- Email: info@clearinfosec.com
- 1800 760 5656
68% of companies say the Red Team beats blue teaming.
Clear Infosec integrates cutting-edge technologies with strong ecosystem alliances that provide you with a wide range of customizable solutions. We enable you to face your challenges and generate measurable value by defining new markets.
Red Team Attack Simulation
Every day, Attack tactics, techniques, and procedures (TTP) are perpetually evolving. It is time for you to know how to identify, stop and prevent a breach. Of all the security assessments, Adversary Simulation can be the most efficient way to figure out how prepared your systems are in facing a real-world attack.
Test your technology and people to check the effectiveness of your response plan
Learn about the hidden vulnerabilities you have in your infrastructure and workforce
See how easily your assets and workforce can be manipulated and classify them
Treat the critical vulnerabilities found and mitigate the risk of having a real attack
With various targeted attack simulations, we help you set up the controls and address gaps
Understand your weakness with and invest in what needs to be done immediately
Even organizations with robust security controls and procedures may not be able to detect and contain a breach in a timely manner. Until and unless you are faced with a real-world attack, you would not know that.
With Clear Infosec, find and fill gaps in your response team, controls, and processes to minimize the damage when a breach occurs.
“With Clear Infosec, test and upgrade your security posture”
STAY PREPARED
With Clear Infosec, put your controls and teams to the test. We test the interaction between your people, processes, and technologies. Test all your controls and see for yourself that it does what you exactly want it to do. With the best team of security experts, we enable you to strengthen your security posture.
