- Email: info@clearinfosec.com
- 1800 760 5656

I am here with a blog on the MITRE ATT&CK because it has gained a lot of attention and popularity in recent years.
ATT&CK is a framework developed by MITRE. It is globally accessible knowledge base of adversary tactics and techniques based on real-world observations.
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
It is a way of telling a story, a story about how an attacker is going to progress through their mission, what steps they are going to take or what steps are possible for them to take in order to execute a successful attack.
It does 2 things:
Because, it is based on real-world observations of past attacks, it gives us detailed insights on what adversaries have done in past to conduct attack, and on what adversaries are likely doing pre and post attack.
Why ATT&CK was created:
It is like an encyclopedia which has all the information’s about different activities of attackers.
ATT&CK is open and available to any person or organization for use at no charge.
The main reason why ATT&CK was created and it became so popular in short time in the industry is that it provides same language for all the teams of an organization. It’s also a great starting point to get multiple people and teams on the same page, using the same terminology for security testing and mitigation as it provides specific name and numbers for different attack techniques.
MITRE ATT&CK can help us achieve Difficult task of detecting TTPs:
ATT&CK focuses on TTPs: Tactics, Techniques, and procedures
Let’s understand why it focuses on TTPs using pyramid of pain shown below:
The point of detecting this indicator is to respond to them by analyzing it and stopping adversaries at that level. It depends on how quickly we can deny adversaries using one of those indicators when they are trying to attack us.
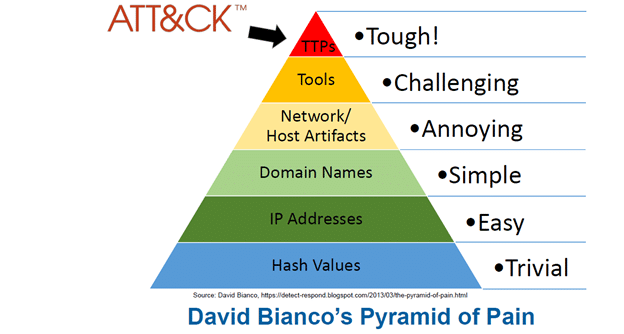
It shows 6 different indicators. The point of detecting this indicator is to respond to them by analyzing it and stopping adversaries at that level. It depends on how quickly we can deny adversaries using one of those indicators when they are trying to attack us.
This pyramid shows what is easy for adversaries to do and what is most difficult for adversaries to do. So here at the apex we can see
TTPs : Tactics, Techniques and procedures
When we detect and respond at this level, we are operating directly on adversary behaviors. It is the most difficult thing for an adversary to change in their behaviors and pattern of carrying an attack. So instead of figuring out which tool they are using, first if we can get to know their TTPs, we can secure our systems far better and if we are already under attack, we can detect it in early stage and mitigate those.
MITRE ATT&CK Framework can help us figure out those TTPs very quickly and with that,
If we can respond to adversary TTPs quickly enough, we force them to do the most difficult and time-consuming thing to do which is learning new behaviors.
MITRE ATT&CK Matrices:
It is Free, Open, globally accessed tool. You can access it on: https://attack.mitre.org/
It contains 3 Matrix:
Enterprise it the most popular one. The Matrix contains information for the following platforms: Windows, macOS, Linux, PRE, Azure AD, Office 365, Google Workspace, SaaS, IaaS, Network, Containers.
They are displayed in matrices that are arranged by attack stages, from Reconnaissance and initial system access to Privilege escalation, Command and Control to the Impact of the attack.
