- Email: info@clearinfosec.com
- 1800 760 5656

A newly discovered and actively exploited vulnerability in the widely used Post SMTP plugin for WordPress has put an estimated 400,000+ websites at risk of full site takeover.
The vulnerability is tracked as CVE‑2025‑11833 and carries a CVSS score of 9.8 (Critical).
Affected plugin versions: up to and including Version 3.6.0. The patched version (3.6.1) was released on 29 Oct 2025.
The root cause: missing capability/authorization check in the plugin’s constructor method ( __construct ) and/or RESTAPI endpoints/logs – allowing unauthenticated actors to access sensitive email logs (including password reset messages) and then reset administrator credentials.
Evidence of active exploitation: security vendor Wordfence reported over 4,500 blocked attacks so far.
For cybersecurity professionals – especially those managing WordPress deployments in the enterprise or client-facing context (such as in your role at AnaData Consulting Inc. / ClearInfoSec) — this vulnerability is a textbook example of how an email/SMTP plugin can become a pivot for full compromise. Below we’ll walk through the technical mechanics, exploit chain, detection/mitigation controls, and proactive recommendations.
The Post SMTP plugin is designed to replace the default PHP mail() function in WordPress with authenticated SMTP delivery. It also includes email logging, OAuth/DNS validation, and other advanced features.
Because it handles email transport and logging, it necessarily deals with sensitive data (password-reset mails, admin notifications, etc.). Any flaw in access control or log-visibility becomes a serious risk.
Versions up to 3.6.0 (and earlier versions) lack proper capability checks in a constructor method ( __construct ) of the plugin. This method should normally validate that the caller is authenticated and has required privileges, but it doesn’t.
In some earlier disclosures (such as CVE-2025-24000) the issue was broken access control in REST API endpoints: i.e., the endpoint only verified user login status, not that the user had sufficient role/capability.
Because of this, an attacker (even unauthenticated) may be able to:
Retrieve the email log entries stored by the plugin (including outgoing mails).
Identify password-reset emails sent to admin or high-privilege users.
Trigger a password-reset for an administrator account.
Read the password-reset link or token from the logs.
Use that token/link to set a new password, log in as admin, and gain full access.
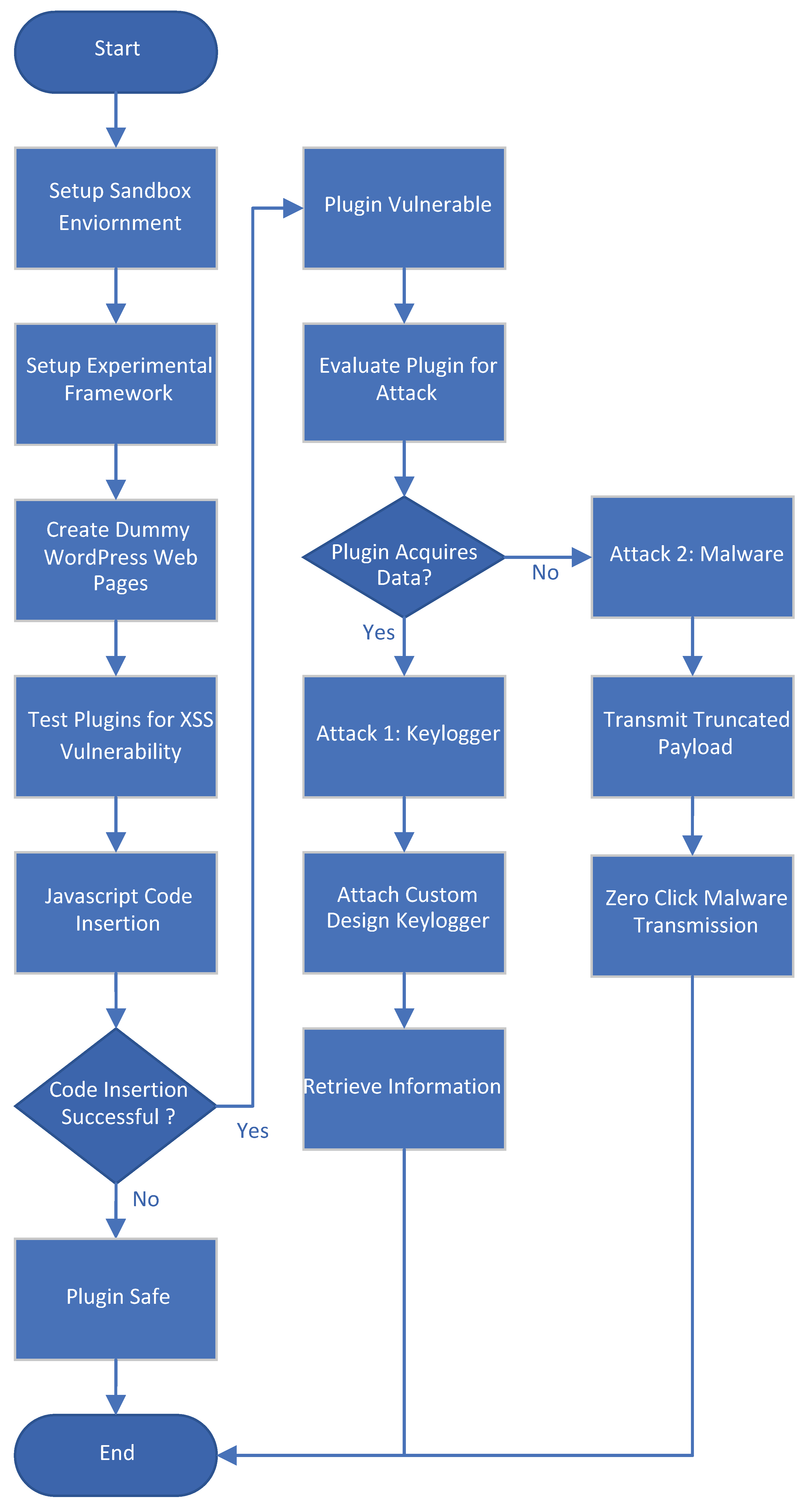
Attacker identifies a WordPress site using Post SMTP (public scans/search engines).
