- Email: info@clearinfosec.com
- 1800 760 5656
Clear InfoSec can help you identify, classify, prioritize, and eventually eliminate the exposures and weaknesses in your organization and compliment your cybersecurity operations. Our vulnerability assessments perform scan audits across internal and external network devices, servers, applications databases, and other assets that are hosted in both On-Prem and Cloud environments.
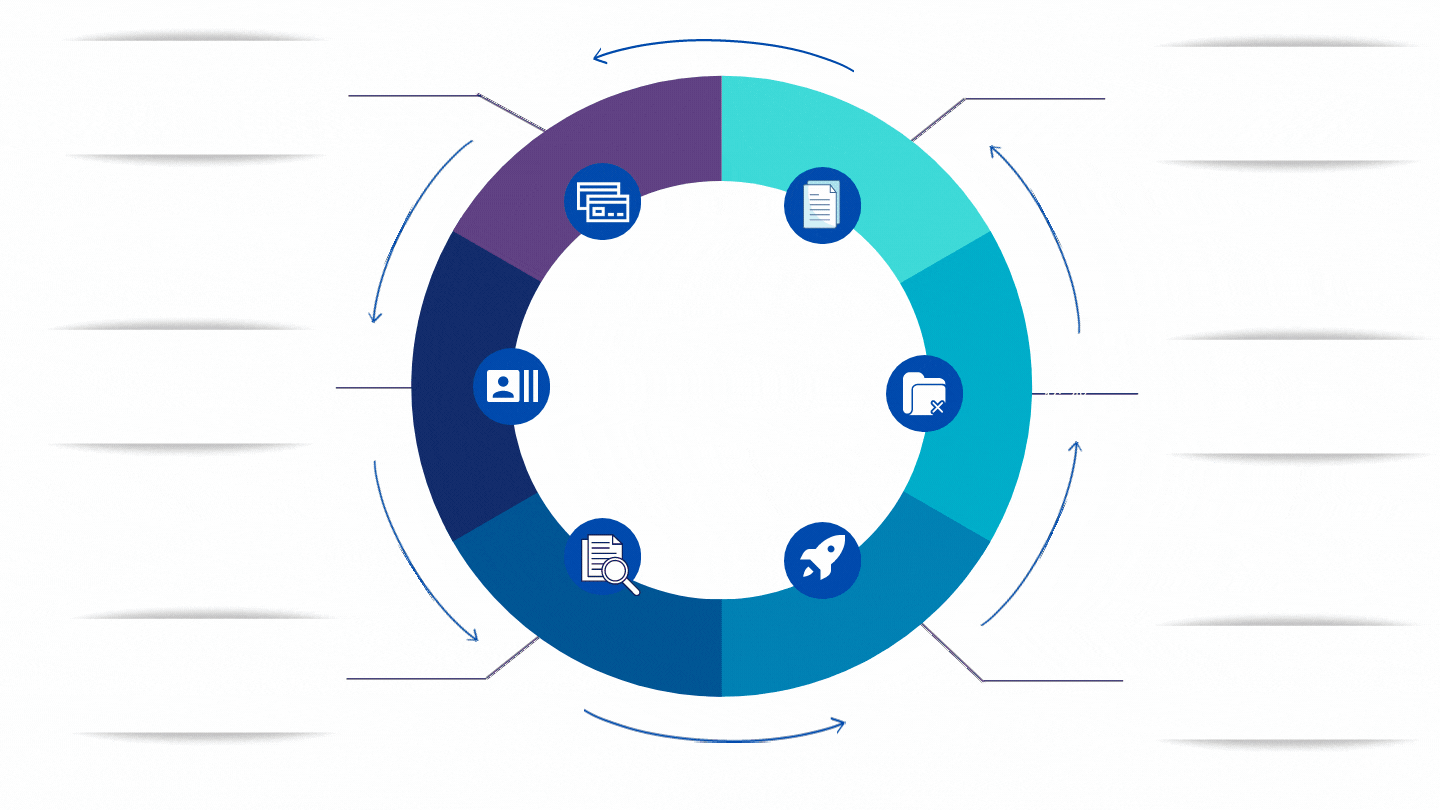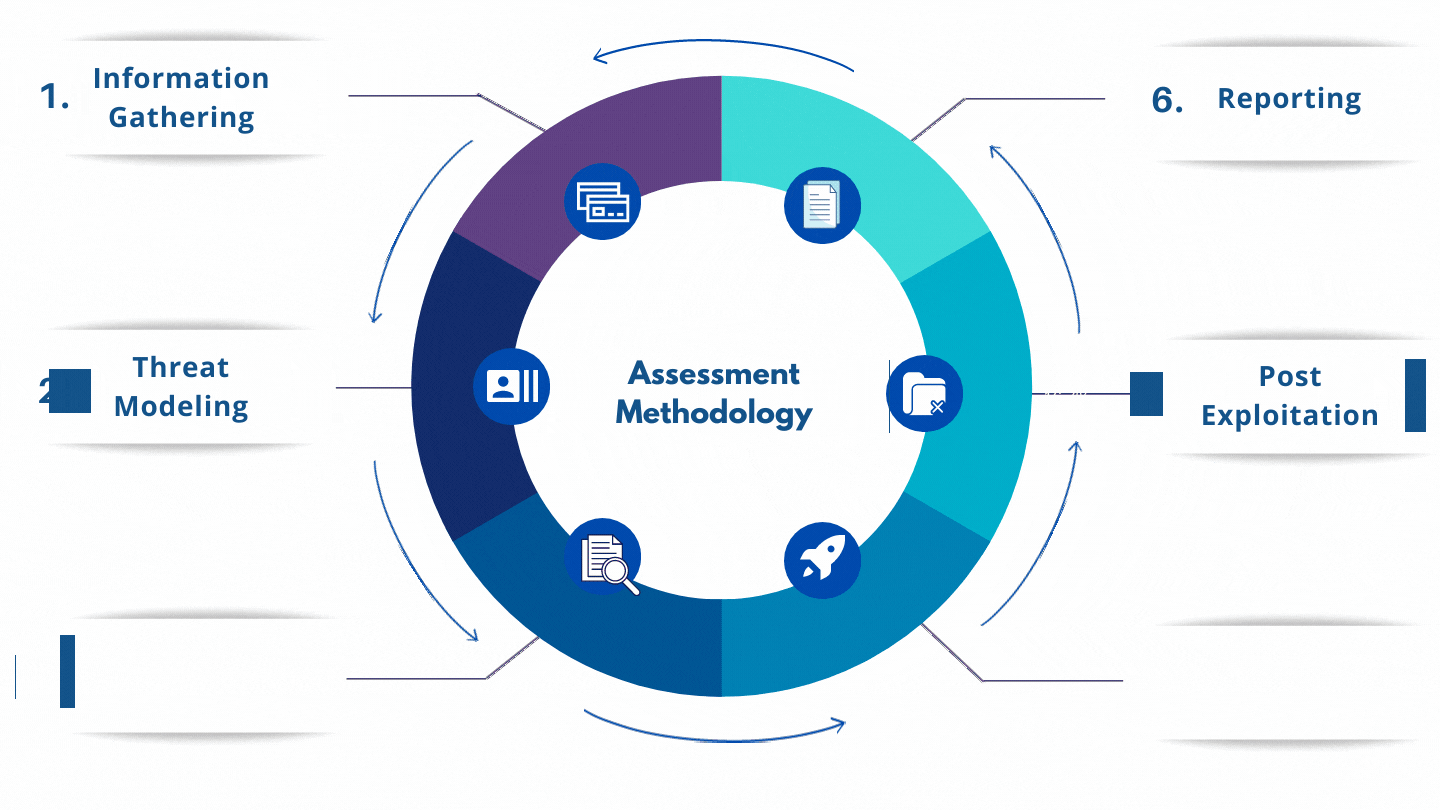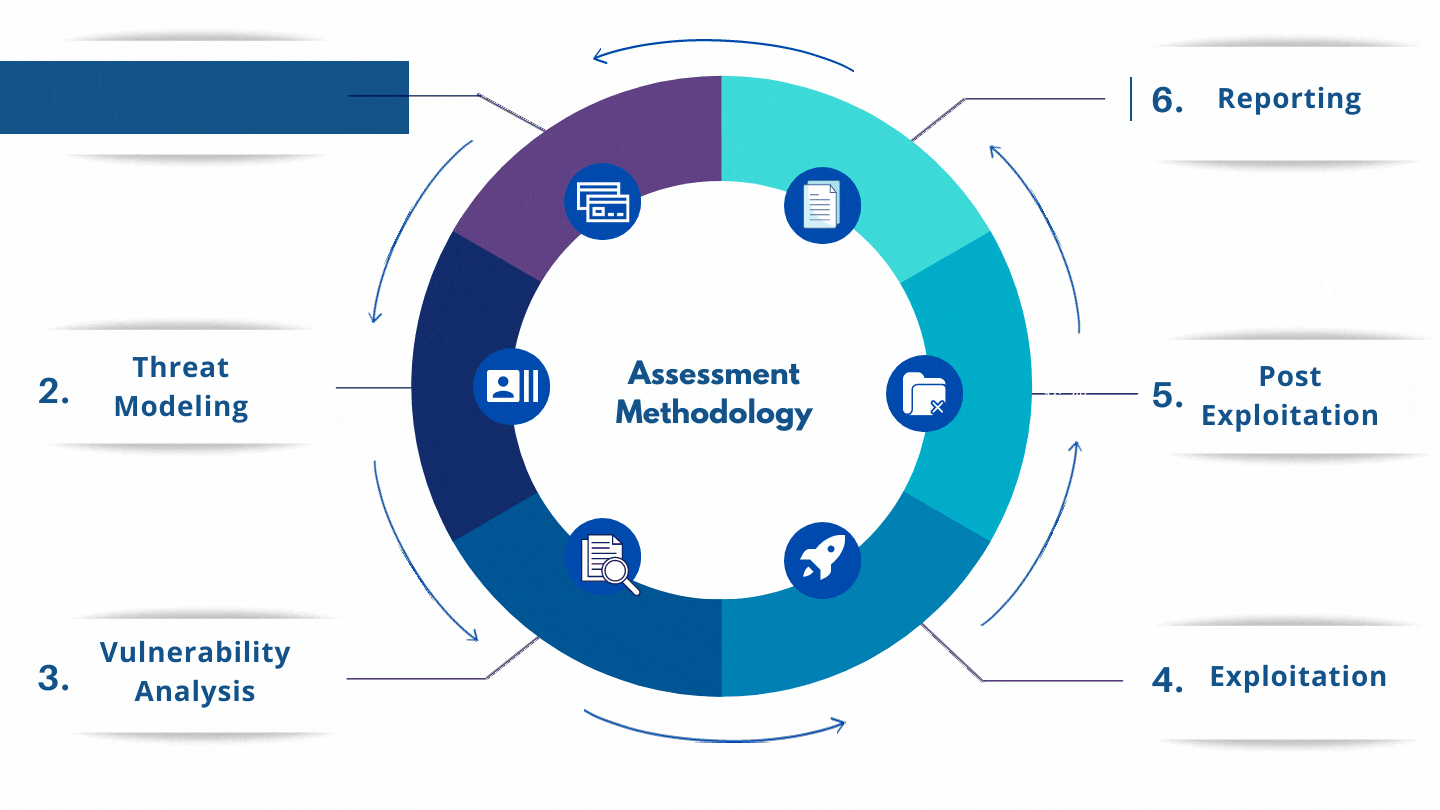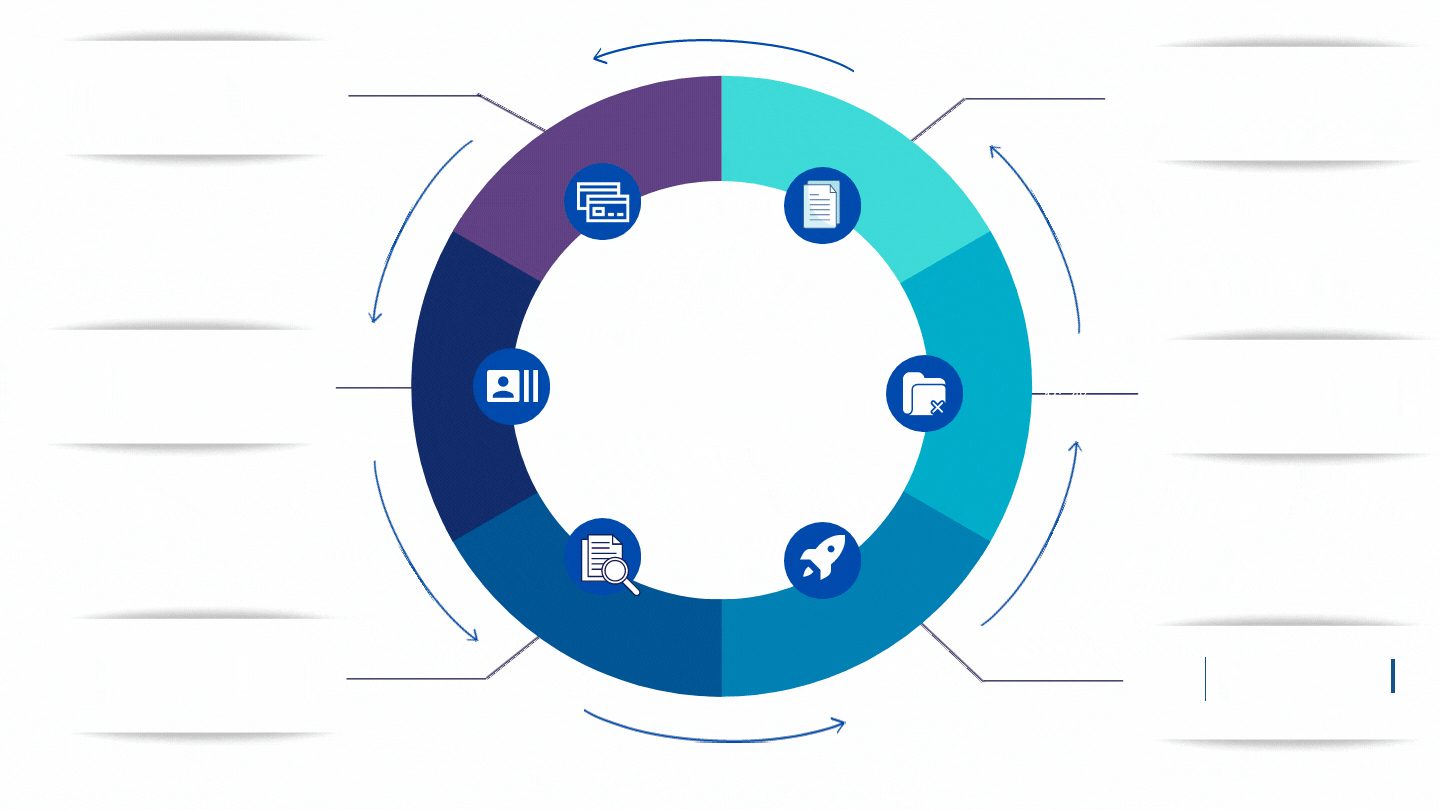
Review and Analyze your networks for security issues. The assessment may reveal network vulnerabilities and security flaws that could allow hackers access to your system. A network vulnerability assessment should also be performed on an ongoing basis as new threats arise and hackers find additional ways to break into systems.
An endpoint is any device that connects to your network. Each device can be an infection entry point. With thousands of vulnerabilities disclosed annually, you can’t patch all of them in your endpoint devices. Clear Infosec endpoint vulnerability assessments scans your endpoints to find and pinpoint critical ones requiring immediate attention.
