- Email: info@clearinfosec.com
- 1800 760 5656

A novel ransomware strain known as Charon has surfaced, specifically targeting critical infrastructure in the Middle East—namely, the public sector and aviation industry.

Analysts note that Charon exhibits unmistakable Advanced Persistent Threat (APT) hallmarks, such as DLL sideloading, process injection, and anti-EDR (Endpoint Detection & Response) evasion techniques, signaling a troubling shift in ransomware sophistication.
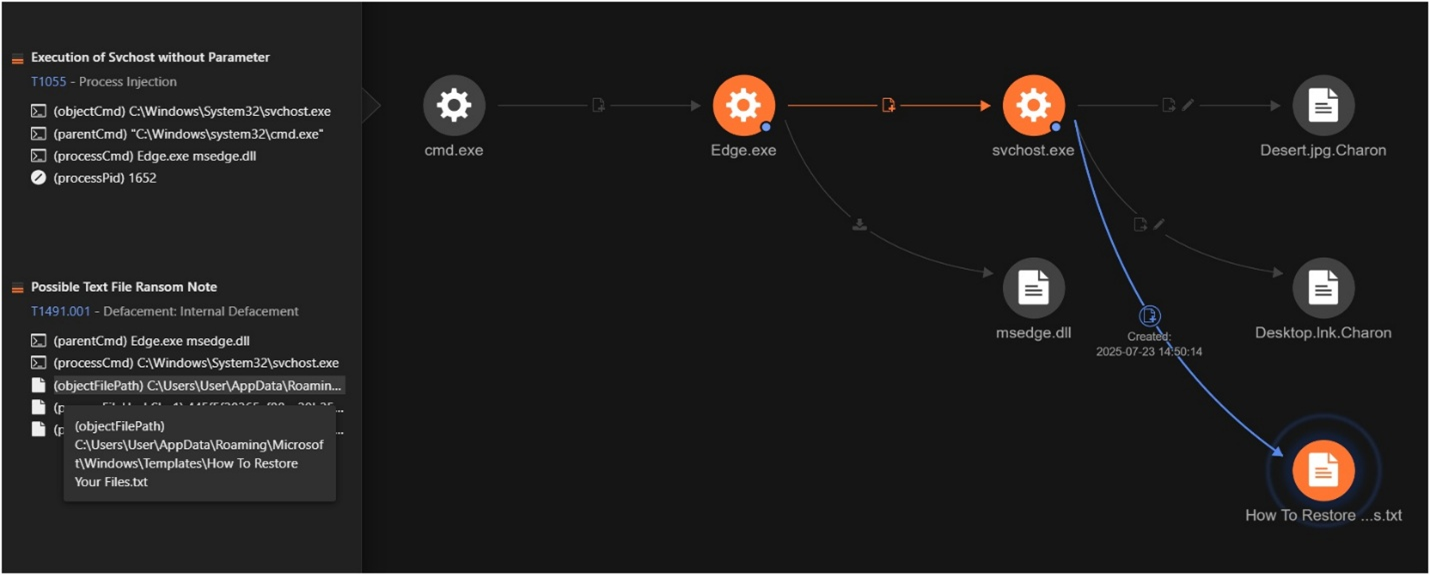
Abuse of Trusted Executables
The intrusion begins when attackers execute a legitimate Windows binary, Edge.exe (originally dubbed cookie_exporter.exe), to sideload a malicious DLL named msedge.dll—also known by its internal codename SWORDLDR.
Encrypted Multi-Stage Payload Loading
SWORDLDR loads a seemingly innocuous file DumpStack.log—initially missing from telemetry but later recovered—that contains encrypted shellcode. This shellcode undergoes multi-stage decryption: first revealing an intermediate payload with embedded configuration directives (such as targeting svchost.exe for injection), and then fully unpacking the Charon ransomware executable (PE).
