- Email: info@clearinfosec.com
- 1800 760 5656
In today’s ever-evolving threat landscape, cybersecurity remains a paramount concern for organizations worldwide. As adversaries continuously refine their tactics and exploit new vulnerabilities, the need for proactive defense measures has never been more critical. Advanced Threat Modeling emerges as a pivotal strategy in this dynamic environment, offering organizations a systematic approach to identify, assess, and mitigate potential risks before they can be exploited.
At its core, advanced threat modeling embodies a proactive mindset, shifting the focus from reactive incident response to preemptive risk management. By meticulously dissecting the intricate architecture of systems, applications, and networks, organizations can uncover hidden vulnerabilities and anticipate potential attack vectors. This proactive stance enables technical teams to fortify defenses, prioritize resource allocation, and stay one step ahead of cyber threats.
Central to the efficacy of advanced threat modeling is its integration with established cybersecurity frameworks, such as the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF). NIST CSF provides a structured blueprint for managing cybersecurity risks, encompassing five core functions: Identify, Protect, Detect, Respond, and Recover. Through a symbiotic relationship with NIST CSF, advanced threat modeling enriches each of these functions, enhancing their effectiveness and resilience.
In this blog series, we embark on a comprehensive exploration of advanced threat modeling within the framework of NIST CSF. We delve deep into technical strategies, methodologies, and best practices, equipping readers with the knowledge and tools necessary to navigate the intricacies of modern cybersecurity. From understanding the foundational concepts of threat modeling to implementing advanced techniques and leveraging cutting-edge technologies, this series aims to empower technical professionals in their quest for robust risk management and effective threat mitigation.
Threat modeling represents a systematic approach to identifying, analyzing, and mitigating vulnerabilities within systems and networks, serving as a cornerstone of modern cybersecurity practices. By peering beneath the surface and dissecting the intricate interplay of assets, threats, and vulnerabilities, organizations can gain invaluable insights into their security posture and bolster their defenses against evolving cyber threats.
In this exploration, we delve beyond the surface level of threat modeling, venturing into the depths of advanced techniques and methodologies. From scenario-based modeling to attack surface analysis and beyond, we illuminate the path to proactive risk management and resilience. Join us as we unravel the intricacies of threat modeling, empowering organizations to anticipate, mitigate, and thwart cyber threats with precision and confidence.
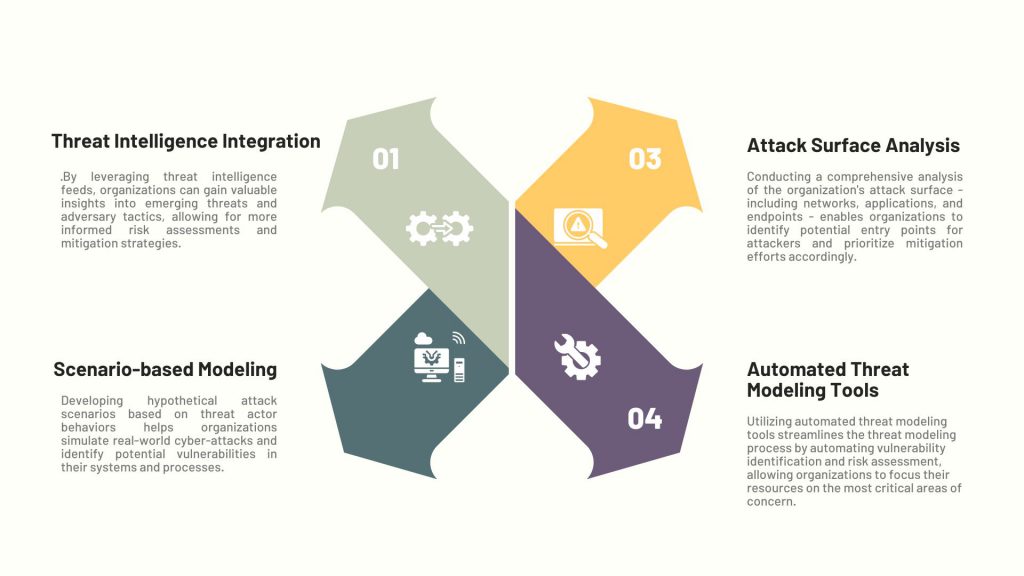
• Threat Intelligence Integration: By leveraging threat intelligence feeds, organizations can gain valuable insights into emerging threats and adversary tactics, allowing for more informed risk assessments and mitigation strategies.
