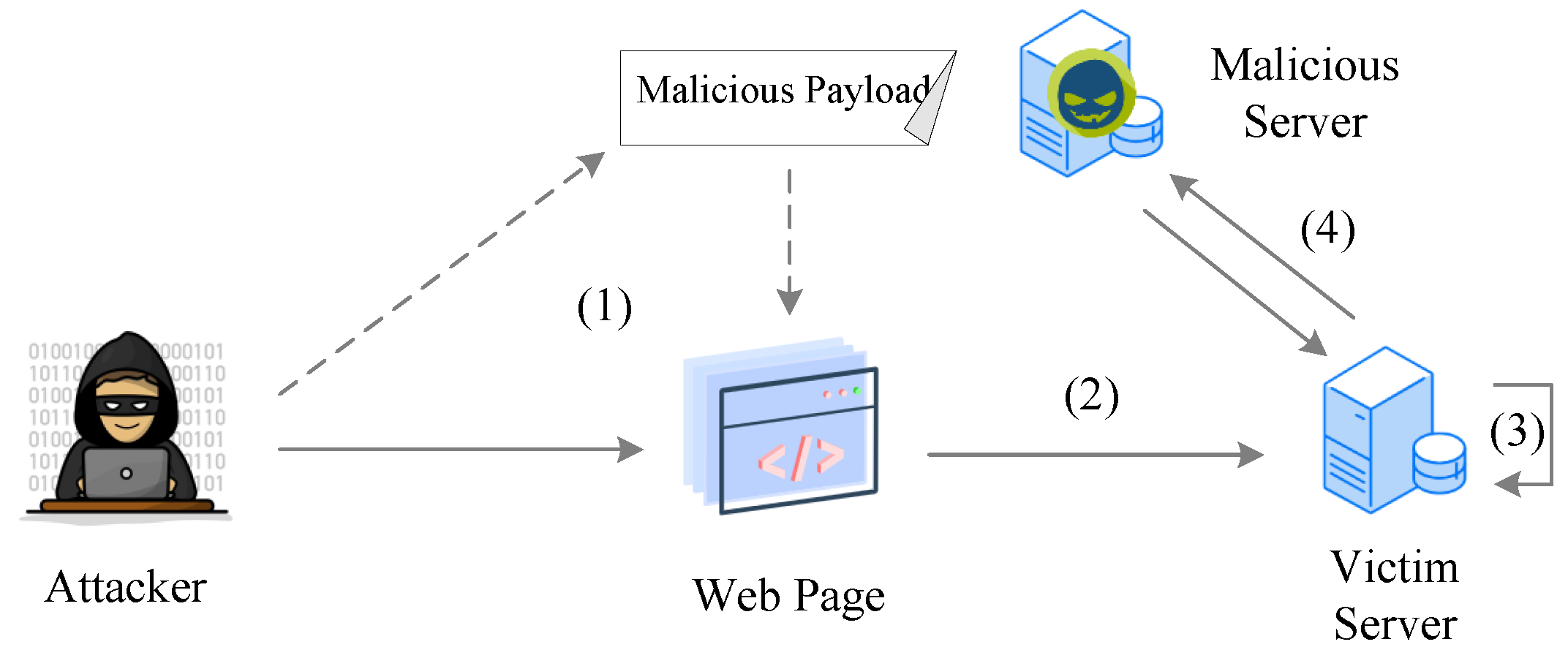
MonikerLink handling flaw: The vulnerability originates from improper input validation in how Outlook processes certain hyperlink types. Specifically, when a link uses a file:// protocol followed by specially crafted data, Outlook fails to correctly treat it as untrusted. This allows bypassing security controls.
Bypassing Protected View and triggering SMB/NTLM leak: Under normal circumstances, attachments or suspicious content are opened in a sandboxed read-only “Protected View.” But the crafted MonikerLink can dodge that. Upon processing the link, Outlook may attempt to access resources via SMB — potentially pointing to a remote server controlled by the attacker. This can result in leakage of the victim’s NTLM credentials over the network.
