- Email: info@clearinfosec.com
- 1800 760 5656
As technology is evolving to high grades, Malwares are also substantially evolving to unprecedent extent.
The truth is that cyber criminals nowadays use much more sophisticated, agile and stealthy malwares that prove to be effective and successful. These Malwares makes more challenging to build a stronger defense against them.
Malwares are evolving at a rapid pace because of mastering the art of evasion. Thus, traditional antivirus engines find it difficult to detect attacks in the first stages. Malware is getting bigger and bigger. Malware developing is a big billion business and growing more.
Paul Edmunds, Head of Technology at the National Crime Agency’s National Cyber Crime Unit (NCCU) states that:
It’s really important to understand the impact that malware has. It’s a massive criminal enabler that underlines most cybercrime. It’s an infrastructure that’s used for compromising devices to conduct most of the prominent attacks that you see.
In 2018, the cost of the average data breach increased by 6.4% to $3.86 million. This is simply the average across the entire world in the US, it’s $7.91 million. In 2015, the global cost of malware was an already staggering $500 billion. In just a short time, however, the economic toll of cybercrime has grown fourfold, to $2 trillion USD. At the current trajectory, the total cost will reach $6 trillion by 2021.
Fileless malware is one of its kind and current trend of attack which uses more advanced technology. Fileless malware aka non-malware or fileless infection is a method where it infects the built-in tools of the operating system. There is no need of installing any malicious executable to infect thus there is no signature for antivirus software to detect. This mechanism makes fileless attacks so dangerous as it is easy to evade AV.
Fileless attacks are considered evasive in nature because of a few characteristics:
Fileless malware targets legitimate program like Powershell and WMI (Windows Management Instrumentation). This makes it more challenging for security programs and analysts to catch the infection. In the case of PowerShell attacks, for instance, fileless malware embeds malicious scripts into legitimate PowerShell scripts essentially working as it runs like a normal process.
Fileless malware leverages what threat actors call “living off the land,” meaning the malware uses code that already exists on the average Windows computer.
PowerShell, Windows Management Instrumentation (WMI), Visual Basic (VB), Windows Registry keys that have actionable data, the .NET framework, etc. Malware doesn’t have to drop a file to use these programs for bad intentions.

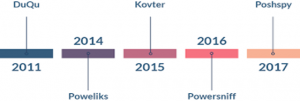
Some of the widely known fileless malwares are listed below,
Now, fileless attacks are not a new thing. One example is the Lehigh Virus
memory-resident malware which was wild over 15 years ago. It fills an unused portion of the of the host file’s code in its stack space, causing no increase in the host’s size. It can infect another COMMAND.COM file if a DOS disk is inserted while the virus is in memory.
As technology improved, malware such as Poweliks used a “NULL” Runkey which makes the content invisible in the registry to run JavaScript and used PowerShell to run an encoded script hidden in the registry. The payload was stored in the registry, retrieving, decoding, and executing during runtime only.
Duqu 2.0 is a highly sophisticated Fileless malware platform exploiting up to three zero-day vulnerabilities which are listed below:
with infections linked to the P5+1 events and venues for high level meetings between world leaders. Kaspersky discovered the malware, and Symantec confirmed those findings. The malware is a variant of Duqu, and Duqu is a variant of Stuxnet. Kaspersky first detected it revealed that among its targets there were entities linked to the negotiations about Iran’s nuclear deal and IT security firms. Duqu 2.0 targeted several Western organizations and entities operating Asia and in the Middle East.
In 2017, Kaspersky Labs described an unnamed incident where adversaries stored Meterpreter-based malicious code solely in memory. The only file system artifacts were legitimate netsh (to tunnel malicious network traffic).
It was POSHSPY, the which used Windows Management Instrumentation (WMI) capabilities of the OS to maintain persistence and relied on PowerShell for its payload. Poshspy had the ability to download executable files, which it would save to the file system.
The threat of fileless malware and its potential to harm organizations is growing.
Ensure Strong Security policies:
To defend fileless malware make sure your Windows computers are patched and up to date. Because if one of the first tenets of threat actors is taking advantage of unpatched systems the you are vulnerable to the attack. The spread of EternalBlue illustrated this well as the patch was available for more than a month before the exploit was launched.
Most fileless campaigns begin their life with a simple phishing email, so it is important to try to nip these entry points quickly. So Be careful on what you click and open.
Understand Your Access Rights and Privileges
A common attack method is escalating privileges as malware moves around the network. A Malware can issue commands for reverse Domain Name System (DNS) queries, enumerate access control lists on any network share and find members of a particular domain group. This means one of the more basic controls for any malware is to restrict administrator rights to the minimum number of systems.
Copyright © 2025 Clear Infosec. All Rights Reserved.