• Scenario-based Modeling: Developing hypothetical attack scenarios based on threat actor behaviors helps organizations simulate real-world cyber-attacks and identify potential vulnerabilities in their systems and processes.
• Attack Surface Analysis: Conducting a comprehensive analysis of the organization’s attack surface – including networks, applications, and endpoints – enables organizations to identify potential entry points for attackers and prioritize mitigation efforts accordingly.
• Automated Threat Modeling Tools: Utilizing automated threat modeling tools streamlines the threat modeling process by automating vulnerability identification and risk assessment, allowing organizations to focus their resources on the most critical areas of concern.
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) serves as a comprehensive blueprint for managing cybersecurity risks, encompassing five core functions: Identify, Protect, Detect, Respond, and Recover. Each of these functions plays a vital role in fortifying an organization’s cyber defenses and enhancing its resilience against threats. When integrating advanced threat modeling techniques with NIST CSF, organizations can amplify the effectiveness of each core function, thereby establishing a robust framework for proactive risk management.
1. Governance in cybersecurity is paramount, serving as the cornerstone of setting up and overseeing an organization’s risk management approach, expectations, and policies. It encompasses several key elements: firstly, understanding the organization’s risk context, including its mission, priorities, stakeholders, objectives, and direction, is essential for informed decision-making. Secondly, a robust risk management strategy is crucial, involving the establishment of priorities, constraints, and risk tolerance to guide operational risk decisions effectively. Through effective governance, organizations can navigate the complex landscape of cybersecurity risks with confidence and resilience.
2. Identify: At the heart of NIST CSF lies the Identify function, which involves understanding and managing cybersecurity risks to systems, assets, data, and capabilities. Advanced threat modeling provides a systematic approach to identifying potential threats and vulnerabilities within the organization’s infrastructure. By conducting comprehensive risk assessments and threat modeling exercises, organizations can gain insights into their attack surface, prioritize critical assets, and understand the potential impact of cyber threats.
3. Protect: Building upon the insights gained from threat modeling, organizations can implement appropriate safeguards to protect their systems and data from potential threats. Integration with NIST CSF enables organizations to align their protective measures with identified risks and vulnerabilities. By mapping threat modeling findings to NIST CSF controls and best practices, organizations can ensure that protective measures are deployed effectively, mitigating potential risks and enhancing their overall security posture.
4. Detect: The Detect function of NIST CSF focuses on establishing mechanisms to identify cybersecurity events promptly. Threat modeling techniques play a crucial role in enhancing detection capabilities by anticipating potential attack vectors and anomalous behaviors. By incorporating threat modeling insights into security monitoring and incident detection processes, organizations can enhance their ability to detect and respond to cyber threats in a timely manner, minimizing the impact of security incidents.
5. Respond: In the event of a cybersecurity incident, organizations must have predefined response procedures to contain the impact and restore normal operations. Advanced threat modeling enables organizations to anticipate potential threat scenarios and develop proactive response strategies. By integrating threat modeling with NIST CSF, organizations can align their incident response plans with identified risks and vulnerabilities, ensuring a coordinated and effective response to cybersecurity incidents.
6. Recover: After an incident, organizations need to recover swiftly, restoring affected systems and data while implementing measures to prevent future occurrences. Threat modeling can inform post-incident recovery efforts by identifying weaknesses in existing controls and providing insights into lessons learned. By integrating threat modeling with the Recover function of NIST CSF, organizations can streamline the recovery process, minimize downtime, and enhance their resilience against similar threats in the future.
In conclusion, the integration of advanced threat modeling techniques with the core functions of the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) represents a proactive approach to cybersecurity risk management. By systematically identifying, analyzing, and mitigating potential threats, organizations can enhance their resilience against cyber attacks and safeguard their digital assets effectively.
Looking ahead, it is essential for organizations to continue evolving their threat modeling practices to adapt to the ever-changing threat landscape. This includes embracing emerging technologies such as artificial intelligence and machine learning to enhance threat detection capabilities and automate aspects of the threat modeling process. Additionally, collaboration and information sharing within the cybersecurity community will be crucial for staying abreast of new threats and vulnerabilities.
Furthermore, organizations should prioritize ongoing training and education for their technical teams to ensure they remain equipped with the skills and knowledge necessary to effectively implement advanced threat modeling techniques. By fostering a culture of cybersecurity awareness and continuous improvement, organizations can strengthen their cyber defenses and mitigate risks proactively. Together, these efforts will contribute to a more secure digital ecosystem for organizations and individuals alike.
Copyright © 2026 Clear Infosec. All Rights Reserved.