Process Injection for Stealth
The decrypted payload is stealthily injected into a new svchost.exe process, enabling impersonation of a legitimate service to evade endpoint security mechanisms.
Disabling Defenses & Destroying Recovery Artifacts
Prior to encryption, Charon disables security services, corrupts or deletes shadow copies, and empties the Recycle Bin—actions aimed at thwarting recovery attempts.
Partial File Encryption for Speed
Leveraging a hybrid cryptographic method with Curve25519 ECC and ChaCha20, Charon employs a partial encryption strategy. Smaller files (≤ 64 KB) are fully encrypted; medium files have selective chunks encrypted; larger files are handled in evenly distributed chunks—an approach that balances speed and file disruption .
Network Propagation
Charon aggressively scans for and encrypts network shares—excluding ADMIN$—using NetShareEnum and WNetEnumResource APIs. It targets both mapped drives and UNC paths to maximize impact.
Dormant Anti-EDR Driver
Inside its data section, Charon contains a driver (e.g., WWC.sys), derived from the open-source Dark-Kill project, designed to disable EDR via a BYOVD (Bring Your Own Vulnerable Driver) tactic. Notably, this module remains inactive in current versions—likely reserved for future use.
Charon’s ransom notes are meticulously customized—they explicitly reference the victim organization by name and often include a list of encrypted files along with tailored payment instructions. This approach underscores a targeted rather than opportunistic modus operandi.
The technical execution of Charon—particularly the DLL sideloading workflow—mirrors what is seen in campaigns attributed to the China-linked APT group Earth Baxia (also known as APT41, Wicked Panda). Nonetheless, researchers stop short of definitive attribution. They outline three possibilities:
Direct involvement by Earth Baxia
A deliberate mimicry or false-flag operation
An independently developed but similar playbook
At present, there’s no conclusive infrastructure overlap to confirm attribution.
This merging of APT-level tactics with ransomware reflects a dangerous evolution—ransomware actors are adopting stealth, precision, and persistence, raising the stakes for defenders.
To counter this sophisticated threat, security teams should consider the following multilayered defenses:
Harden Execution Policies
Restrict which executables are permitted to load DLLs, especially in commonly abused directories. Monitor chains like Edge.exe → suspicious DLL → svchost.exe and flag unvalidated DLLs placed next to signed binaries.
Strengthen Endpoint Controls
Ensure that EDR and antivirus agents cannot be tampered with, disabled, or uninstalled by malicious actors.
Isolate Sensitive Resources
Restrict lateral movement by safeguarding network shares and disabling admin shares like ADMIN$. Use robust authentication controls for remote access.
Robust Backup Strategy
Maintain offline or immutable backups that can’t be compromised by malware. Regularly test backup restores and centralize backup permissions to trusted, monitored accounts.
Educate and Limit Privileges
Train staff to recognize phishing and suspicious payloads. Enforce least privilege principles to reduce the attack surface and limit the impact of a breach.
Proactive Detection via IOCs
Leverage threat intelligence platforms (e.g., Trend Vision One) to hunt for Charon-related indicators and deploy tailored detection rules.
Charon marks a worrying trajectory in ransomware evolution. By borrowing techniques from APT playbooks—such as stealthy DLL sideloading, multi-stage encryption, customized ransom demands, and latent anti-EDR capabilities—it blurs the line between cyber espionage and cyber extortion.
Organizations in high-risk sectors—especially within the Middle East—must urgently reevaluate their posture. The fusion of APT-level stealth and rapid destructive capability makes this a formidable adversary. Only an equally adaptive, layered defense strategy can hope to keep pace.
The Hacker News – Charon Ransomware Hits Middle East Critical Infrastructure
https://thehackernews.com/2025/08/charon-ransomware-hits-middle-east.html
Dark Reading – Charon Ransomware Uses APT-Style Tactics to Target Middle East
https://www.darkreading.com/threat-intelligence/charon-ransomware-apt-tactics
Copyright © 2026 Clear Infosec. All Rights Reserved.