- Email: info@clearinfosec.com
- 1800 760 5656

ISO 27001 is widely regarded as the premier international standard for implementing an information security management system (ISMS). It provides a systematic approach to managing sensitive company information and defending against cyber threats.
Artificial intelligence is transforming how organizations approach information security. AI and machine learning algorithms can process huge volumes of data, identify patterns and anomalies, simulate cyberattacks, and automatically respond to incidents. This enables companies to detect threats early, quickly analyze risks, and take corrective actions.
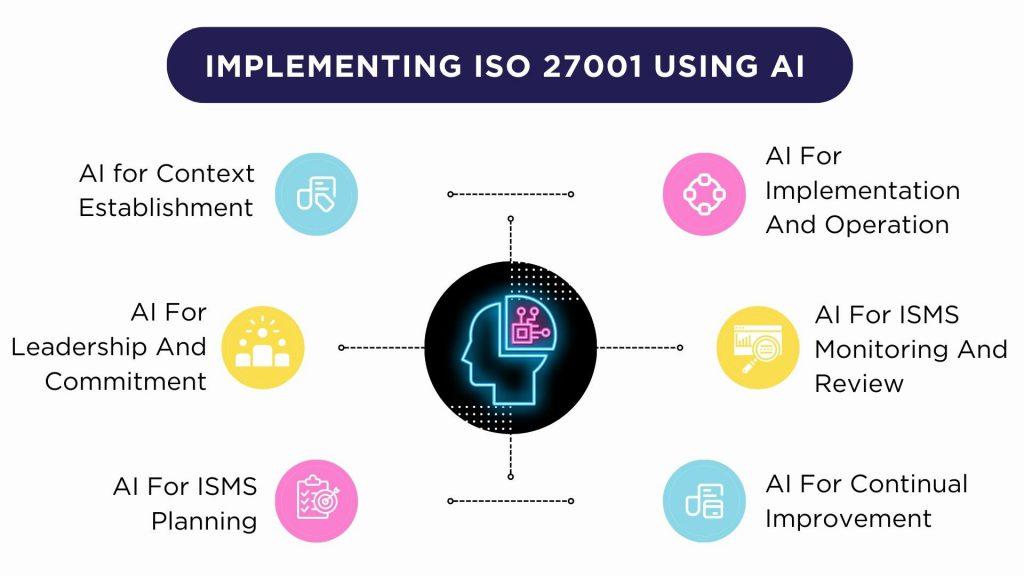
AI is the perfect technology to incorporate into an ISO 27001 compliant ISMS. It can enhance risk management, monitoring, incident response and virtually every other process. AI can make ISO 27001 implementations scalable, efficient and adaptive. It allows understaffed security teams to cover more ground with fewer resources.
In this comprehensive guide, we will explore the various ways artificial intelligence can be integrated at each step of the ISO 27001 implementation journey.
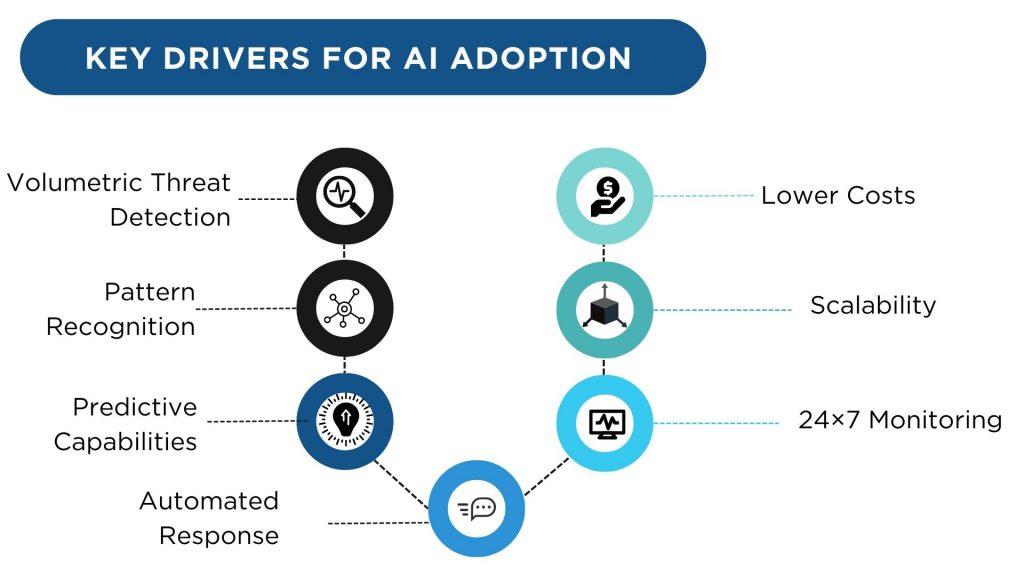
Artificial intelligence promises tremendous benefits for information security:
AI systems can process exponentially more data than humans. Even minor anomalies across massive datasets indicate threats that humans would likely miss. AI complements the human ability to detect sophisticated attacks by eliminating blindspots at volume.