It is constantly being updated but at the time of writing this blog it has:
Enterprise Tactics: 14
Enterprise Techniques: 185
Enterprise Sub-techniques: 367
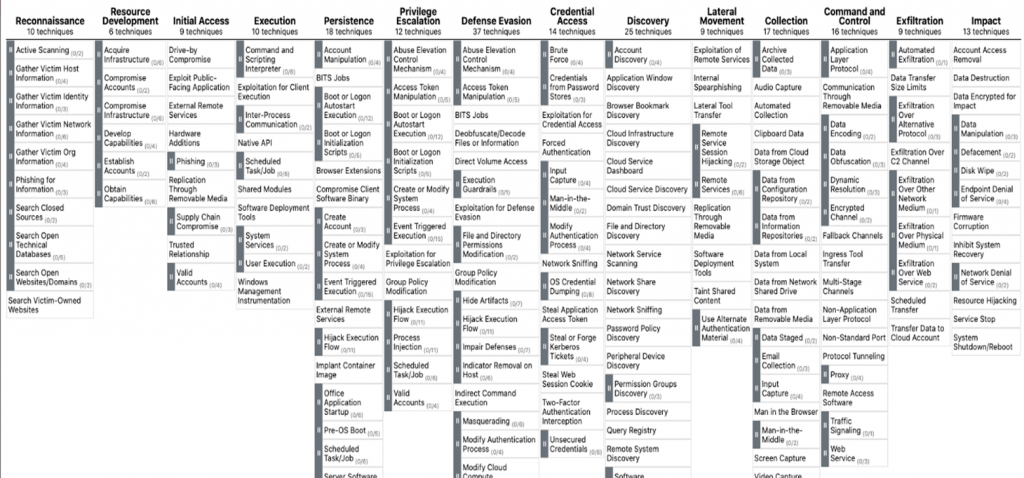
Tactics and techniques is a way of analyzing real-world cyberattacks.
Top Row is Tactics : Adversaries Technical goals
Under each of those Techniques : How the adversary achieve their goal
Here the techniques are most important because it is a specific single step taken by attacker to exploit any system. And if we can detect it early enough, we can prevent future attacks or stop the one which is currently happening. For that ATT&CK provides many details about each technique including a description, examples, references, and suggestions for mitigation and detection.
MITRE ATT&CK VS Lockheed Martin’s Cyber Kill Chain:
After looking at the Matrix, some of us might remember Lockheed Martin’s Cyber Kill Chain. They both resemble each other because they define the steps an attacker uses to achieve their goal. So let’s compare them:
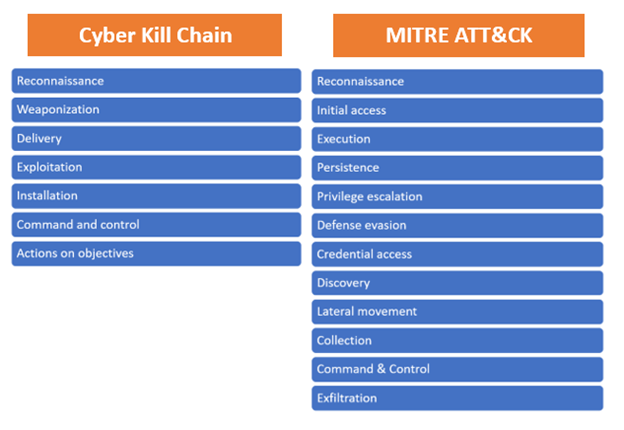
As we can see, both follow the same pattern, but ATT&CK provides us with more detailed techniques and sub-techniques.
We can say that they are complementary. ATT&CK sits at a lower level of definition to describe adversary behavior than the Cyber Kill Chain. ATT&CK Tactics may not be followed by adversary in the same order, because the goal of an adversary changes throughout an operation and also based on type of attack, whereas the Cyber Kill Chain have all the phases are in ordered manner to describe high-level adversary objectives.
But the Cyber Kill Chain does not go deep into what to do after an attacker has broken into your network successfully, and all those different techniques which ATT&CK Matrix has.
So, we can say that Cyber kill chain has several security gaps because it has not been modified since its created, but MITRE ATT&CK Framework has filled in all of those gapes and the main advantage is, it’s constantly being updated and expanded by the community.
Different Enterprise ATT&CK Tactics:
Now that we’ve covered the basics of ATT&CK framework you can look forward to future blog post where I will write about how you can start using ATT&CK for Cyber Threat Intelligence (CTI).
Thanks for reading.
Copyright © 2026 Clear Infosec. All Rights Reserved.