Web apps were involved in 43% of data breaches, according to the 2020 Data Breach Investigation Report. Vulnerabilities in an application can act as an entry point to a bad actors and are targeted by them to steal sensitive data and more. With Clear Infosec, run a smart business by actively monitoring and testing for potential security holes.
Identify, Analyze and Prioritize vulnerabilities that exist in the software or system components that are present in your infrastructure -
Vulnerability assessments enables you to identify your vulnerabilities before they are exploited is crucial in today’s connected world. Find them before someone bad does.
“Find out your exposed assets and what needs to be addressed first.”
Clear Infosec provides a comprehensive vulnerability scan with the best team capable of handling leading technology plus high industry knowledge, to scan and report vulnerabilities for all your assets. With a strong understanding about the threat landscape and offensive techniques for of attackers, Clear Infosec Vulnerability Assessments stands unique by giving you the confidence and power you need to stand ahead of the emerging vulnerabilities and varying vulnerability landscape.
A strong Vulnerability Management Program is a core strategy every organization should have. It is never a “nice-to-have” option but a “must-have” thing. Many organizations are at different levels of cyber maturity journey. Many might be at the start are planning to start the journey. Wherever you are, we recommend vulnerability scanning at a regular interval and patching the critical ones immediately.
Clear Infosec partners with our clients to offer them with the best service they are in need of, with the most efficient tools available in the market. Our Vulnerability Assessment not only looks for unpatched systems, but checks for misconfigured systems, applications, unnecessary services and it even ensure that your IT assets are compliant with policy and standards like:
PCI DSS | HIPAA | FISMA | DISA STIGs | GLBA guidelines | OWASP | NIST
We understand that many organizations just wanted to test all their assets but once. If you are one of them, you are at the right place. Clear Infosec got you covered with a highly skilled security professionals and efficient tools needed to serve the purpose.
Many organizations will be at a higher cyber maturity level and want to do regular recurring scans, as they can be highly effective and helpful to find and patch the vulnerabilities right away. Clear Infosec can help you with setting up recurring vulnerability assessments
Situations might come up when some of the organizations wants to test just any of one or two of their assets like, the Internal networks, External networks, applications, etc. Well, Clear infosec still got your back and you can always count on our team.
These terms are mostly used inter changeably but defines different services. Vulnerability assessments helps you in finding and recording all your weakness. Penetration testing helps you in analysing each of your vulnerability found by every way to exploiting them. But legally and with permission.
To make maximum out of your vulnerability Management program, Vulnerability assessments and Penetration testing should be carried out together. One without the other is always incomplete.
Make your systems fortified with your trusted Information Security consultant
Copyright © 2026 Clear Infosec. All Rights Reserved.