By continuously analyzing huge volumes of data across diverse sources, AI algorithms uncover complex patterns in the noise that point to emerging threats. These would normally be invisible to human eyes. The broad data access of AI systems reveals tactics, techniques and procedures used by threat actors.
Machine learning models can ingest data from inside and outside the organization to make highly accurate predictions of where the next threat may arise or how an attack may unfold. The risk of insider threats can also be anticipated by analyzing behavioral patterns. AI systems get better at predictions over time as more data is fed.
When a threat surfaces, AI systems can instantly take routine response actions like blocking IP addresses or disabling accounts according to predetermined playbooks. This allows rapid containment before incidents spiral out of control. The machine speed of AI enables near real-time defenses.
AI systems continuously monitor networks, endpoints, servers, logs, traffic, access and usage without downtime, distractions or fatigue. Machine learning models trained on large volumes of historical data are able to flag anomalies suggesting potential threats. This vigilant monitoring is impossible for human teams alone.
AI systems can easily scale up or down on demand to meet the security needs of growing networks and users. Once the upfront development and training of algorithms is complete, they can be flexibly deployed across on-premise and cloud environments. This scalability is especially beneficial for large enterprises.
While the upfront investment in AI can be significant, the ongoing marginal costs are relatively low compared to recruiting, training and managing large teams of expert analysts. The computing costs required to run advanced AI algorithms also continue to fall steadily.
These AI capabilities perfectly complement the rigorous requirements of ISO 27001 implementations. That makes AI an extremely appealing technology for enhancing ISMS defenses.
While AI offers many benefits for ISO 27001, there are some key challenges and limitations to consider:
As AI adoption grows, it may become an integral part of future ISO 27001 revisions. Specific AI controls could be added to guide its use.
With more implementations, large datasets will be aggregated to create industry-specific AI models. These shared models will spread the benefits to smaller companies lacking resources to train their own algorithms.
In the long-term, autonomous AI security may shoulders a large part of day-to-day ISMS functioning with humans focused on strategic oversight. However, responsible oversight is necessary to check AI’s power and prevent unintended consequences.
ISO 27001 helps organizations manage information securely. AI unlocks capabilities to take that security to the next level. But striking the right synergy between humans and AI is key to maximizing benefits while minimizing downsides.
With the right strategy, processes and oversight, AI-powered ISO 27001 implementations can make information security management more predictive, proactive, scalable and resilient. This symbiosis fortifies defenses far beyond the capabilities of either humans or AI alone.
In conclusion, integrating artificial intelligence into ISO 27001 information security management systems unlocks invaluable capabilities for proactive threat defense. AI adds machine power to human expertise to create a formidable cyber shield. Organizations that embrace this synergy will be well-positioned to thrive in the emerging era of cyber risk.
Copyright © 2025 Clear Infosec. All Rights Reserved.
1 Comment
Comments are closed.