- Email: info@clearinfosec.com
- 1800 760 5656

Android malware BRATA gained new dangerous features in the latest version like GPS tracking, the ability to use various communication channels and factory reset to hide fraudulent wire transfer.
BRATA – Brazilian Remote Access Tool (RAT) Android was a spyware, which was later known to be a banking trojan. This spyware was found out by Kaspersky as banking and financial institution-targeting Android RAT (The remote access trojan) in 2019. Before this RAT reach US and Spain, it used to target only Brazil.
Cleafy published a research in December 2021 and highlighted BRATA as malware emerging across Europe. It was discovered that hackers posing as bank customer service representatives were targeting e-banking users and collecting their credentials.
The BRATA trojan has been detected in three different variants so far:
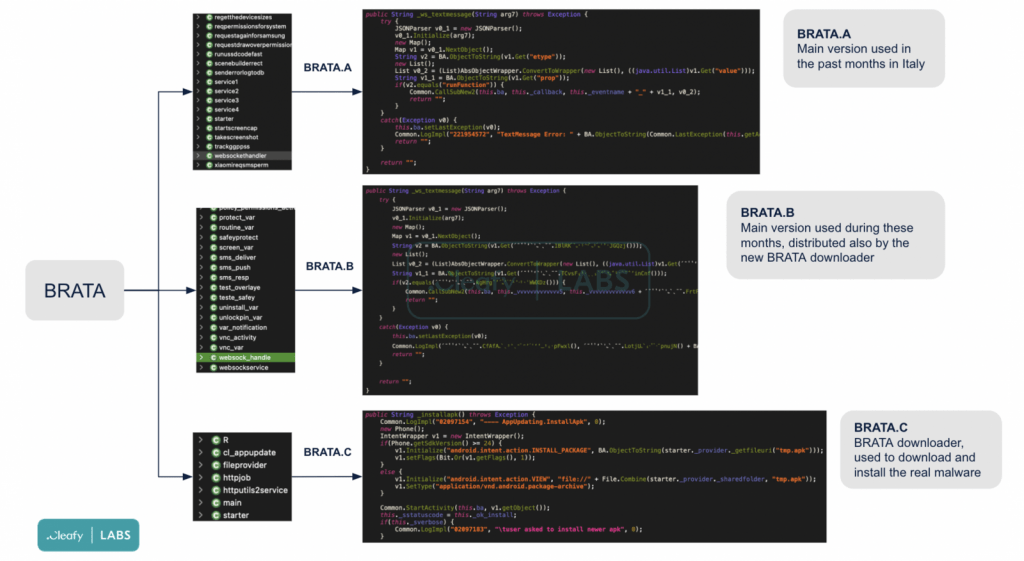
The creators of BRATA are constantly changing the malicious code to avoid antivirus software detection. “Although the majority of Android banking trojans try to obfuscate/encrypt the malware core in an external file (eg. .dex or .jar), BRATA uses a minimal app to download in a second step the core BRATA app (.apk),” the Cleafy team added.
“When the victim clicks on the install button, the downloader app sends a GET request to the command-and-control (C2) server to download the malicious .APK,” they explained. “At this point, the victim has two malicious apps installed on their device.”
After BRATA installs a malicious app and executes the code, the accessibility permissions had been granted and can take control over the compromised device. Here’s a list of commands discovered by McAfee in all of the payloads :
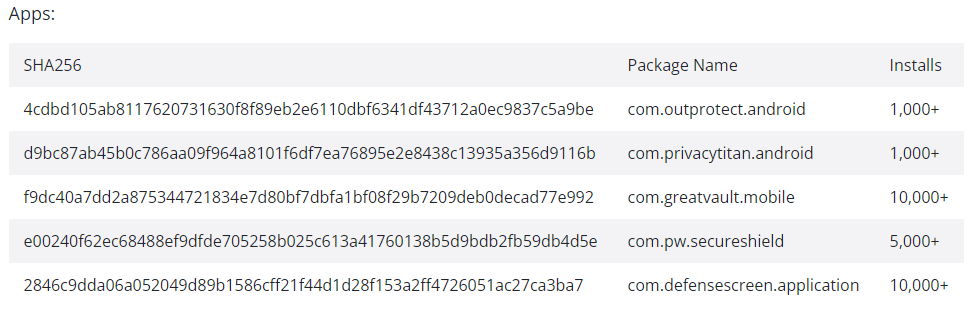
Here are some of the apps which are compromised :
Here are some suggestions to help you avoid being deceived by Android malware.
As a result, Android users must exercise extreme caution when allowing this access to any app. As accessibility services are so powerful, a malicious application may exploit them to completely take over device data, online banking, and funds.
Get the protection you need and the privacy you want, with Clear Infosec. Check out our services and reach out to know more about how to secure your data.
Fernando Ruiz Apr 12, Ruiz, F., Fernando Ruiz Mobile Malware Researcher Fernando Ruiz is a Security Researcher in McAfee, Researcher, M. M., & Fernando Ruiz is a Security Researcher in McAfee Labs. He specializes in mobile threats and Android malware. Ruiz performs deep analysis and reverse engineering of malicious code. (2021, April 12). Brata keeps sneaking into Google Play, now targeting USA and Spain. McAfee Blog. Retrieved January 25, 2022, from https://www.mcafee.com/blogs/other-blogs/mcafee-labs/brata-keeps-sneaking-into-google-play-now-targeting-usa-and-spain/
Copyright © 2026 Clear Infosec. All Rights Reserved.