The attacker issues requests (either via REST endpoints or plugin routes) exploiting missing capability checks to enumerate or fetch email logs.
The attacker triggers a password-reset for the target admin user (via wp-login.php?action=lostpassword or plugin’s custom route).
The outgoing password-reset email is logged by the plugin, and the attacker obtains the reset link/token from the log.
Using the reset link, attacker changes the admin password.
With admin credentials, attacker logs into WordPress, modifies plugin/theme files (uploads malicious PHP shell/backdoor), creates new administrator accounts, or deploys malware/redirects/phishing.
Because the plugin deals with SMTP, the attacker can also monitor subsequent emails (e.g., two-factor codes, notifications).
No authentication required for initial step in many cases → lower bar for attacker.
Admin takeover equals full site compromise → lateral pivot to host access, database, backups, network of WordPress site.
Email logs serve as the “golden ticket” for reset links.
Large install base (400K+) means massive attack surface.
Exploits began hitting live sites around 1 Nov 2025 (per Wordfence).
Over 4,500 attacks were blocked by Wordfence’s protection rules, indicating that adversaries are actively scanning and exploiting.
Some sites remain unpatched, meaning the risk remains elevated.
Patch Immediately: Update Post SMTP plugin to version 3.6.1 or later.
Verify that no lower/hanging versions (3.6.0 or prior) remain installed.
If plugin cannot be updated for compatibility reasons, disable it temporarily or remove email-logging features.
Conduct an audit of the plugin’s configuration: disable unnecessary logging, ensure logs are stored securely (not publicly readable).
Review email logs for suspicious password-reset events for administrator accounts.
Check for unauthorized accounts created (administrator or editor roles).
Review plugin/theme files for added PHP shells/backdoors (e.g., eval(…), base64_decode, file_put_contents).
Examine outgoing mail logs (if available) for unusual patterns (mass password resets, unknown recipients).
Reset all administrator passwords, rotate secret keys (in wp-config.php: AUTH_KEY, SECURE_AUTH_KEY etc.).
Review wp_users, wp_usermeta for unexpected entries.
If backups exist, isolate affected site, rebuild from clean image, then reapply patches.
Consider forensic timeline of events: when did password reset occur, from which IP, which user triggered it.
Use a plugin-vulnerability scanner (e.g., WPScan) to detect outdated plugins and active known CVEs.
Monitor access logs for suspicious POST/GET requests to plugin routes (e.g., ones associated with Post SMTP).
Set up file-integrity monitoring (FIM) for wp-content/plugins and wp-uploads.
Implement least-privilege: Limit administrative logins, enforce strong 2FA for admins.
Disable WP admin via IP-whitelisting or WAF protection rules to reduce exposure.
This case underlines that while WordPress core is fairly well scrutinised, the plugin ecosystem remains a major vector for compromise. Third-party plugins often implement complex features (logging, SMTP, REST APIs) and may introduce flawed access control. Industry research confirms extensions and modules across CMSs are frequent sources of vulnerabilities.
Here, the attacker leveraged email logging as a pivot to takeover: retrieving logs → obtaining password-reset link → admin login. Email systems are often overlooked in web-app security but as this shows, can provide a “backdoor” into the site.
With active exploitation already underway, the risk window is narrow. Security teams must prioritise patching critical vulnerabilities. Even high-rating vulnerabilities may not be mitigated quickly due to plugin complexity, site owner inertia, or incompatibility concerns.
Regularly audit plugin versions, enable auto-updates where feasible for low-risk plugins.
Maintain an up-to-date inventory of installed plugins/themes, monitor for known CVEs.
Employ segmentation: restrict admin interfaces, disable unnecessary features (REST API endpoints, logging) when not required.
For clients or enterprise deployments (such as your engagements via ClearInfoSec / AnaData), include checks for SMTP/logging plugins, restrict their permissions and external access.
In summary, the discovery of CVE-2025-11833 in the Post SMTP plugin is a high-impact vulnerability that should serve as a red-flag for all security teams using WordPress. With over 400,000 active installations, the exploit isn’t hypothetical — it’s live, with confirmed in-the-wild attacks.
For teams like yours at AnaData Consulting and ClearInfoSec, which support cybersecurity services and assessments:
Take this incident as a case study to strengthen your plugin-risk assessment frameworks.
When advising clients, emphasise plugin inventory & monitoring, email system visibility, and least-privilege access.
Develop checklists or automated scans as part of your Web Application Penetration Testing (WAPT) engagements to identify vulnerable WordPress plugins, logging functionalities, and unusual email/reset flows.
Include this vulnerability in your red-teaming narrative: how an attacker walked through plugin mis-configuration, email log access, reset link theft, to full admin takeover.
Finally, for any WordPress-based site (be it client or internal), applying the patch is urgent. But patching alone isn’t enough — you also need to verify that no compromise occurred during the exposure window. And going forward, treat plugins with the same scrutiny you’d apply to any critical service.
Copyright © 2026 Clear Infosec. All Rights Reserved.