- Email: info@clearinfosec.com
- 1800 760 5656
Since its introduction in 1999, Active Directory (AD) has become a critical component for around 90% of the Fortune 1000 companies’ IT infrastructure. As such, understanding Active Directory can significantly aid security professionals in expanding their attack surface during internal network VAPT and red teaming engagements. This blog will explain what Active Directory is and how it works.
Active Directory is an identity management solution that stores information about an organization’s resources on a network. Resources include hardware like computers and printers, and software like applications and shared files. It also stores user information such as usernames, passwords, and much more.
It helps manage the authentication and authorization of users and devices in a Windows domain network. Simply put, it controls who has access to what resources, ensuring security and efficiency. For example, it can organize users into groups, set policies for those groups, and manage permissions for accessing different resources.
Microsoft introduced also Azure Active Directory (Azure AD) to support cloud-hosted infrastructures. Azure AD Connect bridges on-premises AD with cloud-hosted Azure AD, providing a seamless integration between local and cloud resources.
To understand how Active Directory works, we can look at its components in three main categories: core components, server roles and logical hierarchy.
Core components – Essential elements required for AD to function.
Logical hierarchy – Organized groupings of information stored in AD.
Server Roles – Roles that instruct servers to perform a specific task within the Active Directory.
A directory serves as a hierarchical structure for storing information about various objects on the network. Active Directory Domain Services (AD DS) functions as the directory service responsible for managing this data. It offers methods for storing directory data into logical hierarchies, facilitating efficient management and retrieval of information across the network.
A lightweight version of AD DS, without the extra infrastructure-related features, enabling it to function as a stand-alone directory service without the need for domain integration. This independence allows for greater flexibility and efficiency in managing directory data for specific application needs.
While Active Directory ensures smooth access to internal resources, AD FS takes it a step further by extending this capability to external applications. With AD FS, organizations can implement single sign-on for all applications located outside of the network.
AD RMS allows organizations to create and enforce policies for accessing and using documents, emails, and other types of digital content. AD RMS encrypts content and controls access based on permissions set by administrators, ensuring that only authorized users can view, modify, or share protected information.
Active Directory Certificate Services (AD CS) is a Windows server role that specializes in issuing digital certificates. These certificates serve various purposes, such as encrypting and digitally signing documents and messages. Additionally, AD CS facilitates the authentication of computer, user, or device accounts within a network using these certificates.
A domain controller is a server that runs AD DS and is tasked with carrying out the primary function of Active Directory, which is to manage resources and regulate their access based on the rules configured in response to requests from other devices or users on the network.
The storage location where AD DS holds all its information is commonly referred to as the “Data Store” or “Directory”. This data store is automatically created within the “%SystemRoot%\NTDS” folder on every domain controller, and it’s known as the “ntds.dit” file. Access to this data store is restricted only to the domain controller processes.
Logical components are the organized groupings of information stored in Active Directory. Directory objects like users and resources are organized into manageable groups, ensuring efficient organization and access.
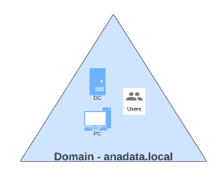
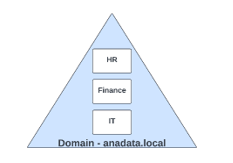
An Active Directory tree consists of multiple domains starting from a central root and extending into child domains. These domains within the tree collectively share a common namespace, allowing for the seamless authentication and management of users, computers, and resources across the entire tree.
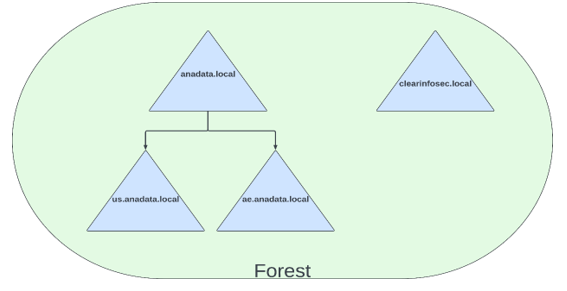
In an Active Directory environment, multiple domains are commonly structured hierarchically, with each domain maintaining its own set of resources. However, direct access to resources across domains isn’t universal. A “Trust” creates a connection between domains, enabling users in one domain to access resources located in another domain.
Trusts can be classified into two categories – Directional Trust and Transitive/Non-Transitive Trust.
Further, the sub classifications
A one-way trust allows authentication and authorization to flow in only one direction. For example, Domain A trusts Domain B, allowing users in Domain B to access resources in Domain A, but not vice versa.
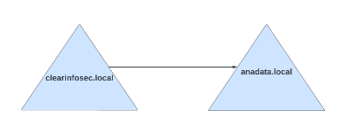
In a two-way trust, authentication and authorization can flow in both directions between two domains. Domain A trusts Domain B, and Domain B trusts Domain A, enabling users in both domains to access resources in each other’s domains.

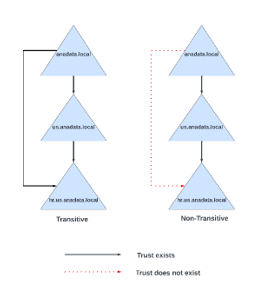
The subclassifications of trust types, such as directional trusts (one-way and two-way) and transitive/non-transitive trusts, can be combined in various ways to create additional trust relationships. For instance, a one-way trust can be established between two domains to allow resources from one domain to be accessed by users in another domain. This trust relationship can further be extended by configuring it as transitive, enabling access to resources across multiple domains within the forest.
A bidirectional, transitive trust, the parent-child trust forms automatically upon adding a child domain to a parent domain. As new child domains are introduced, the trust path flows upwards through the domain hierarchy.
2. Tree-Root Trust
Similar to parent-child trusts, tree-root trusts are bidirectional and transitive. Automatically established upon creating a new domain tree within a forest, they link the new domain tree with all existing domain trees. For instance, if domain A has child domains B and C within forest X, and a new domain D with child domains E and F is created under the same forest X, domains D, E, and F will be automatically trusted by domains A, B, and C.
3. Shortcut Trust
A one-way, transitive trust established manually, shortcut trusts streamline authentication between two domains by circumventing hierarchical trusts like parent-child or forest-root trusts, thus simplifying the authentication process.
4. External Trust
Manually created, an external trust is a one-way, non-transitive trust with an external domain beyond the trusting domain’s forest.
5. Forest Trust
Transitive in nature, forest trusts can be one-way or two-way and occur between forests, requiring manual configuration. When one forest extends trust to another, all domains within both forests reciprocally trust each other.
6. Realm Trust
A trust relationship established between an Active Directory domain and a non-Windows Kerberos realm, such as Unix or MIT Kerberos realms, facilitating cross-realm authentication and resource access. Realm trusts are typically one-way, though a two-way trust can be achieved by creating trust in the reverse direction.
These trust relationships provide administrators with flexible options for managing access and collaboration within and across organizational boundaries in an Active Directory environment.
In short, this blog post has given us an overview of Active Directory and its main parts. In our next post, we’ll break down how Kerberos, an authentication protocol, operates. This will help us understand different attacks that can target Active Directory. Stay tuned for more insights!
Copyright © 2026 Clear Infosec. All Rights Reserved.