- Email: info@clearinfosec.com
- 1800 760 5656

Phishing is a social engineering attack mostly used by cybercriminals to attack clients for their confidential information. In general, the common details that are commonly asked by cybercriminals are
The attacks may be concentrated on a specific user or the organization itself. Depending on that, the attacker will enquire about different information from the victim.
In phishing attacks, the criminals will disguise themselves as a trusted or genuine entity to cheat the victims open an email. By not observing carefully and trusting the attacker, the beneficiary was then tricked into providing confidential details or opening a suspicious weblink. This will help the attacker to create a starting point for his further attack. The weblink may install malware or attack servers, or collect data from the database and upload it to the attacker system.
These kinds of data thefts will be used to steal money or unapproved purchase of resources and more. With the organization’s confidential information, the attackers may understand the security protocols and prepare to bypass or break the security for more dangerous attacks. Or gain access to more privileged information, which may destroy the foundation of the organization itself.
If an organization undergoes such an attack, the financial losses will be very severe. The loss of assets, reputation may reduce the company’s market share and may go bankrupt.
Depending on the scale of the phishing attack, it may target an individual for money or a severe security incident on a business organization. So it is recommended to take phishing mails as serious attacks and report them to the cybersecurity team.
Phishing attack starts when the user receives phishing mail but only when the user responds to that subjective mail does the true attacks start. Some of the general actions required in phishing emails are opening an attachment, Providing the details in a form, clicking on the links, sending money to a charity organization (not the real one), and more.
Some of the examples of email phishing are given below.
Usually, these emails look like they come from someone the user knows, like a supervisor or chief or team leader like that and ask the user to urgently send some funds, transfer money or provide bank details for their salary account.
If you receive mail like that, always be cautious and confirm with the corresponding person with the contact details available from sources other than the one specified in that mail.
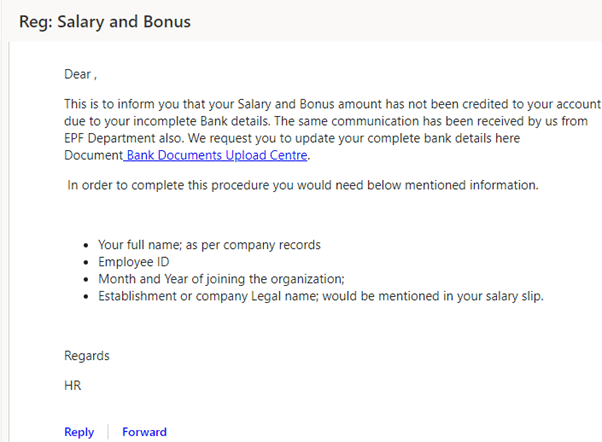
The mail may contain some details like you are selected for a specified position in a reputed company, but you have to send a demand draft of certain money for the application process. As soon as the DD is obtained, we will send you the appointment order.
They may also send a form and ask for your complete details for a job application.
It is always recommended to confirm the job you applied for, the company name, and the company logo before responding to emails like these.
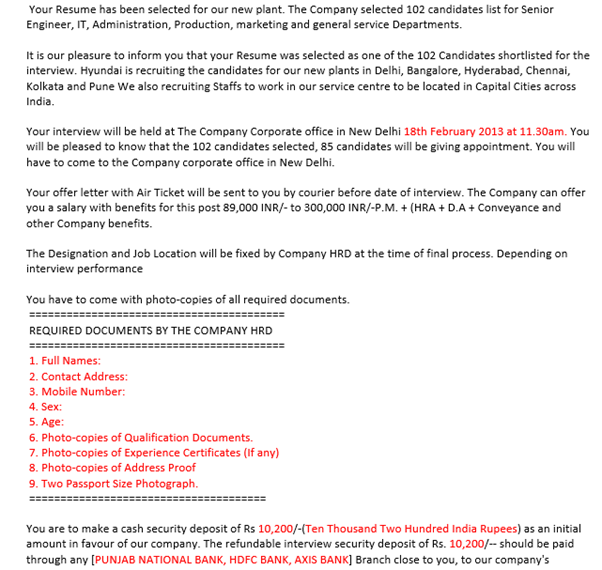
The attacker may send a mail like a genuine person from any social network site and ask for your details.
The mail may inform you there may be some discrepancies in your login or a login attempt in another system. And ask you to confirm by giving your profile details.
The criminal may send a fake invoice showing you have paid a certain amount for buying their services. For example, you have paid 100$ to avail iTunes service. At the end of the mail, they will specify if we didn’t buy that service; click the link and provide details for the refund.
This kind of mail is sent to ignite greed or make the user think they will get extra money for free. Then the user will give their details to get a refund without knowing they provided confidential details to the hacker who is taking all the money from your bank account with their details.
There may also be mail like Remainder: Invoice or Important: Invoice and asks you to download the attachment. Be cautious of this kind of mail and report to the cybersecurity in your organization.
The hacker will pretend like they are having an orphanage or other charity organization and request money. They may provide a believable story like a kid who needs lots of money for an operation, making the user feel pity and donate the money.
If you receive any such emails, kindly confirm the organization’s authentication or the story provided, then donate the money.
We may receive mail describing that our account has been suspended due to some illicit activities or log in from different places like that. And ask as to provide our details in a link they would have sent along with the mail. This kind of mail may come from the bank or social media accounts.
Believing this mail and without checking if we proceed with sending our details, the hacker may very easily claim our account ownership.
The email will have surveys to collect information from the user. These surveys can appear as display ads on websites and in the news feed, and more. The most important thing to note is that no legitimate organization will survey by asking about your credentials.
You may receive a simple mail from someone like a higher authority in your organization. For example, someone under your organization’s higher official name will ask you to mail your mobile number to discuss urgent needs like that.
The hacker may have got the email from any dating web and started sending mail. After a while, the hacker may ask for money from the user or ask serious questions about the user. These questions are asked to understand the security questions the user may have given for password retrieval and more. If not careful, the romance scams broke not only the bank vault but also the heart.
The mail we receive may contain details such as our mail id may be won a lottery among many thousands of mail id. They will ask for our details to send the prize amount and our details for the same.
It may come as attachments or links or in many forms. The ultimate goal of the scam is to get the details of the user.
Having some knowledge about the email header may help to avoid phishing attacks. Can check this blog for more about email header analysis.
The genuine company logos have distinct marks, which cannot be completely duplicated or won’t be duplicated. If the user receives any mail from an organization, it is recommended to check the organization’s logo is correct.
The mail received from the legitimate company will have proper grammar and no typo errors. In most of the scam mail, there might be many spelling mistakes.
If the mail contains a hyperlink, it is better to hover the mouse pointer above it to see the link’s address. If the specified address in the mail and the link’s address are not the same, there might be a problem with the account.
If the mail is received from an unknown sender or you have some doubts about the sender, it is better to use a virtual machine to download attachments. And use the tools available to examine whether the attachment contains any suspicious file. For more details, check this blog https://clearinfosec.com/pdf-malware-ioc-extraction-2/
It is recommended that the cybersecurity team in the organization create awareness about phishing mail by conducting webinars or meetings or blogs etc.
Copyright © 2025 Clear Infosec. All Rights Reserved.