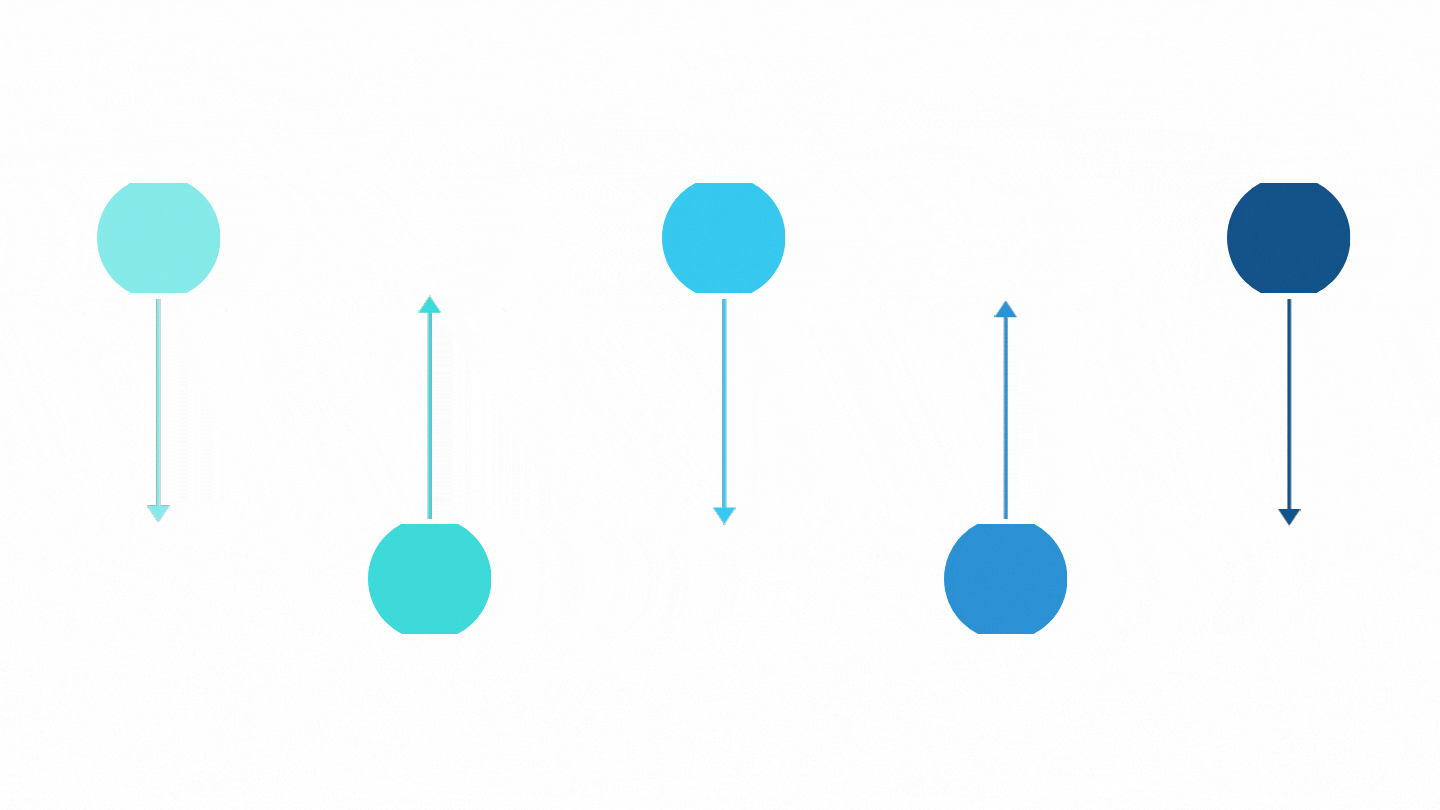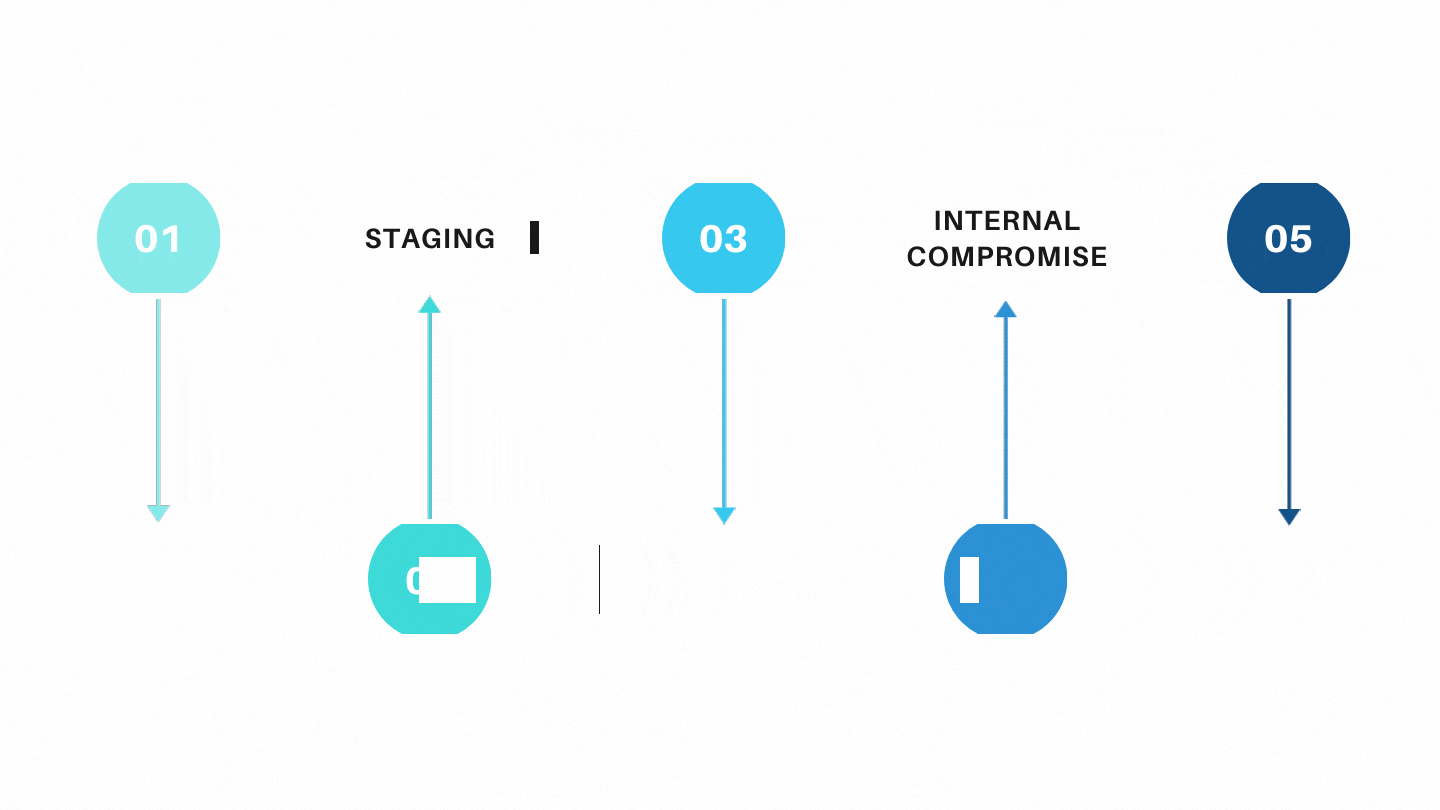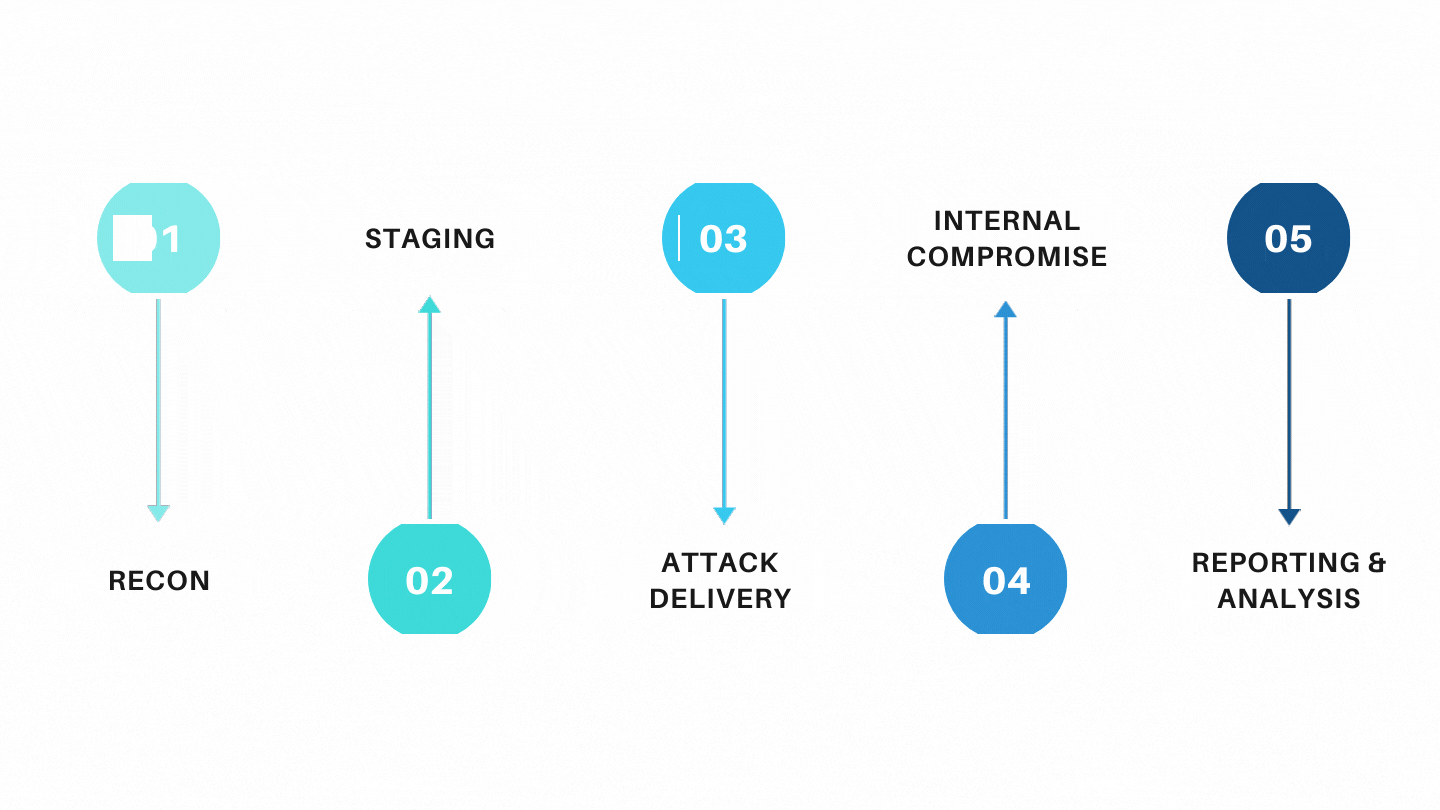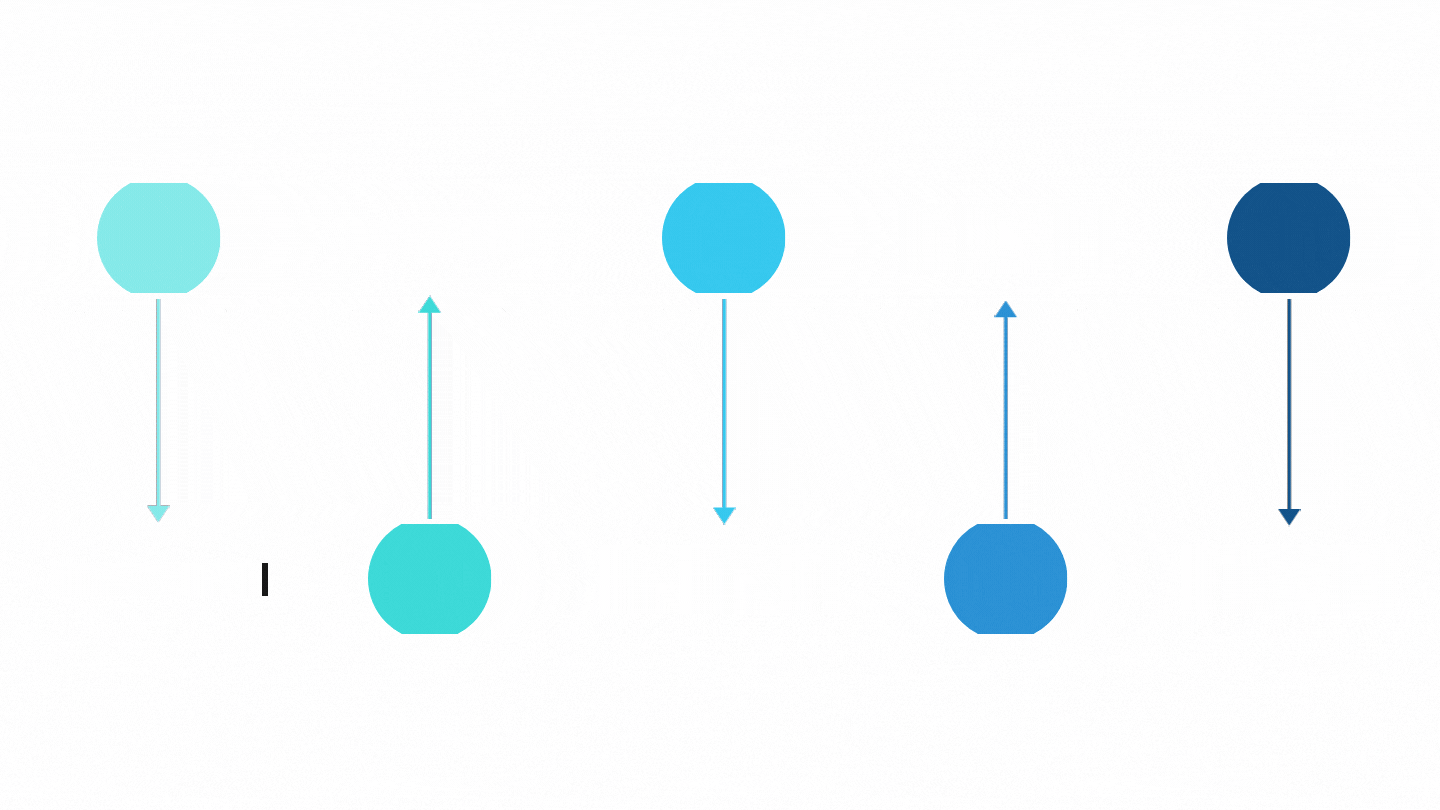
Our red team plays the role of the attacker, employing hacker techniques and tools to evade detection and test the internal security team's defense readiness. This includes not only testing for vulnerabilities in the technology but also in the people who work for the company. Skilled attackers can combine different vulnerabilities in your systems, both small and big, to carry on a potential cyber-attack.
The Red Team Exercise exposes security flaws by penetrating your networks, assessing your processes, and putting your security teams' defensive capabilities to the test in every way possible. This enables you to take the necessary steps to update your security layers. Know your flaws and quantify risk factors that can lead to a breach in the future.
Customized phishing, vishing, Quid pro quo & baiting, and physical tricks to test your workforce. Our team of highly skilled attackers tries out every possible way to penetrate your workforce to get our hands on the sensitive systems.
Identify and prioritize existing vulnerabilities and start remediating the exposed ones. Our vulnerability assessments perform scan audits across internal and external network devices, servers, applications databases, and other assets that are hosted in both On-Prem and Cloud environments.
Test your applications, networks, and hardware to uncover and fix vulnerabilities. Find the
vulnerabilities that can be exploited and figure out the security posture of your company. Build confidence with Clear Infosec Penetration Testing
Breaches can still happen no matter how strong you think your security systems are. We also have a forensic investigation unit deployed for activities including data breach analysis and data discovery. Give us a call today to find out how you can improve your cyber security posture and infosec approach.
Copyright © 2025 Clear Infosec. All Rights Reserved.