Remote code execution & full compromise: Beyond credential theft, the flaw enables arbitrary code execution on the victim’s machine — meaning the attacker could run malicious payloads, fully compromising the system, exfiltrate data, install malware, or pivot deeper into a network.
Because the PoC is public, even moderately skilled attackers can leverage the flaw. As such, the severity is very high (CVSS score 9.8 per public reporting).
This is not the first time Outlook has suffered critical RCE vulnerabilities. For example:
CVE-2024-30103 — a “zero-click” RCE flaw disclosed in 2024, where simply receiving a malicious email could trigger arbitrary code execution when Outlook processed it
CVE-2025-32705 — an out-of-bounds read flaw affecting Outlook, which could be triggered by opening a malicious file and lead to local code execution.
These past vulnerabilities underscore a pattern: attackers exploiting weaknesses in how Outlook parses inputs (links, embedded objects, files), often leveraging “zero-click” or minimal-interaction scenarios to compromise targets.
High risk of widespread exploitation: Outlook is ubiquitous in corporate and enterprise environments. A single successful exploit can compromise a user’s credentials (via NTLM leak) — which can be reused for lateral movement, domain pivoting, or privilege escalation.
Data theft / malware load / network infiltration: Arbitrary code execution can enable threat actors to install malware, deploy backdoors, exfiltrate sensitive data, or persist in a network undetected.
Bypassing typical defenses: Since the exploit abuses standard link processing and may not require user interaction beyond email receipt or minimal click, traditional defenses (basic sandboxing, static attachment filters) may not suffice.
For organizations that handle sensitive data — for example, healthcare providers, financial institutions, or corporate IT departments — this RCE represents a serious attack vector.
To defend against this RCE vulnerability (and similar future Outlook flaws), security teams should:
Apply official patches immediately — The vendor has released updates to remediate CVE-2024-21413. All installations of affected Outlook/Office versions (Microsoft 365 Apps, Office 2016, Office 2019) should be updated without delay.
Block outbound SMB (port 445) to untrusted endpoints — Since the exploit may attempt SMB connections to attacker-controlled servers, blocking outbound SMB traffic at the network edge can prevent credential leakage or further exploitation.
Monitor email traffic for suspicious patterns — Use detection mechanisms (e.g. specific YARA rules) to flag incoming emails containing malicious file://-style links or other anomalous link structures associated with MonikerLink exploits.
Educate users & restrict risky features — Discourage using automated email-opening features, disable automatic link or preview rendering where possible, and train users to avoid opening emails/links from unknown or untrusted senders.
Adopt layered security & hardening for sensitive deployments — Use endpoint isolation, least-privilege accounts, network segmentation, and strong authentication mechanisms so even if one client is compromised, lateral movement is constrained.
Given our role at ClearInfoSec (part of AnaData Consulting Inc.), this vulnerability underscores why proactive security posture matters. Many organizations remain vulnerable simply due to delayed patching or misconfigurations. As part of our service offerings (red-teaming, security audits, awareness training), we recommend:
Including this RCE scenario in tabletop exercises to evaluate incident response readiness.
Reviewing and strengthening email-handling policies — especially for clients with high compliance/regulation requirements (e.g. healthcare, finance).
Enforcing network controls and outbound traffic filtering as part of our defensive architecture recommendations (e.g. for ClearCloudAI-migrated workloads).
Conducting simulated phishing / exploit-chain testing to identify potential weaknesses in real-world usage, thereby exposing gaps before adversaries do.
The disclosure of CVE-2024-21413 — a critical remote code execution vulnerability in Outlook — is a wake-up call for organizations that rely on Outlook for daily communication. The combination of a public PoC, high severity (CVSS 9.8), and a dangerous attack vector (MonikerLink / SMB / credential theft) makes this vulnerability a serious threat.
For security-first organizations — like those served by ClearInfoSec — immediate patching, network hardening, traffic filtering, and user awareness are not optional; they are essential.
At AnaData / ClearInfoSec, we are ready to help organizations assess their exposure, apply required mitigations, and implement best-practice controls to prevent exploitation — ensuring enterprise communication remains secure, resilient, and threat-resistant.
Copyright © 2026 Clear Infosec. All Rights Reserved.